Posts on this page:
- Understanding Active Directory Certificate Services containers in Active Directory
- PowerShell Cmdlet Help Editor on CodePlex
- PowerShell Cmdlet Help Editor 1.0
- The History Will Be Made!
- Bulk file signing with PowerShell and user interface
Updated 20.06.2018: clarified the purpose of NTAuthCertificates DS container.
Hello folks! Today I want to explain in details about Active Directory containers related to ADCS (Active Directory Certificate Services), their purposes and how they work.
Intro
All ADCS related containers are stored in configuration naming context under Public Key Services container:
CN=Public Key Services, CN=Services, CN=Configuration, DC={forest root domain}
Since Public Key Services container is stored in configuration naming context, any it’s content is replicated between all domain controllers in the current forest (not only current domain) and are available to any client in the forest. This means that there is no way to limit PKI containers only to specific domain or domains.
Here is a screenshot from ADSIEdit.msc tool:
Read more →
Just let you know, it is pushed (with sources) to CodePlex.
Update 18.11.2013: pointed URL to a CodePlex project page.
Phinally!!!
Abstract
As you already know, last time I worked on my next PowerShell PKI module and encountered in an issue with Microsoft’s Cmdlet Help Editor. When I tried to open my module (and any other built-in module) I got very nice message:
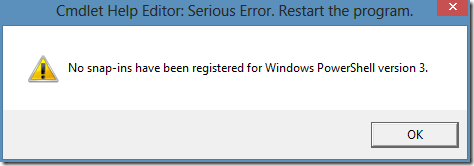
Ok, I tried to download sources (thanks, they are available for download) and was stuck with WPF. I heard that WPF is a modern replacement for WinForms, and that was the only what I knew about WPF. I was able to fix mentioned message issue, but failed with application layout. The form has fixed size and no scroll bars. So I couldn’t access textboxes and commands which are outside of my screen (even if I worked on a 1680*1050 display). And I decided to create my own Help Editor with with “blackjack and hookers”.
Read more →
Hello S-1-1-0! I rarely write offtopic posts, but holy tits God, sometimes it happens!!! Today NHL lockout is ended (although tentatively, but in any way)!!!!!!1111oneone
Abstract
I missed real hockey (KHL is not a sort of good hockey) and this year lockout was very disappointing. Now we have shortened season (48-50) games and it is much better than nothing.
As per recent news, a new CBA (Collective Bargaining Agreement) is signed for another 10 years. The season may start at January 15 (for 50-game season) or 19 (for 48-game season). Salary cap for this season remains the same ($70,2 million) and for the next season it is set to $64,3 million.
Read more →
Hello S-1-1-0! Today I would like to present a PowerShell script that allows you to add multiple files to a form and sign them using Authenticode signature.
As you already know, I’m using Software Restriction Policies and Applocker to prevent users (including myself) from running unauthorized applications and scripts. I’m using various options to allow certain applications and scripts in group policy. In certain cases I’m using hash rules, but mostly (as possible) I’m using digital signatures and publisher/certificate rules.
Since I’m writing a lot of PowerShell scripts I have to sign them in user-friendly way. Yes, there is Set-AuthenticodeSignature cmdlet, but I dislike to specify file path and signing certificate each time I want to sign something. Previously I used a nice function that adds a context menu to Windows Explorer and signs file: Подписывание скриптов PowerShell – практическая реализация (часть 2). However this script adds context menu only for PS1 files, while there are a lot of other file types that supports digital signatures. To address this question I wrote a little WinForms PowerShell script that allows me to perform file signing very easy. At first I start with screenshots.
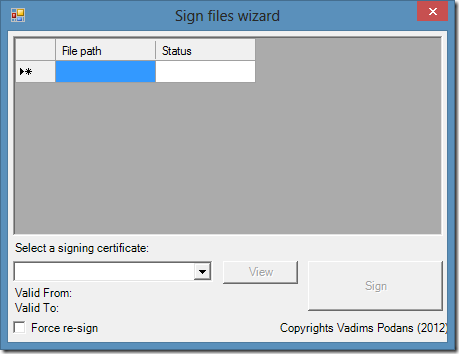
Read more →



