Posts on this page:
- Database log files are not truncated when you perform a full Certification Authority database backup.
- Install Certification Authority with PowerShell
- PowerShell PKI module v0.9.2 release
- Web Enrollment pages fails after MS11-051 patch installation
- Retrieve text messages for Win32 errors
SYMPTOMS
Consider the following scenario. You have Windows Server 2008 R2 with installed Active Directory Certification Authority role. When you perform a full database backup by using either certutil.exe utility, or Certification Authority, the database log files are not truncated, as expected and backup set may contain up to 60 database log files. When using certutil.exe tool, it reports that log files are successfully truncated:
Backing up Database files: 100% Backing up Log files: 100% Truncating Logs: 100% Backed up database to C:\Backup. Database logs successfully truncated. CertUtil: -backupDB command completed successfully.
Read more →
Hi there! PowerShell Crypto Guy is again here!
Today I've finished SetupCA.ps1 script testing and I'm ready to share it with you. Of course this is not the first attempt to install CA role from cmdline, there is already SetupCA.vbs script written by Windows PKI team. To be honest, this is not the first PowerShell script for CA installation from cmdline. The first attempt was made by Hasain Alshakarti — http://secadmins.com/?dl_id=3. However this script just illustrates basic API functionality with ability to specify CA name, CA certificate validity and CA type. There is no error handling at all, even whether the CA can be installed on the computer.
Read more →
Hi, S-1-1-0!
Finally I have finished another PowerShell PKI module release. This is not a significant release, but is quite improved. During module usage (I'm using certutil.exe less an less) I found some bugs in the previous release. Now they are fixed (at least those that were reported). The most significant change is in a new functionality. There are 3 set of cmdlets to manage the following CA settings:
Interface settings
Enrollment (ICertRequest3) and management (ICertAdmin2) interface management consist of four cmdlets:
Read more →
SYMPTOMS
Consider the following scenario. You have Windows Server 2003 with installed Certification Authority and Web Enrollment components. When you try to access web enrollment pages from a Windows Vista-based (or newer) computer you receive a message box:
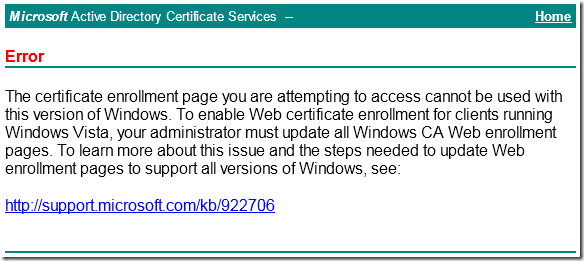
Read more →
Hi S-1-1-0! Today's topic is described in the post header :)
I guess most of you have encountered with some application/system issues. Sometimes the only information you have is Win32 error code and nothing else. To find a text message for particular error you usually use Google/Bing and/or other tools, like Err.exe from Windows Server 2003 Resource Kit. Yesterday I wrote a PowerShell script that will convert Win32 error code to a readable text. The code uses FormatMessage() WinAPI function. Here is a known limitation, this function doesn't handle network-related errors (that are defined in wininet.h header file). Hopefully my script resolves this limitation by adding a reference to the wininet.dll library when it is necessary. Here is a code snippet:
Read more →



