Posts on this page:
- CA certificates and Untrusted Certificates container
- How to change CA certificate validity period
- You cannot download CA certificate from web enrollment pages
- How to merge certificate and private key to a PKCS#12(PFX) file
- Certificate Chaining Engine — how it works
As you may know a DigiNotar CAs was compromised due of some reasons (one, two). Microsoft have decided to break DigiNotar CAs trust at all — http://support.microsoft.com/kb/2607712. Trust breaking is performed as follows:
- DigiNotar CA certificates are removed from Windows Update;
- DigiNotar CA certificates are removed from crypt32.dll on Windows Vista+;
- DigiNotar CA certificates are moved from Trusted Root CAs container to Untrusted Certificates.
Read more →
Today I want to discuss one question about CA certificate validity and how this can be changed.
Issue background
A little abstract. When you install Windows Certification Authority the default value is 5 years. It is quite long period and many young administrators leave default value (especially if they are not very experienced in certificate services). After a time it appears that 5 years is too short validity for CA certificate and administrators lookups for a resolution.
Read more →
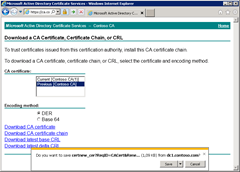
SYMPTOMS
When you try to download CA certificate from web enrollment pages you get a prompt message with unreadable proposed file name:
Do you want to save certnew_cer?ReqID=CACert&Renewal=1&Enc=bin (1,09 KB) from <ServerName>
Read more →
Hello S-1-1-0, PowerShell Crypto Guy still here and today we will talk about the subject. Sometimes you have to use 3rd party applications/tools for certificate request generation. Some of them uses Windows certificate store to store request and a corresponding private keys, but others generates a request file and separate file with unencrypted private key. As a common example are makecert.exe and openssl.exe tools. These applications creates a request file (mostly with .CSR or .REQ file extension) and private key file (mostly with .KEY or .PVK file extension) for UNIX-like systems compatibility. Once certificate request is signed you get a standard X.509 certificate file.
Read more →
Table of contents:
- Understanding certificate chains
- Exploring SSL certificates in action
- Building the Certificate Chain
- Binding Certificates
- Signature validation
- And more...
- Conclusion
- Related links
Often the certificate path/revocation checking issues that certification authority (CA) admins encounter are caused by invalid CDP (CRL Distribution Point) or AIA (Authority Information Access) configuration. This article covers the Certificate Chaining Engine (CCE) and how it can be used for troubleshooting purposes.
Read more →