Posts on this page:
- How to convert PKCS#12/PFX to PEM format
- How to retrieve certificate purposes property with CryptoAPI and PowerShell
- How to register custom Object Identifier
- Digging into digital signatures (part 2)
- Digging into digital signatures (part 1)
Hello folks! If you are longing for CryptoAPI stuff here, then you are on the right page. Here you will see another bunch of CryptoAPI, PowerShell and p/invoke hardcore.
Today’s subject is to convert PFX file to PEM format. A time ago I wrote a function that does opposite — converts PEM to PFX: How to convert PEM file to a CryptoAPI compatible format. Read this post to get information about CryptoAPI structures and ASN modules for PKCS#1 and PKCS#8 structures.
The script below performs the following tasks:
- Reads certificate or certificate file. If the file is not valid PFX or certificate hasn’t associated private key, an exception will be thrown.
- Acquires private key (via unmanaged function calls) and attempts to export raw private key from CSP. If the private key is not marked as exportable or it is stored on smart card, an error will be thrown.
- Inspects CryptoAPI private key blob as described here: RSA/Schannel Key BLOBs, removes header, reads raw private key and splits it to components (modulus, primes, exponents, coefficient). Each component is stored in separate variable.
- Generates required ASN structures according to output type by using basic ASN encoder.
- composes certificate and private key and saves them to file.
Read more →
Hello crypto world! One my colleague asked me about how to get certificate purposes property. Here is a little intro.
Certificate purposes are (mainly) limited by Enhanced Key Usages extension:
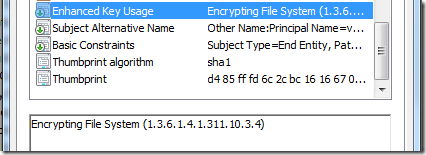
That is true. In certain cases it is reasonable to limit certificate purposes to a subset of purposes that are allowed in EKU extension. For example, in many and many CAs are allowed for any purpose (All Application Policies) and you can limit it's purposes to a limited set:
Read more →
Today I will discuss about how to register custom object identifier on a local computer. Why you need this? .NET Oid class which can resolve many common object identifiers to their friendly names and vice versa. However, not all OIDs are registered there. For example, RDS (Remote Desktop Services, former Terminal Services) team introduces special OID for RDP-SSL enhanced key usage with OID=1.3.6.1.4.1.311.54.1.2:
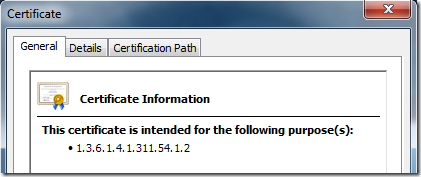
If you have Active Directory domain and at least one Enterprise CA, you can define this OID in Active Directory (by editing certificate template). But what if you don't have Active Directory or internal Enterprise CA? Then PowerShell and CryptoAPI is the answer here!
Read more →
In previous post we talked about digital signatures and how we can verify them in PowerShell (RSA signatures). I promised to continue this diving with unmanaged stuff.
As we already discussed, CryptoAPI has unmanaged structure CERT_SIGNED_CONTENT_INFO which represents a signed info, including actual data to be signed, algorithm identifier and signature value. In order to deal with this structure we need to use some encoders and decoders. In the decoding process a ASN.1-encoded raw byte array is converted to a structure and in encoding process, a structure is converted to a ASN.1-encoded byte array. CryptoAPI contains 2 (actually 4) functions for ASN.1 encoding/decoding:
Read more →
Hi folks!
A time ago I wrote a high-level description about the signatures in Digital signatures blog post. And today I want to demonstrate how this works in a real world.
In a real world there are too many signature types, including RSA signatures (plain), Authenticode, XML, Document-specific (MS Word, Adobe PDF, etc.). The simplest signature type is plain RSA signatures. This type of signatures is widely used in PKI (certificates, CRLs, signed BLOBs and so on). In ASN.1 modules (as well as in unmanaged structures), signed BLOB is written like this:
Read more →



