Posts on this page:
- Standard and alternate signature algorithms
- Acknowledges and special thanks
- Verifying The SSL Certificates with a tool
- PowerShell Cmdlet Help Editor 2.0
- SHA1 Deprecation Policy.
Time by time I receive questions about alternate signature algorithms. What is the difference between them and what benefits are in an alternate signature algorithms.
As per TechNet article:
For certificates based on RSA algorithms, PKCS #1 v2.1 specifies separate object identifiers for the hash algorithm and for the asymmetric algorithm. (In PKCS #1 v.1.5, only one object identifier is used to identify both the hash and asymmetric algorithms.) In addition, if you select the alternate signature format for certificates based on RSA algorithms, an enhanced cryptographic formula is used to create the signature.
Generally speaking, alternate signature algorithm (signature format) just allows to specify additional details about how signature is constructed.
Read more →
This is the last my post this year and I want to make a little summary about my blogging and public projects I’m running and to acknowledge some companies and people.
Projects summary
During this year I continued to focus on Public Key Infrastructure and it’s integration into Windows PowerShell. It is unfortunate that only few people pays attention to this aspect. While many Microsoft products and technologies have solid support in PowerShell, ADCS and PKI still has very poor support. Finally, Microsoft developed cmdlets for ADCS components installation (starting with Windows Server 2012) — it is a big win. However, built-in cmdlets still lacks in ADCS component management in PowerShell.
To be honest, cmdlets in PKI and AdcsAdministration modules are awful and don’t cover daily ADCS management tasks. On the other hand, it is a great field (opportunity) for me, to continue PowerShell PKI module development. During this year I shipped two releases of this module. Each new version implements new commands, features and resolves detected issues. New version is coming (release is planned in January).
Also I’m continuing to work on others projects and concepts. For example, PowerShell Cmdlet Help Editor. so far it is the only publically available help editor for 3rd party modules. Primarily I developed the editor to cover my own needs to create unified help content for PowerShell PKI module. First version covered just basic functionality. It wasn’t enough, so I added an ability to generate HTML code which can be pasted to your web site (for example, to CodePlex). However, I noticed that help content review (for typos or other inaccuracies) is not very easy, so I added a browser plugin to the editor, so you can select the cmdlet and view entire cmdlet help content in a user-friendly way. There are other improvements which I didn’t mentioned, the main idea is the same — make the editor more user-friendly and reduce the time on content writing and review.
In addition, you can check my little, but very useful scripts on TechNet Gallery: PowerShell File Checksum Integrity Verifier (PsFCIV) and Self-signed certificate generator (PowerShell), which are now a part of PKI module. Do not forget about my recent work: Verifying The SSL Certificates with a tool, which is outstanding and still, there are ways for improvement and enhancements (it requires a time).
Acknowledges
All these projects require a lot of time. Since I’m working on them during my free time, I’m trying to spend the time more effectively. Also, the product should be easy to ship and install by end-users. Therefore I want to mention some companies which helped me with free NFR (Not For Resale) licenses for their products.
- Dell Software — PowerGUI Script Editor (still free). I’m using PowerGUI many years (5+ years) and now I can’t imagine complex PowerShell script writing outside of it. Really, smart and effective product (comparing to others) for script development and testing.
- Sandcastle Help File Builder (already free). This is a great tool which is intended to generate a user-friendly help content for your own .NET projects. Here is the documentation example from my PowerShell PKI module: http://pkix2.sysadmins.lv/library/
- JetBrains — ReSharper. I’m not considering myself as a decent C# developer and my experience in this language and behaviors is average. ReSharper dramatically improved my C# code, made it cleaner, shorter and smarter by removing unnecessary/redundant code paths and follows for code compliance, refactoring, code generation and more and more. This is really-really invaluable tool. Even if they retire the NFR license, I will buy it.
- Caphyon — Advanced Installer. PowerShell module distribution is a real challenge. Unfortunately, PowerShell don’t have easy and flexible ways to distribute 3rd party modules (like NuGet in Visual Studio) and it looks like: pack the module to ZIP, provide a long instructions to end user to install and configure the module. The things become worse when there are additional dependencies (like required .NET version). End users are not PowerShell MVPs and don’t have to know all these details, they just need to install the module, run in, ??????, PROFIT. This is what Advanced Installer does. It easily packs the module to a MSI package which can be easily installed with few “Next-Next-Finish” clicks.
MSI creation is not an easy process, but Advanced Installer is really-really easy to use, user-friendly with a really good help content which do not overhead the user with unnecessary technical details. - DigiCert. When you distribute the software over internet, it is important to make sure that end user receives the code that was produced by a developer, without modifications. Digital signatures on a software ensures that no one added, removed or somehow tampered the code after it was released (intentionally or unintentionally). In addition, digital signatures increases the trust between the developer and end user, especially when the software was downloaded from untrusted sources. this ensures that 3rd party (hosting company or someone else). Each my product, script is digitally signed, so you can be sure that it wasn’t modified after I signed it.
Special acknowledges
While I mentioned companies that helped me with products that reduces my time on project development, I want to mention two guys from Microsoft, who help me with their brains and who put reasonable effort in PKI module development. Probably you never heard about them, but I think you should know these “invisible” heroes:
- Vic Heller (Microsoft). Vic is a heart, head, hands, knees and soul of Windows PKI. Cryptography is not the easiest technology and cryptography documentation and API in Windows is a hell. Apparently it is written for incredibly skilled in cryptography guys who can understand it. Just an example: CryptSetProvParam function. Also, the API behavior is not always clear from the documentation. Time by time I’m struggling on some aspect (theoretical or practical) and even Google can’t help there. Only Vic “Last Chance” Heller can help in such cases. I can’t remember if there was a question when Vic or Rashmi couldn’t find an answer.
- Rashmi Jha (Microsoft). When the question is about OCSP or certificate enrollment web services questions, Rashmi is (maybe, the only) the rescue service there.
Sometimes I’m writing about interesting behavior in Windows PKI which is not described anywhere and which I got from these guys. For example, Database log files are not truncated when you perform a full Certification Authority database backup, or String comparison in Certification Authority database queries.
Thank you all, who helped and continue to help me with your products or brains, your help is invaluable!
Hello S-1-1-0, CryptoGuy is back with some good news!
About two years ago Windows PKI team posted about a SSL certificate expiration checking tool: Verifying The SSL Certificate Expiration with a tool. However, the download link is broken and PKI blog writers aren’t responsive, so there is no chance to get the utility. Although I have this tool, it is useless a bit more than completely. This is because the utility just checked leaf certificate for expiration without performing any additional checks.
A week ago I decided to make my own tool with “Black Jack and Hookers”. For a first attempt I asked myself to implement the following wishes:
- Validate the SSL certificate and validate all certificates in the chain for possible errors;
- Implement certificate expiration checking (as in original tool). Certificate expiration should be checked for all certificates in the chain;
- When we connect to a host, it may decide to redirect us to another site. Say, we connect to paypal.com, the server will redirect us to www.paypal.com. The fact is that these two servers may use different certificates (as is the case for paypal.com). Therefore, the tool must process all redirects and collect certificate status information for all of them.
- Write trace/debug log for each processed entry;
- Provide an ability to save server list to a file and read the list from a file.
Read more →
Yesterday I released another version of PS Cmdlet Help Editor. It is minor update, which resolves several issues (not very critical), internal code redesign and added support for PowerShell 4.0.
Two notable updates were made in this release:
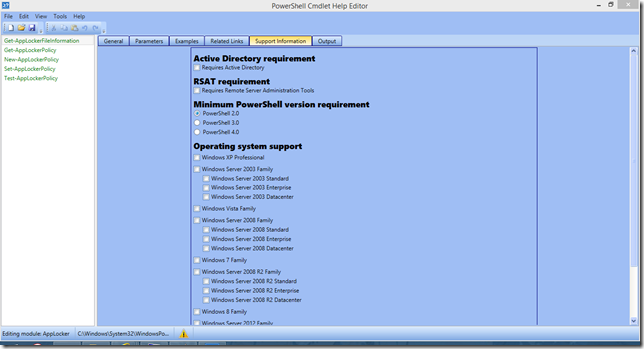
1) Support Information tab
in this tab you can specify basic requirements and platforms your module supports. When you save help file, support information (if it is enabled in the settings), this support information is saved in the same folder with the following naming format: <ModuleName>.supports.xml. And when you load your module next time, the editor attempts to find appropriate file to fill this tab.
Read more →
Warning: this post is the shortest post in the entire blog.
Microsoft announced a deprecation policy for certificates signed with SHA1 (sha1RSA) signature algorithm. The algorithm should not be used after January 1 2016. US NIST Guidance has counseled that SHA1 should not be trusted past January 2014 for the higher level of assurance communications over the US Federal Bridge PKI.
More on Windows PKI weblog: SHA1 Deprecation Policy.