Disclaimer: this article contains information about modifying the IIS configuration files. Before you modify the IIS configuration file, make sure to back it up and make sure that you understand how to restore the file if a problem occurs.
This article contains information about unsupported operations. Before you modify any settings described below, make sure to backup your system and make sure that you understand how to restore the system if a problem occurs
A little abstract. The Online Certificate Status Protocol (OCSP) is an Internet protocol used for obtaining the revocation status of an X.509 digital certificate. Why it has been developed? Prior to OCSP, clients checks certificate status (valid/revoked) using certificate revocation lists (CRLs). Client software downloads certificate issuer CRL file and examines its Revocation List property. If particular certificate serial number is present in CRL, certificate is considered as revoked or invalid and is rejected for usage. While CRLs may contain many revoked certificates, CRL size is grown. Typically empty CRL with default settings is about 600 bytes (the CRL size generally depends on field and extension textual information length and signing certificate key length). Each revoked certificate entry is about 80 bytes. If 10 certificates are revoked, CRL size will be: 600 + 80 * 10 = 1400 bytes. For 100 revoked certificates the size will be about 9 kilobytes. For 100 000 revoked certificates, the size will be approximately 8 megabytes.
When multiple clients tries to use particular certificate (for example, clients connects to SSL web site) they downloads full CRL (if it is not cached already). This may cause network bandwidth overhead and significant time delays in certificate revocation checking process. Online Responder model was developed to address this issue. When OCSP-aware client checks certificate status, the client extracts serial number from certificate and submits a query to certificate issuer Online Responder service. When request is reached Online Responder, it responds to client with certificate status: Valid or Revoked. In overall certificate request and response have known size ~2 kilobytes. So if a lot of clients connects to particular SSL web site, they are not required to download large CRLs, but just send short requests to OCSP service.
This was a little abstract. For additional information about OCSP please refer to the following documents:
- X.509 Internet Public Key Infrastructure Online Certificate Status Protocol – OCSP
- Installing, Configuring, and Troubleshooting the Online Responder
Note: it is recommended to perform steps described below before you setup certification authority (CA).
I assume that you have installed Online Responder Service on separate web server with default settings. It is not recommended to install OCSP Responder on the same computer as CA server.
When you setup OCSP responder using Server Manager, it is installed as virtual directory in the default web site and has the following URL format: WebServerComputer.company.com/ocsp. This is not quite nice URL format, so you may wish to get something like this: ocsp.company.com. Unfortunately there is no standard tools to move OCSP application to another web site. However there are some tricks that allows this.
- Log on to OCSP Responder server with local administrator permissions.
- On the Windows desktop, click Start, click Administrative Tools and click Internet Information Services (IIS) Manager.
- Expand web server name node and select Sites node.
- In the Actions pane click Add Web Site link.
- Fill the dialog box as shown in the picture:
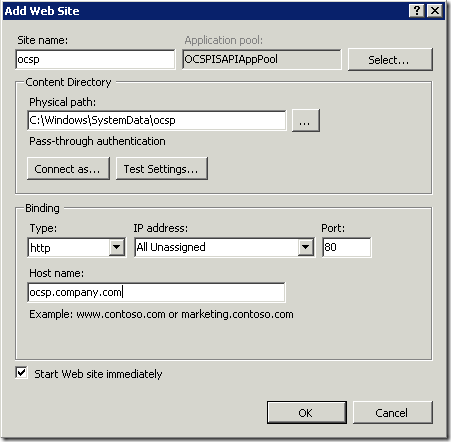
Note: in the Host name type your own custom OCSP URL.
Note: in order to access this site you will have to configure your DNS servers that serves custom URL domain zone. In a fact you will have to add new CNAME record with the following name: OCSP and point this alias to web server host A record. - Click Ok to close dialog window.
- Exit IIS Manager console.
- Do not log off from this server.
At this time we have created new web site that will host OCSP Responder service. Now we need to do move application settings from default location to the new created web site. While OCSP implementation in Windows relies on ISAPI only, the only way to move configuration is to edit IIS configuration file.
- Locate the following directory: C:\Windows\System32\inetsrv\config
- Locate applicationHost.config file.
- Backup this file in order to restore settings if problem occurs.
- Open file in your favorite TXT/XML editor.
- Locate the following section at the bottom of the configuration file:
<location path="Default Web Site/ocsp"> <system.webServer> <handlers accessPolicy="Read, Script"> <clear /> <add name="ISAPI-dll" path="*.dll" verb="*" modules="IsapiModule" resourceType="File" requireAccess="Execute" allowPathInfo="true" /> <add name="AboMapperCustom-107421" path="*" verb="*" modules="IsapiModule" scriptProcessor="C:\Windows\system32\ocspisapi.dll" requireAccess="None" responseBufferLimit="0" /> <add name="TRACEVerbHandler" path="*" verb="TRACE" modules="ProtocolSupportModule" requireAccess="None" /> <add name="OPTIONSVerbHandler" path="*" verb="OPTIONS" modules="ProtocolSupportModule" requireAccess="None" /> <add name="StaticFile" path="*" verb="*" modules="StaticFileModule,DefaultDocumentModule,DirectoryListingModule" resourceType="Either" requireAccess="Read" /> </handlers> <security> <authentication> <windowsAuthentication enabled="false" /> <anonymousAuthentication enabled="true" logonMethod="Network" /> <digestAuthentication enabled="false" /> <basicAuthentication enabled="false" logonMethod="Network" /> </authentication> <requestFiltering allowDoubleEscaping="false" /> </security> </system.webServer> </location>
- Change path in the pasted leading
<location path="Default Web Site/ocsp">tag to the following:<location path="ocsp">. Each <location path="path"> tag represent each web site, web application or virtual directory settings. While our default web site haven't custom settings (actually each web site inherits settings from server scope settings), we'll define new settings for OCSP Responder. - Save changes in configuration file.
Now you will have to configure certification authority to add this OCSP URL (for example http://ocsp.company.com) to AIA extension. After CA configuration you may have to do refresh OCSP URL in PKIView.msc MMC snap-in. To do this, revoke the most recent CA Exchange certificate and in Command Prompt run the following command:
certutil –cainfo xchg
If all is ok, you may run PKIView.msc MMC snap-in (available on CA server) and check if all is correct. Here is a screenshot from my PKIView.msc snap-in:

I have made this operation for several times and this always works for me. In any case if you have encountered in issues, you may revert all changes and/or contact me for assistance.
Hi Vadims, thanks for this workaround. Everything work fine excepts the GET-Requests (Opera only supports GET-Requests). So when I configure the Default Website in the AIA-Extension (http://abc.xyz/ocsp) the GET-Request is handled by the OCSP-Responder but when I change the AIA-Extension to a custom website (http://abc.xyz) and do all the settings you described above, the OCSP-Responder returns a "Internal Server Error 500" after the GET-Request. I traced the communication and couldn't figure it out, why I get this error. Any suggestions? Thanks. bollo007
If you check OCSP location in web browser, you should recieve HTTP500 error, this is expected behavior, because OCSP service is based on a custom ISAPI handler.
Yes you are absolutely right, but that's not what I mentioned. I traced my communication with Wireshark and Opera sends a GET-Request like this http://abc.xyz/ocsp/MMEswEt....ACM%3D and I get a correctly Response from the OCSP-Responder with the default configuration of the OCSP website. But when I configure the OCSP-Responder and the AIA in the CA for a custom OCSP website, Opera sends a GET-Request like this http://abc.xyz/MMEswEt....ACM%3D and I get an Error 500 from the OCSP-Responder. I tried nearly everything and couldn't find the problem. If you want to have a look at the trace, feel free --> http://imageshack.us/photo/my-images/263/trace2.jpg/ bollo007
Did you find a resolve for you Error 500? i am interested in setting up a custom web URL as well to explory the possiblity to publish externally using ISA/TMG/UAG.
Apparently I cannot spell today. Did you find a resolve for your Error 500? I am interested in setting up a custom web URL as well to explore the possibility to publish externally using ISA/TMG/UAG.
When you open OCSP location in web browser you should receive HTTP500 error. It is expected behavior.
Hi Vadims, i've tried this guide to change ocsp to custom url. Followed all your steps. This part seems to be fine but my pkiview will still show error after i changed to custom url. I've revoked all ca exchange certificates in my CA and when i open pkiview it will get a new one but the new custom url shows error. I've also done some test. When using certutil -url cert.cer with new ocsp url certificate check is successful. i get verified for cert, revoked for revoked cert and unavailable when i shutdown lan interface for ocsp server. So ocsp seems to work fine.
I'm aware about this issue. Sometimes it happens and sometimes not. There is nothing wrong with OCSP server, since certutil reports that all is ok. It is just pkiview.msc console issue, so you can ignore this error.
OK...major breakthrough for me. For those that have a functioning OCSP responder but still show "Error" for "OCSP Location #1" in Enterprise PKI view MMC... Go to IIS and for the site you use for ocsp ensure that allowDoubleEscaping in the Configuration Editor under "system.webServer/security/requestFiltering" is set to FALSE for the site/directory that is hosting the OCSPISAPIAppPool. Boom...now shows as OK in PKI view. This plagued me for weeks...hope this helps someone else out there.
I haven't been able to get this to work after following the steps in this article. I get the same 500 error as bollo007 mentioned in his comment. Vadims replied that when you open OCSP location in web browser you should receive HTTP500 error. However, to clarify, I'm NOT referring to manually opening the OCSP location in a web browser. I get the 500 error when Internet Explorer does an OCSP check for certificate validation when a web site loads. I see the 500 error in Fiddler, and then since the OCSP response fails, I can see the CRLs being downloaded as a fallback, before the page loads.
Would appreciate any pointers Vadims or anyone else may have on how to troubleshoot the 500 error issue.
Also, as a side note, regarding the comment from KJB about setting allowDoubleEscaping to false. If you do that, and you specify a delta CRL in the OCSP revocation provider settings, then the OCSP configuration won't work, and you will see an error in the Online Responder console. And I don't see how the allowDoubleEscaping setting is related to the PKI View error, so I wouldn't change the default value of allowDoubleEscaping on the IIS OCSP web site from true to false.
Did you try to send it via POST method?
Try to run "certutil -url path\certfile.cer", select OCSP and try OCSP request.
"certutil -url" (POST) works, but Internet Explorer (GET) fails. I could not get the configuration working, so I reverted back to the default configuration (with ocsp folder under the Default Web Site) , and both POST and GET are working fine now. Also, thanks Vadims for pointing out that customizing the default configuration would not be supported by Microsoft.
I don't know what is wrong here. I'm investigating the issue, but this will take some time.
Thanks Vadims. Were you able to reproduce the issue ?
Yes, I was able to repro this issue. In the case if I will unable to find the solution, I will delete this blog post.
Thank You. Appreciate you taking the time to investigate the issue. Please let us know what you find.
I started having this issue after I installed Mircosoft UrlScan, and was gone after uninstall it. Im not an expert in crypto area, but I wanted to share this information. Instead, if I will find more problems like this... I will become an expert for sure. :) Three days searching hundreds of pages, trying lots of "solutions"... Now I want to find a solution to set urlscan.ini file not to reject GET requests from ocsp.
Another interesting thing is that I have ocsp responder with two configurations, and only one of them had this issue.
Thank you Vadims for this useful post, do not delete it even if you can't found a solution.
Hi Vadims - Just curious, Did you get a chance to look into the HTTP 500 error that you were able to reproduce ? Thanks !
Sorry, I didn't get a chance to work on this issue. And have no idea when I will.
Hi,
I have configured OCSP in AIA with both the FQDN URL of the IIS Server hosting OCSP website and the same by using the CNAME of that server.
While in PKIView the FQDN (http://iis.domain.extension/ocsp) is working fine, an error is displayed when using the CNAME (http://OCSP.domain.extension/OCSP).
I don't really understand why it is not working. In the IIS Default webSite Binding for HTTP I did not enter a hostname / SNI. Hence, it should response to all hostnames.
KR
I have moved OCSP Online Responder to custom site many times and Vadims instructions on editing C:\Windows\System32\inetsrv\config\applicationHost.config file is critical.
It works every time. Just wanted to post a thank you.
Hi I was able to do it and thank you.
Hi
I did follow your post exactly..at least that is what I thought. Unfortunately I do still get the error beside OCSP. Wonder what I am missing or did wrong? Please see my parameters:
Server 2019 with Root-PKI RO1 and Server 2019 DC1 with already installed AD/Sub-PKI/OCSP/DNS Alias set ocsp to DC1
On DC1 On DC1 add Website as OCSP1 with OCSPISAPIAppPool (OCSP naming got always error message) PhysicalPath C:\Windows\SystemData\OCSP Hostname oscp.xy.com
On DC1 changed applicationHOST.config entry from <location path="Default Web Site/ocsp"> to <location path="ocsp1">
On DC1 Certification Authority add http://ocsp.xy.com under AIA tagged include OCSP extension
On DC1 CMD => certutil –cainfo xchg
Any support is very appreciated. THANKS
Regards, Markus
Post your comment:




Comments: