Posts on this page:
- Configure IIS Web Administration to use centralized SSL certificate
- Get certificate template effective permissions with PowerShell
- Backup Certification Authority with PowerShell and CryptoAPI (part 2)
- Backup Certification Authority with PowerShell and CryptoAPI (part 1)
- String comparison in Certification Authority database queries
Many of you use IIS web servers in corporate network for various purposes, for example, to host internal/external web site, ADCS web services, OCSP, WSUS and this list is very long. It is common to manage them all from a centralized place, for example, from web server administrator’s computer. In other words, IIS servers are not managed directly from console.
The problem
By default IIS do not allow remote administration, you have to enable it by starting (and, likely, setting start type to Automatic) Web Management Service (WMSVC). Ok, you started the service on a web server and attempt to connect to the server from remote IIS management console:
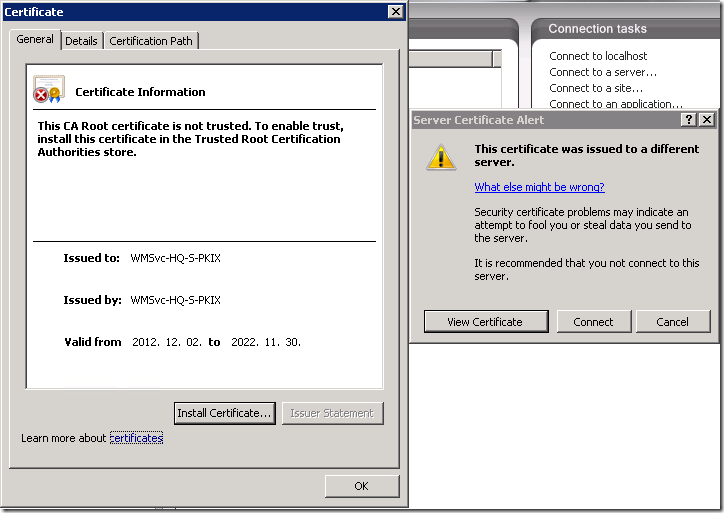
Read more →
In this article I will show the techniques used to determine effective permissions for a user or computer account on a certificate template.
The problem
When you open certificate template in Certificate Templates MMC snap-in (certtmpl.msc) or in ADSI Editor (adsiedit.msc) and switch to Security tab, you will see the following:
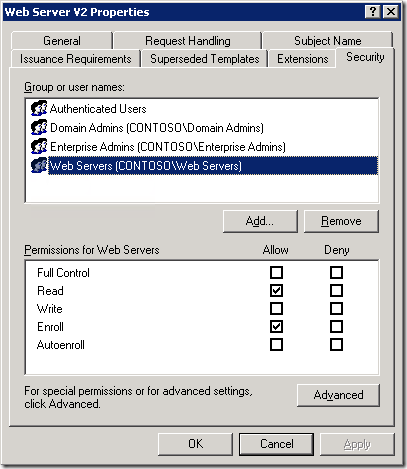
When you click Advanced button, you won’t see Effective Permissions tab like in NTFS permission editor:
Read more →
Hello, everyone! Today I’m feeling good as Flyers eventually managed more than 2 goals per game and Lecavalier set up a hat-trick against Isles. Big WIN! So, I’ll continue Certification Authority backup API coverage and usage in PowerShell.
In the previous post we learned what functions are used for CA backup, their sequence and ended with CA database location retrieval. Today we will continue the backup process and today’s post will cover:
- Database backup
- Identification of log files to be backed up
- Log file backup
- CA Configuration backup
- CA key backup
Database file backup
Let’s move forward. We have a $DBPaths variable that holds CA database location. Note that database location is specified in an UNC form (\\serverNameFQDN\C$\Windows\CertLog, for example). We need to pass this path to three functions:
Read more →
Hello S-1-1-0!
Recently I noticed that PowerShell in Windows Server 2012 R2 ships two new cmdlets: Backup-CARoleService and Restore-CARoleService which are used to backup and restore CA database and CA keys. Today I want to talk about CryptoAPI functions utilization to backup CA database in PowerShell.
Backup step-by-step guide
Although, backup process isn’t looking very complex, however CryptoAPI implements a number of detailed (low-level) functions which must be called in a certain sequence. Here is a copy of the article that explains the correct sequence:
Read more →
In this post I will discuss about non-standard string comparison in Certification Authority database queries. This post will focus on my PowerShell PKI module and queries in the CA database. The module contains the following commands that support CA database queries:
Request filters support the following comparison (seek) operators:
Read more →



