Time by time this happens. Even highly trusted commercial certification authorities issue fraudulent certificates to malicious users. In 31 January 2001 (more than 10 years ago) VeriSign issued two fraudulent certificates to Microsoft on behalf of unknown men. This is very strange for a company who sell digital certificates starting with $100+ and cannot perform requestor identification as documented in their CPSs.
Ok this was ten years ago. But about 2 weeks ago Comodo CAs was compromised ( http://blogs.comodo.com/it-security/data-security/the-recent-ra-compromise/ ). If VeriSign issued only two fraudulent certificates, Comodo — 9!!!!1111oneone. And to what names: login.live.com, login.yahoo.com, www.google.com, mail.google.com, login.skype.com and so on. All of them are SSL certificates. And not usual SSL certificates, but Extended Validation (EV) certificates!
What exactly means extended validation certificate? In theory these are certificates issued according to a specific set of identity verification criteria. These criteria require extensive verification of the requesting entity's identity by the certificate authority (CA) before a certificate is issued (grabbed from Wikipedia). In practice this doesn't mean anything. Sadly, but true. Commercial CAs request $300+ for each such certificate for a one year. In this case each certificate was issued for 3 years. It is a chance to earn about $9 000. Looks good, but what about security? I understand that big and rich vendors can bypass CA's security measures (like requester verification), but this may cause issues like this. Even if certificates cannot be used.
Microsoft issued update to move these certificates to Untrusted Certificates store. Details here: http://www.microsoft.com/technet/security/advisory/2524375.mspx
Ok, our subject is slightly different than Comodo's compromise, but is related. What about if CA has issued a fraudulent certificate, but attacker has tampered or spoofed DNS? In this case even certificate is revoked by it's authority, but we cannot determine certificate revocation status (due of spoofed DNS). By default the most popular web browsers ignores "revocation offline" errors and we can be forwarded to rogue web page with rogue certificate and put some sensitive data. To address this issue Internet Explorer 7 has introduced a setting that enables strict revocation checking. And if revocation checking fails, web browser displays a warning message. I'm not aware about similar feature in other web browsers. Here is a registry setting for Internet Explorer 7+:
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\Main\FeatureControl\FEATURE_WARN_ON_SEC_CERT_REV_FAILED]"iexplore.exe"=dword:00000001
Now if revocation is unavailable due of any reason, you will see similar screen:
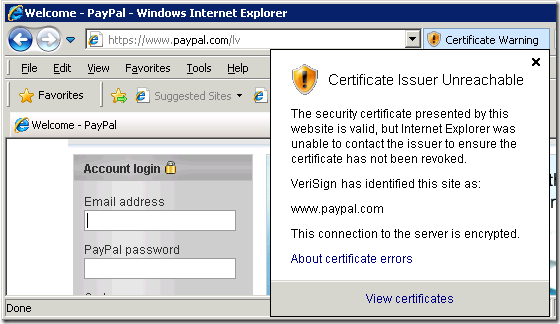
Of course systems administrators MUST instruct their users what to do when they see this message.
HTH
>Of course systems administrators MUST instruct their users what to do when they see this message. Problem is: any security measure that depends on user actions - will fail. For high security environments there should be an option to simply deny access to sites that have some problems with certificates. Vasily
Unfortunately there is no such option. There is setting that will permanently block connection to a HTTPS web site with invalid certificate, but not for mentioned case.
Post your comment:




Comments: