Posts on this page:
- 34 PKI & ADCS Whitepapers You Must Read
- Certutil tips and tricks: query cryptographic service providers (CSP and KSP)
- Certutil tips and tricks: working with X.509 file format
- Certutil tips and tricks: parsing cryptographic objects
- Constraining Extended Key Usages in Microsoft Windows
This page contains a collection of downloadable whitepapers on Public Key Infratructure (PKI) and Active Directory Certificate Services (ADCS) published by Microsoft starting with Windows Server 2003 and up to Windows Server 2012. In the past, Microsoft has published a number of high-quality deep detail whitepapers on PKI and ADCS in particular. I’m often using them in consulting projects and online forums. Unfortunately, some of them were lost in time and there is no “one stop shop” with links to all PKI/ADCS whitepapers. I put efforts in collecting them in a single place and I believe this collection is a true gem for every PKI admin!
There are several reasons for this publication:
- Whitepapers written against retired Windows Server 2003 are still relevant for the most recent Active Directory Certificate Services versions;
- Some of documents are no longer available on Microsoft Download Center and download links are dead;
- Most whitepapers are scattered over internet and are hard to find.
Here is the table of whitepapers I have collected:
Read more →
Hello S-1-1-0,
Today I’m continuing my certutil tips and tricks post series. In this post, I will get an introduction into cryptographic service provider architecture and how certutil can list and query them.
A short introduction to Cryptographic Providers
Windows Cryptography relies on a cryptographic service provider (CSP) architecture when performing cryptographic operations. CSP is a program module that represents an abstraction between client application and functions that utilize private keys. Applications are not required to interact with private key material directly, implement cryptographic functions. They only interact with known CSPs that implement private key storage database and cryptographic functions and operations. Here is a simple diagram that shows the relationship between client application and CSP:
Read more →
Hello world,
Today I’m continuing my certutil tips and tricks post series. In this post, I will show how cryptographic objects are stored in files and how certutil can convert between different presentation formats.
Binary formatting
In a nutshell, all cryptographic objects are stored in a binary stream form which is ready for transfer (transfer syntax, or raw syntax). However, transfer syntax is not suitable for other presentation forms, especially, display forms. For example, if we open binary certificate in notepad, we may see a mess like this:
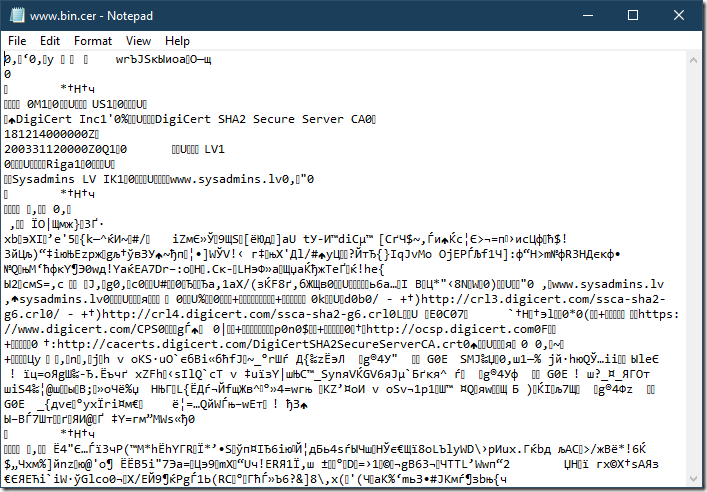
We can see a lot of non-printable characters. This means that we cannot copy/paste its contents into a text-based messaging system (web page, email body, IM, etc.). The only thing we can do here is to attach the file. If messaging system doesn’t support file attachments, we are out of luck.
Read more →
Time by time I see questions on StackOverflow.com where people ask “How to do view/decode/validate certificate in Windows?”. And answers often include OpenSSL examples for no reason. OpenSSL is not built-in into Windows box, it is a 3rd party dependency and such responses force users to download the tool to perform basic stuff. Sounds like, there is no other way to do that otherwise. Yes, OpenSSL can do these tasks, but why do people ignore native tools which are built in Windows box? I’m going to write several blog posts to promote a built-in certutil.exe tool.
Ok, what Windows can offer us? There are two main command-line cryptographic utilities called certutil.exe and certreq.exe.
Certutil is used for various cryptographic operations which include:
- dealing with cryptographic objects
- validating cryptographic objects
- managing Windows Certificate Store (view/add/delete/export/import)
- managing Active Directory Certificate Services components (including Certification Authority, OCSP server, Enrollment Web Services)
Certreq is used for certificate enrollment operations, which include:
- certificate request generation
- certificate request submission to ADCS server and issued certificate retrieval and installation
These tools cover most of cryptographic operations you may encounter when managing Windows box.
In this post, I will talk about parsing and decoding cryptographic objects with certutil.
Read more →
Hello, S-1-1-0!
Today I’m going to talk about interesting subject about Enhanced Key Usage constraints in CA certificates. This question is inspired by a thread on Security StackExchange: Root CA with Extended Key Usage fields. I put a brief answer in that thread, but still feel it is incomplete. In this blog post I will try to explain the subject in more details. Let’s start!
Extended Key Usage definition
What is Extended Key Usage or simply EKU (Microsoft calls it Enhanced Key Usage, but they both share the same abbreviation)? RFC 5280 §4.2.1.12 says:
This extension indicates one or more purposes for which the certified public key may be used, in addition to or in place of the basic purposes indicated in the key usage extension.
The meaning is quite clear. How it is processed (should be processed). Few paragraphs below (same section in RFC):
In general, this extension will appear only in end entity certificates.
<…>
If the extension is present, then the certificate MUST only be used for one of the purposes indicated. If multiple purposes are indicated the application need not recognize all purposes indicated, as long as the intended purpose is present. Certificate using applications MAY require that the extended key usage extension be present and that a particular purpose be indicated in order for the certificate to be acceptable to that application.
This part is clear too: applications verify if particular OID is presented in EKU extension or not. If OID is presented, validation continues, otherwise validation fails. RFC makes no assumptions about constraining EKU on CA level to restrict CA on issuing certificates only to a specified usages subset. Since CA certificate is not directly used as end entity certificate, EKU in CA certificate makes little sense. In theory. In practice, it is not very flexible in a number of scenarios and there are cases when such constraint is necessary. For example, company manages multiple CAs where each CA is dedicated to specific purposes. another scenario is cross-certification (qualified subordination) where such constraint is a must in order to reduce chances of mississuance and detect if misissuance occurred.
Read more →



