In this article I want to talk about Applocker rule priority and rule sorting. As you know, Applocker has one security level or default action — Disallowed all except explicity allowed. This is common misunderstanding point for some administrators.
When you create Path or Publisher rule, it cannot uniquely identify particular file. For example, when you create Path rule such C:\BusinessPrograms\*, it will allow to run anything within C:\BusinessPrograms folder and all subfolders. Or, for example, you create Publisher rule that will allow to run any file that is signed with ‘Microsoft Corporation’ digital certificate, regardless of actual file location. It is common scenario when you want continue to block some files that are located in this folder or subfolders (in Path rule case) or files that are signed with particular certificate subject (in our case this is ‘Microsoft Corporation’ certificate), however.
To resolve this issue we can use Rule Exception list. Exceptions tell us ‘This rule is affected to all specified files except those in Exception tab’. However, as I mentioned, Applocker has only one default action/level. This means that exceptions in ‘Denied’ action are not automatically treated as ‘allowed’ action.
Right now, how rules actually work? Based on my research, the following processing rules apply to each file that you want tu run:
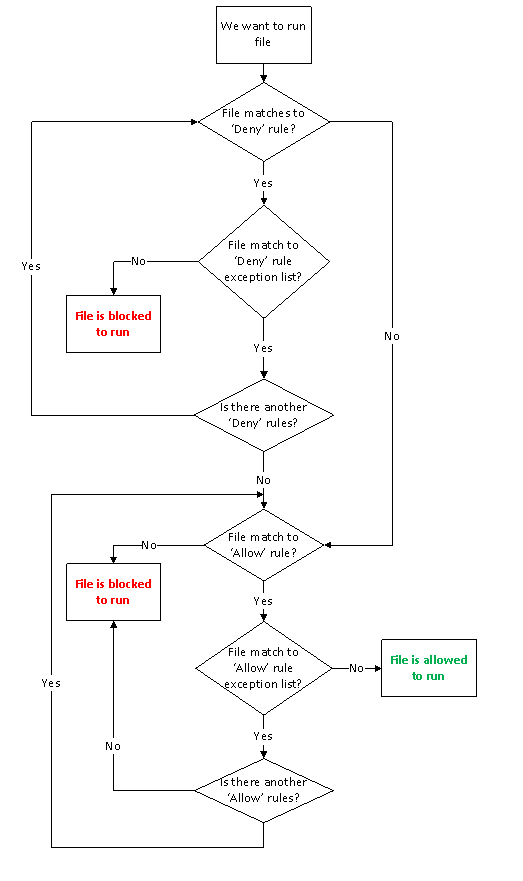
- File is checked for explicit rule with ‘Deny’ action.
- If file matches to any rule with ‘Deny’ action, exceptions for this rule are processed. If file still matches to this rule (in other words not match to any exception in this rule), the file is moved to ‘Denied’ list and file is blocked to run. No other steps are processed.
- If file don’t match to particular rule after exception processing (file matches to both main rule with ‘Deny’ action and to exception list), the file is moved to ‘Processing’ list and other rules with ‘Deny’ action are processed.
- If no explicit ‘Deny’ rule is found at previous step, Applocker check all rules with ‘Allow’ action.
- If file matches to any rule with ‘Allow’ action, exceptions for this rules are rpocessed. If file still matches to this rule (in other words, matches to main rule and not match to any exception in this rule), the file is moved to ‘Allowed’ list and is allowed to run. No other processing rules are processed.
- If file don’t match to particular rule exception processing (file matches to both main rule with ‘Allow’ action and to exception list), other rules with ‘Allow’ action are processed.
- If file status (Allowed/Denied to run) is not determined after all rule processing, file is moved to ‘Denied’ list and file is blocked to run.
It looks very difficult for understanding, so here is rule processing diagram:
For better understanding let to demonstrate one scenario.
Task:
We have Terminal Server with installed Microsoft Office. Company dictates that all MS Office programs are available for any user except Accountant group. Accountant group is allowed to run Word and Excel, all other programs from MS Office are not allowed for them. All other programs within ‘Program Files’ folder are allowed to run for everyone.
Solution:
At first we need to grant to run all programs within Program Files folder for every user. We create Path rule for Everyone group with ‘Allow’ action and point it to C:\Program Files\* path. As mentioned, Accountant group must have a limited access to Microsoft Office programs. Therefore we create another Path rule for Accountant group only with ‘Deny’ action and point it to C:\Program Files\Microsoft Office\*. Now everyone will be able to run any programs within Program Files folder, except Accountants. They will not be able to run Microsoft Office programs. To resolve this issue, we need to edit deny rule. In rule editor we need to switch to Exception tab and specify ‘Word.exe’ and ‘Excel.exe’ using path/hash/publisher rule.
Looking to a diagram, we can tell how rules will be processed when member of Accountant group will try to run Excel.
- ‘Microsoft Office’ folder is defined in Deny rule for Accountant group.
- Go down to exception list decision box.
- Excel.exe is defined in the deny rule Exception list. Move to this decision box.
- There is no any another deny rules, therefore move down to ‘Allow’ rule decision box.
- We have ‘C:\Program Files’ folder allow rule, therefore move down to rule exception processing decision box.
- This allow rule don’t contain any exception, therefore move right and we came to “file is allowed to run” action box.
If member of Accountant group will try to run PowerPoint, the following steps will occur:
- ‘Microsoft Office’ folder is defined in Deny rule for Accountant group.
- Go down to exception list decision box.
- PowerPNT.exe is not defined in the deny rule Excpetion list. Move left and we came to “File is blocked to run” action box.
I hope that this article help you ton understand Applocker Rule processing rules.
Awesome post and flow chart - thanks!
Hello, I am new to System Administration.
I apply Deny Rule on Everyone in Applocker, when program runs from Program Files or From Windows. Now i can't do any thing. all the programs are blocked even i can't see my desktop. i tried on DCGPOFIX as well but FAILUREEEEEEEEEEEEEEEEEEEEEEEE.
Please Help.
Post your comment:




Comments: