Posts on this page:
- You cannot submit a certificate request generated by Exchange Management Console (EMC) or Exchange Management Shell (EMS) to Microsoft Certificate Ser
- Digging into digital signatures (part 1)
- Test remote web server SSL certificate
- Do I need to implement Online Responder for Root/Policy CAs?
- Database log files are not truncated when you perform a full Certification Authority database backup.
SYMPTOMS
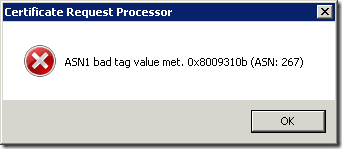
Consider the following scenario. You create certificate certificate by using either Exchange Management Console (EMC) or Exchange Management Shell (EMS) and save it to a file. When you attempt to submit certificate request to a Windows-based Certification Authority (CA) (also known as Microsoft Certificate Services), you may receive error message. If CA server runs on Windows Server 2003 (R2) or Windows Server 2008, you receive the following message:
Read more →
Hi folks!
A time ago I wrote a high-level description about the signatures in Digital signatures blog post. And today I want to demonstrate how this works in a real world.
In a real world there are too many signature types, including RSA signatures (plain), Authenticode, XML, Document-specific (MS Word, Adobe PDF, etc.). The simplest signature type is plain RSA signatures. This type of signatures is widely used in PKI (certificates, CRLs, signed BLOBs and so on). In ASN.1 modules (as well as in unmanaged structures), signed BLOB is written like this:
Read more →
A time ago, Windows PKI team posted an article about a tool that allows you to check web server SSL certificate: Verifying The SSL Certificate Expiration with a tool. Unfortunately, the download link is broken. I have this tool and uploaded it to my weblog: VerifySSLCertificate.
- ZIP archive SHA1 hash: C633A3DC3E8A3AA6BDD714EABB925429076A160A
- Executable SHA1 hash: A13CE031F5C1331785E87B62D1464C6260549EC0
The tool is very good, but what if you want to run the test against a bulk of servers? Any sort of automation and batching means some PowerShell stuff :). To provide administrators with such tool I wrote a PowerShell script, where you can test web server SSL certificate and it's status. You can export required fields to XML or CSV for future examination/audit. Let's go:
Read more →
Hi S-1-1-0, PS Crypto Guy is again on the board! Today I want to discuss about implementing Online Responder for Root and Policy CAs.
Abstract
Online Responder implements Online Certificate Status Protocol (OCSP) as a part of alternate certificate validation mechanism (or revocation provider). Classic PKI uses Certificate Revocation Lists (CRL) to provide an information about revoked and untrusted certificates issued by the particular Certification Authority (CA). Most applications perform certificate checking for revocation by downloading and examining the particular issuer's CRL (or CRLs). If the presented certificate's serial number is listed in the corresponding issuer's CRL, an application rejects that certificate. During the CA lifecycle, you sometimes revoke some unnecessary and untrusted certificates. For example, if a certificate holder lost his/her certificate and associated private key, or a user left the company. Each revoked certificate's serial number is added to the CRL.
Read more →
SYMPTOMS
Consider the following scenario. You have Windows Server 2008 R2 with installed Active Directory Certification Authority role. When you perform a full database backup by using either certutil.exe utility, or Certification Authority, the database log files are not truncated, as expected and backup set may contain up to 60 database log files. When using certutil.exe tool, it reports that log files are successfully truncated:
Backing up Database files: 100% Backing up Log files: 100% Truncating Logs: 100% Backed up database to C:\Backup. Database logs successfully truncated. CertUtil: -backupDB command completed successfully.
Read more →



