Posts on this page:
- Manage pending certificate requests in ADCS with PowerShell
- PowerShell PKI module, v3.1
- PowerShell PKI module v3.0 (part 4)
- PowerShell PKI module v3.0 (part 3)
- PowerShell PKI module v3.0 (part 2)
I think, I have to publish several articles that would cover common PKI/ADCS administration tasks with PowerShell by using my PowerShell PKI module (of course!). Today I'll cover very simple, but very common task: managing pending certificate requests.
In this post we would propose the following scenario:
- IIS admin requested certificate for internal SharePoint portal
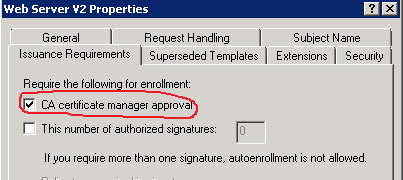
- Certificate template is configured to require CA manager approval to issue the certificate.
- No certificate will be issued until CA manager review and approve the request.
Just to make it clear, CA manager approval is configured in the certificate template, as follows:
you, as CA manager, received notification about incoming certificate request. Your task is to review the certificate request to ensure that it is properly constructed and conforms internal security policies and then make decision: approve or deny certificate request. You can do this by using Certification Authority MMC snap-in, but this would require a lot of clicks and without having a chance to automate this. Another solution that includes PowerShell offers you great automation capabilites.
Read more →
Yesterday I released another version of PowerShell PKI module v3.1.
Though, this release is not that big like v3.0. Only 1 (one!) new command is added (Get-EnterprisePKIHealthStatus) and various bug fixes (as usually). On the other hand it includes very important things which are hidden behind the scene.
The project is growing and I have to battle hard with poor design decisions I made previously. Of course, I could break everything and make it as per all guidelines. However, it is too late, 3000 downloads for the past 7 months is not a joke and I can’t simply break it.
Next sections will cover some development details, so you can scroll down to the end of post to get the right link :)
Read more →
Continuing the story, I would like to uncover some new features which are available with PSPKI v3.0. I started X.509 certificate revocation list (CRL) object factory development and already shipped basic features. These features are implemented via a set of methods. The main use case of these functions is OCSP server’s local revocation configuration. When you open revocation configuration properties, you will see Local CRL tab:
Read more →
Continuing the story about new release I will talk about two interesting features.
PKCS#7 data support
Previously there was only basic PKCS#10 certificate request support. However, there are many cases when certificate request is composed in a PKCS#7 signed message. As a start point, I tried to utilize both, EnvelopedCms and SignedCms and other related classes in the PKCS namespace. However, I quickly figured out that these classes are completely useless and do not provide any way to access PKCS#7 contents. Shame on .NET!
Read more →
Continuing the story about new release I will talk about two interesting features.
Set-CertificateExtension
Windows CA supports extension addition to a certificate request. Sometimes it is necessary. For example, IIS admin submitted certificate request for one of the web site. He used IIS Manager console to generate request. The biggest drawback of the IIS certificate request manager – it doesn’t allow you to specify subject alternative names (SAN). Or another example, some application requires custom extension which cannot be added through Certificate Templates console. Or, maybe, certificate request contains some unwanted extensions and you want to disable them. Set-CertificateExtension command will be very handy in such situations.
Read more →



