Posts on this page:
- Open Source Day
- Reading multiple signatures from signed file with PowerShell
- Manage pending certificate requests in ADCS with PowerShell
- How to read ADCS Enrollment Agent/Certificate Manager rights in PowerShell
- Switching my web site to SSL
It was a long-waited decision, however, finally I did it. Today I released my two major .NET projects to GitHub:
- ASN.1 Parser
This is my own ASN.1 binary parser. ASN.1 parser/reader is a mandatory component when you are dealing with cryptography and cryptographic messages, because all they use ASN.1. I’m using this library in ASN.1 Editor and PowerShell PKI module’s API library (it is now opensourced as well).
Read more →
Hello S-1-1-0, it’s time for another blog post. Another PowerShell and CryptoAPI blog post.
Identifying the problem
Recently I had a trivial (or non-trivial?) challenge: read multiple signatures from signed files. Usually files have only one signature:
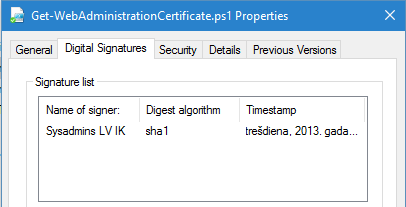
Read more →
I think, I have to publish several articles that would cover common PKI/ADCS administration tasks with PowerShell by using my PowerShell PKI module (of course!). Today I'll cover very simple, but very common task: managing pending certificate requests.
In this post we would propose the following scenario:
- IIS admin requested certificate for internal SharePoint portal
- Certificate template is configured to require CA manager approval to issue the certificate.
- No certificate will be issued until CA manager review and approve the request.
Just to make it clear, CA manager approval is configured in the certificate template, as follows:
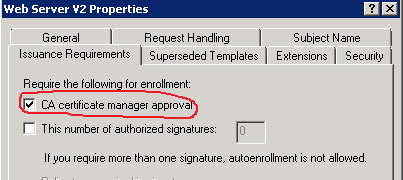
you, as CA manager, received notification about incoming certificate request. Your task is to review the certificate request to ensure that it is properly constructed and conforms internal security policies and then make decision: approve or deny certificate request. You can do this by using Certification Authority MMC snap-in, but this would require a lot of clicks and without having a chance to automate this. Another solution that includes PowerShell offers you great automation capabilites.
Read more →
Recently I was asked about how to read Enrollment Agent Rights and Certificate Manager Restrictions in ADCS. At first, I would like to make a little introduction about the subject.
Enrollment Agents
With Active Directory Certificate Services (ADCS) you can designate one or more enrollment agents to enroll on behalf of other users. One of the most common scenarios is smart card provisioning. Suppose, you purchased smart cards and plan to issue them to employees. You will designate one or more highly trusted persons who will:
- instruct employees about smart card usage policies;
- register smart card serial number/other data in the accounting system (some certificate lifecycle management system);
- prepare smart card for use (print labels and so on);
- install certificate for another employee.
Enrollment Agent Restrictions cover the last point in the list. Restrictions define three major parts:
Read more →
 I’m glad to announce that today I switched my website to SSL. This greatly increases security for my visitors, because all your data on this website is protected.
I’m glad to announce that today I switched my website to SSL. This greatly increases security for my visitors, because all your data on this website is protected.
I made a soft-permanent redirect from HTTP to HTTPS. This means that all previous links to my website will continue to work, but with redirect. In any way, I encourage everyone who have links to my website to update them by changing protocol identifier.
Please, let me know if you face any SSL-related issues when browsing my website, either, in the post comments, or by contacting me via contact form.
And the last word: many thanks to DigiCert as they kindly offered me SSL certificate. I’m using their services for several years and would say that it is really 5-star service with outstanding support lelvel and which is easy to use.
Read more →



