Time by time I see questions on StackOverflow.com where people ask “How to do view/decode/validate certificate in Windows?”. And answers often include OpenSSL examples for no reason. OpenSSL is not built-in into Windows box, it is a 3rd party dependency and such responses force users to download the tool to perform basic stuff. Sounds like, there is no other way to do that otherwise. Yes, OpenSSL can do these tasks, but why do people ignore native tools which are built in Windows box? I’m going to write several blog posts to promote a built-in certutil.exe tool.
Ok, what Windows can offer us? There are two main command-line cryptographic utilities called certutil.exe and certreq.exe.
Certutil is used for various cryptographic operations which include:
- dealing with cryptographic objects
- validating cryptographic objects
- managing Windows Certificate Store (view/add/delete/export/import)
- managing Active Directory Certificate Services components (including Certification Authority, OCSP server, Enrollment Web Services)
Certreq is used for certificate enrollment operations, which include:
- certificate request generation
- certificate request submission to ADCS server and issued certificate retrieval and installation
These tools cover most of cryptographic operations you may encounter when managing Windows box.
In this post, I will talk about parsing and decoding cryptographic objects with certutil.
Introducing to Certutil
As it was mentioned, certutil.exe tool is one of two main cryptographic utilities in Windows and exists since Windows NT4 Option Pack. In Windows 2000 and Windows XP (Windows Server 2003), the tool was a part of “AdminPack” package or “Support Tools”. Starting with Windows Vista and Windows Server 2008, certutil is shipped with every installation by default and no extra download or installation is required. Certutil greatly evolved over years and latest version is very powerful. The full list of commands can be retrieved by calling standard command-line tool help query:
certutil -?
The command outputs the top-level commands. Every top-level command has context commands and their usage is queried accordingly:
certutil -dump -?
There is a verbose switch that dumps more detailed output. Put -v switch in the beginning of any other parameter to get extended output. In addition, there is an undocumented switch that shows hidden and (of course) undocumented top-level commands:
certutil -uSAGE
This switch is case-sensitive.
Parse certificates revocation lists
Certutil can easily parse certificates, either from file or certificate store by using -dump parameter. In fact, this is default parameter, so you can omit this parameter when decoding the file:
PS C:\Certs> certutil www.cer
X509 Certificate:
Version: 3
Serial Number: 097772da4a53eadbe86fe01a4f97f90a
Signature Algorithm:
Algorithm ObjectId: 1.2.840.113549.1.1.11 sha256RSA
Algorithm Parameters:
05 00
Issuer:
CN=DigiCert SHA2 Secure Server CA
O=DigiCert Inc
C=US
Name Hash(sha1): 105fa67a80089db5279f35ce830b43889ea3c70d
Name Hash(md5): c47fcd4b1a68730e777c053868355ab1
NotBefore: 12/14/2018 2:00 AM
NotAfter: 3/31/2020 2:00 PM
Subject:
CN=www.sysadmins.lv
O=Sysadmins LV IK
L=Riga
C=LV
Name Hash(sha1): 8016fd7aec0a840a0e1ab7eea6eaabe0c551b403
Name Hash(md5): 4bdcfa3e75ff9a842bf4a97bb806ca07
Public Key Algorithm:
Algorithm ObjectId: 1.2.840.113549.1.1.1 RSA
Algorithm Parameters:
05 00
Public Key Length: 2048 bits
Public Key: UnusedBits = 0
0000 30 82 01 0a 02 82 01 01 00 af ce 7c d9 ec e6 7d
0010 01 33 a5 b7 0a 78 62 17 fd d5 b2 08 92 e5 27 35
0020 19 7b 6b 97 5e 9d c8 7e 08 23 2f 06 09 69 5a ec
0030 aa bb a1 01 39 d9 bd 07 5b b8 de e4 05 5d e0 55
0040 00 74 d3 2d c8 99 64 b3 43 b5 1d 99 02 5b d1 b4
0050 d7 24 7e 2c 81 e8 0c 8d f1 a6 aa 3e ac 3d ef 7f
0060 9b e8 f1 d6 f4 0f 9e 24 21 33 e9 d6 9a 29 93 87
0070 69 fe 8c c5 7a 70 e6 15 67 9a 86 a2 e2 c7 d3 0c
0080 7e 90 ef 12 a6 95 5d 57 a1 56 21 8b 00 e3 87 0f
0090 9c 58 27 c4 6c 2f 23 0c 79 d6 03 10 3f c9 f2 80
00a0 7b 7d 49 71 4a 76 4d 6f a0 ce 6a 45 d0 81 8a 66
00b0 31 d7 5d 3a f4 93 48 3e 6d b9 f4 52 33 cd c4 ba
00c0 ea f4 95 b9 51 0f 9c cc 91 9e f4 ea 59 b6 dd 1c
00d0 30 77 e4 21 59 e0 98 9d c5 c0 37 44 72 96 3a ee
00e0 16 cd 0b 2e d1 ea ad 18 4c 48 fd d4 bb 61 0e d9
00f0 9f e0 8d 90 e6 54 65 a5 1a 9d 21 68 e5 7b 0d db
0100 32 1b 63 ec 1d bd 3d 2c 63 02 03 01 00 01
Certificate Extensions: 10
2.5.29.35: Flags = 0, Length = 18
Authority Key Identifier
KeyID=0f80611c823161d52f28e78d4638b42ce1c6d9e2
2.5.29.14: Flags = 0, Length = 16
Subject Key Identifier
fc36e08508b29800c219d62a228b1e384e075714
2.5.29.17: Flags = 0, Length = 22
Subject Alternative Name
DNS Name=www.sysadmins.lv
DNS Name=sysadmins.lv
2.5.29.15: Flags = 1(Critical), Length = 4
Key Usage
Digital Signature, Key Encipherment (a0)
2.5.29.37: Flags = 0, Length = 16
Enhanced Key Usage
Server Authentication (1.3.6.1.5.5.7.3.1)
Client Authentication (1.3.6.1.5.5.7.3.2)
2.5.29.31: Flags = 0, Length = 64
CRL Distribution Points
[1]CRL Distribution Point
Distribution Point Name:
Full Name:
URL=http://crl3.digicert.com/ssca-sha2-g6.crl
[2]CRL Distribution Point
Distribution Point Name:
Full Name:
URL=http://crl4.digicert.com/ssca-sha2-g6.crl
2.5.29.32: Flags = 0, Length = 45
Certificate Policies
[1]Certificate Policy:
Policy Identifier=2.16.840.1.114412.1.1
[1,1]Policy Qualifier Info:
Policy Qualifier Id=CPS
Qualifier:
https://www.digicert.com/CPS
[2]Certificate Policy:
Policy Identifier=2.23.140.1.2.2
1.3.6.1.5.5.7.1.1: Flags = 0, Length = 70
Authority Information Access
[1]Authority Info Access
Access Method=On-line Certificate Status Protocol (1.3.6.1.5.5.7.48.1)
Alternative Name:
URL=http://ocsp.digicert.com
[2]Authority Info Access
Access Method=Certification Authority Issuer (1.3.6.1.5.5.7.48.2)
Alternative Name:
URL=http://cacerts.digicert.com/DigiCertSHA2SecureServerCA.crt
2.5.29.19: Flags = 1(Critical), Length = 2
Basic Constraints
Subject Type=End Entity
Path Length Constraint=None
1.3.6.1.4.1.11129.2.4.2: Flags = 0, Length = 16e
SCT List
v1
ee4bbdb775ce60bae142691fabe19e66a30f7e5fb072d88300c47b897aa8fdcb
Friday, December 14, 2018 9:32:36 PM
SHA256
ECDSA
30450220534d4a898f06302cf831972520bce9b7681efe51a1856969190602db6ce5aa0d022100bff63d6fdf67d889ad801c2ea8faf7b400785a4668118b1fbe496c519860f1d2
v1
8775bfe7597cf88c43995fbdf36eff568d475636ff4ab560c1b4eaff5ea0830f
Friday, December 14, 2018 9:32:36 PM
SHA256
ECDSA
3045022100f83f5fa45fdfc3cef209f8b3533489a640f8151d08fb04c23b13bb6fd7b8259f0220488cc3154c7ba8c483acc966f9c6e25e7fb0bb343d77e39ca001ca5a92a46fc8
v1
6f5376ac31f03119d89900a45115ff77151c11d902c10029068db2089a37d913
Friday, December 14, 2018 9:32:37 PM
SHA256
ECDSA
304502205f7be476ba17b0f378af72b3a4ec880809b8a63d8551e957819c98967745f20502210090c70c0ddb96c28137d8f21912b414dfc84016a52087593de3ec944d57beab90
CT[0]:
Version: 1
Key Id Hash(log-sha256): 7ku9t3XOYLrhQmkfq+GeZqMPfl+wctiDAMR7iXqo/cs=
Key Id Hash(log-sha256-hex): ee4bbdb775ce60bae142691fabe19e66a30f7e5fb072d88300c47b897aa8fdcb
Signing Time: 12/14/2018 9:32 PM
Extensions: 0000
Hash Algorithm: 4 (SHA256)
Signature Algorithm: 3 (ECDSA)
Length: 0047
0000: 30 45 ; SEQUENCE (45 Bytes)
0002: 02 20 ; INTEGER (20 Bytes)
0004: | 53 4d 4a 89 8f 06 30 2c f8 31 97 25 20 bc e9 b7
0014: | 68 1e fe 51 a1 85 69 69 19 06 02 db 6c e5 aa 0d
0024: 02 21 ; INTEGER (21 Bytes)
0026: 00
0027: bf f6 3d 6f df 67 d8 89 ad 80 1c 2e a8 fa f7 b4
0037: 00 78 5a 46 68 11 8b 1f be 49 6c 51 98 60 f1 d2
Google 'Rocketeer' log
ct.googleapis.com/rocketeer
Signature matches Public Key
CT[1]:
Version: 1
Key Id Hash(log-sha256): h3W/51l8+IxDmV+9827/Vo1HVjb/SrVgwbTq/16ggw8=
Key Id Hash(log-sha256-hex): 8775bfe7597cf88c43995fbdf36eff568d475636ff4ab560c1b4eaff5ea0830f
Signing Time: 12/14/2018 9:32 PM
Extensions: 0000
Hash Algorithm: 4 (SHA256)
Signature Algorithm: 3 (ECDSA)
Length: 0047
0000: 30 45 ; SEQUENCE (45 Bytes)
0002: 02 21 ; INTEGER (21 Bytes)
0004: | 00
0005: | f8 3f 5f a4 5f df c3 ce f2 09 f8 b3 53 34 89 a6
0015: | 40 f8 15 1d 08 fb 04 c2 3b 13 bb 6f d7 b8 25 9f
0025: 02 20 ; INTEGER (20 Bytes)
0027: 48 8c c3 15 4c 7b a8 c4 83 ac c9 66 f9 c6 e2 5e
0037: 7f b0 bb 34 3d 77 e3 9c a0 01 ca 5a 92 a4 6f c8
Not found: h3W/51l8+IxDmV+9827/Vo1HVjb/SrVgwbTq/16ggw8=
CT[2]:
Version: 1
Key Id Hash(log-sha256): b1N2rDHwMRnYmQCkURX/dxUcEdkCwQApBo2yCJo32RM=
Key Id Hash(log-sha256-hex): 6f5376ac31f03119d89900a45115ff77151c11d902c10029068db2089a37d913
Signing Time: 12/14/2018 9:32 PM
Extensions: 0000
Hash Algorithm: 4 (SHA256)
Signature Algorithm: 3 (ECDSA)
Length: 0047
0000: 30 45 ; SEQUENCE (45 Bytes)
0002: 02 20 ; INTEGER (20 Bytes)
0004: | 5f 7b e4 76 ba 17 b0 f3 78 af 72 b3 a4 ec 88 08
0014: | 09 b8 a6 3d 85 51 e9 57 81 9c 98 96 77 45 f2 05
0024: 02 21 ; INTEGER (21 Bytes)
0026: 00
0027: 90 c7 0c 0d db 96 c2 81 37 d8 f2 19 12 b4 14 df
0037: c8 40 16 a5 20 87 59 3d e3 ec 94 4d 57 be ab 90
Not found: b1N2rDHwMRnYmQCkURX/dxUcEdkCwQApBo2yCJo32RM=
Signature Algorithm:
Algorithm ObjectId: 1.2.840.113549.1.1.11 sha256RSA
Algorithm Parameters:
05 00
Signature: UnusedBits=0
0000 f7 7b 9c 62 e7 b6 83 ec 4b 4a 23 95 c7 fc 6d 91
0010 25 ca 61 0b d7 28 27 1a 28 78 2c 5c 38 5d 26 3f
0020 36 da bb 81 9e c3 1b b0 15 d1 52 28 dc 31 81 67
0030 50 9d b6 39 c9 45 2f d5 12 ac 30 6f f1 6c 47 a2
0040 b7 57 b3 60 69 8e c5 df aa 88 e7 df 41 73 86 d5
0050 a9 f5 e3 20 bf 10 cd 8f 09 32 93 ef 77 57 1d 92
0060 4c d2 54 d7 19 ac 33 36 42 67 ac 03 a9 19 31 9b
0070 3d 06 44 04 b0 11 04 b1 20 f8 82 af 31 df 52 c5
0080 21 f7 55 93 11 d5 6d 0f 39 fd d6 14 3d e0 dd 37
0090 22 69 35 42 a8 a8 00 b6 6f 27 40 fe 01 7a 6e e9
00a0 5d 25 ec f5 d7 84 24 8d 36 21 2a b8 42 e6 2f 3e
00b0 19 d1 c0 9a 98 a0 e4 62 9d c3 2e 78 75 c8 70 9b
00c0 5c 44 57 79 6c da 4c 6f 38 bf d9 88 ba a1 cd 18
00d0 f8 d7 db 83 73 34 fc c1 e4 a6 c9 7f fe 69 36 80
00e0 49 a4 98 ef a2 12 53 95 92 2a af 14 52 c3 59 68
00f0 a8 68 2a 4d 99 28 d0 f7 33 bf 81 85 aa 22 34 a8
Non-root Certificate
Key Id Hash(rfc-sha1): fc36e08508b29800c219d62a228b1e384e075714
Key Id Hash(sha1): c6ce6fa0e03411eb4c8492cc8a63573da27e949b
Key Id Hash(bcrypt-sha1): 6da1335f720ebf7c3cb7b280546ec4943cb8c3d7
Key Id Hash(bcrypt-sha256): b2460a4975065ea11c4f98480612ca0256b2ac41193315c1b5fe68569dca6659
Key Id Hash(md5): a2390892613f126ea67d49c08a32e8a3
Key Id Hash(sha256): 4fc59e5139ff419f05bf22f25734825bdeb9216c6e48f65525a765dcd0e5f582
Key Id Hash(pin-sha256): 40ZjlKbqYs7SDpsYj+bzrmlldMUSBgLujZGQId6W9/o=
Key Id Hash(pin-sha256-hex): e3466394a6ea62ced20e9b188fe6f3ae696574c5120602ee8d919021de96f7fa
Cert Hash(md5): 4f7c2f6025168bbc0801b5b5a0cbca7d
Cert Hash(sha1): 21c49dcc11e58b2bb90c3917ce033d447f376c06
Cert Hash(sha256): d4d973a6d7ec43d2db790ee181324c4e44c161369135fcc4458f347791422510
Signature Hash: 00d10c7c554d919ab26c08725b07d3c13e8c7974044a9e3d91c9ae4a27a92d3f
CertUtil: -dump command completed successfully.
PS C:\Certs>
Here is the decoded dump of my website SSL certificate. The dump includes all the information stored in the certificate is readable way. The same command can be used to decode CRL files, PKCS#10 certificate requests, Certificate Trust Lists (CTL), PKCS#7, digitally-signed catalog file, public/private keys and so on. There is no need to specify exact cryptographic object type — certutil is smart enough to determine the embedded object type and apply required decoder. That is:
PS C:\CRL> certutil DigiCertGlobalRootCA.crl
X509 Certificate Revocation List:
Version: 2
Signature Algorithm:
Algorithm ObjectId: 1.2.840.113549.1.1.11 sha256RSA
Algorithm Parameters:
05 00
Issuer:
CN=DigiCert Global Root CA
OU=www.digicert.com
O=DigiCert Inc
C=US
Name Hash(sha1): 8051060132ad9ac27d5187a0e887fb01620155ee
Name Hash(md5): 59779e39e21a2e3dfced6857ed5c5fd9
ThisUpdate: 1/10/2019 12:01 AM
NextUpdate: 1/31/2019 12:01 AM
CRL Entries: 2
Serial Number: 123dcf84ae4841b4afa731e629042ac8
Revocation Date: 11/10/2006 2:00 AM
Extensions: 1
2.5.29.21: Flags = 0, Length = 3
CRL Reason Code
Superseded (4)
Serial Number: 2a846fb0eac24af297540ac0ea634e08
Revocation Date: 11/10/2006 2:00 AM
Extensions: 1
2.5.29.21: Flags = 0, Length = 3
CRL Reason Code
Superseded (4)
CRL Extensions: 2
2.5.29.35: Flags = 0, Length = 18
Authority Key Identifier
KeyID=03de503556d14cbb66f0a3e21b1bc397b23dd155
2.5.29.20: Flags = 0, Length = 4
CRL Number
CRL Number=01b5
Signature Algorithm:
Algorithm ObjectId: 1.2.840.113549.1.1.11 sha256RSA
Algorithm Parameters:
05 00
Signature: UnusedBits=0
0000 b1 76 7f ba e8 09 b7 10 f8 f9 44 a2 20 9d 7a 11
0010 01 8b 0c 89 2b 2b a1 45 00 cb 7d e8 6c 7a 8f f8
0020 47 32 8e 47 fe 70 b6 4e 59 db a8 6b dd 43 3f 55
0030 cf 61 65 d9 ae a7 f6 a7 c0 d7 24 f9 a0 f4 03 77
0040 11 ce 05 31 86 92 da c9 13 58 88 d9 21 96 f5 31
0050 06 d7 56 00 92 4e e3 76 68 52 a8 5d 97 63 a4 ce
0060 9d 36 c4 8c 42 83 ef ae df 90 e3 b4 fe c9 9e 2e
0070 28 c9 a8 31 a7 05 87 1f 62 a6 ee ba f1 92 42 9c
0080 fa e7 88 93 31 f9 ca f5 0a 91 d7 50 28 d0 57 f9
0090 f6 d2 e8 b9 95 c3 b8 08 cd f0 f9 da 7a a0 a3 2d
00a0 f5 d1 62 6b 83 c2 89 36 13 cb cc 07 88 95 6c 99
00b0 fb e4 95 27 5c 3e 98 7e 27 fe 21 92 6a c8 00 3d
00c0 a7 0e 3f 67 ed 96 53 8a 19 2e c9 1c 7f 65 85 ee
00d0 ef c9 92 c0 6f d0 d1 e8 5a 56 e8 52 c6 c3 cf 9b
00e0 15 42 dd be 00 c3 07 ca 46 81 a9 fd 93 21 ba b9
00f0 5f 08 65 e7 da 08 dc b3 d8 e5 fd 08 9a 83 5f 1e
CRL Hash(md5): 64b3ec15f50da44cb96638735b44ee14
CRL Hash(sha1): 7c4f55184b57d5377f814591d8b88b0c1b46e541
CRL Hash(sha256): 9960ef932d2410ea01fa789930c51f48ed5ffaae3b8c826e261495e98897f9a5
Signature Hash: 0f85d9fbc8de0852ffa78563ec3220d5f69b0f87c7651d706b98747b2bed2564
CertUtil: -dump command completed successfully.
PS C:\CRL>
Same here, certutil automatically determined the type of a file. And certutil don’t rely on file extension, it relies on actual file content. In addition, certutil don’t care whether the file has pure binary (DER) encoding, or base-64 encoding. Certutil will make all decoding stuff automatically when necessary. Just to add an example of how certutil decodes OCSP responses:
PS C:\CRL> certutil 21C49DCC11E58B2BB90C3917CE033D447F376C06
OCSP Response:
OCSP_SUCCESSFUL_RESPONSE
1.3.6.1.5.5.7.48.1.1 szOID_PKIX_OCSP_BASIC_SIGNED_RESPONSE
Version: 1
OCSP_BASIC_BY_KEY_RESPONDER_ID
0f80611c823161d52f28e78d4638b42ce1c6d9e2
Produced At 1/9/2019 10:21 PM
OCSP Response Entries: 1
OCSP Response Info[0]:
Hash Algorithm:
Algorithm ObjectId: 1.3.14.3.2.26 sha1 (sha1NoSign)
Algorithm Parameters:
05 00
Issuer Name Hash(sha1): 105fa67a80089db5279f35ce830b43889ea3c70d
Issuer Key Hash(sha1): 0f80611c823161d52f28e78d4638b42ce1c6d9e2
Serial Number: 097772da4a53eadbe86fe01a4f97f90a
OCSP_BASIC_GOOD_CERT_STATUS
ThisUpdate: 1/9/2019 10:21 PM
NextUpdate: 1/16/2019 9:36 PM
Extensions: 0
Extensions: 0
Signature Algorithm:
Algorithm ObjectId: 1.2.840.113549.1.1.11 sha256RSA
Algorithm Parameters:
05 00
Signature: UnusedBits=0
0000 41 3b be d1 74 9e c4 c7 4a 1e fb 89 fb 1c 0b c3
0010 e6 7f 02 7b 67 d9 d5 c1 69 30 e5 5a 66 89 31 19
0020 3e 53 4a 2c f4 3b 3b d4 f4 c6 1e ee 8a 95 ee 67
0030 4b 0b c1 86 52 7f 3f c1 7a 6b 84 27 f8 b1 dd 25
0040 79 de 88 63 b9 73 e8 1d c9 b4 df 40 2a 2b e3 e1
0050 68 fc ed 99 98 ce 6f 66 07 3f 09 a8 ae 97 8a 71
0060 a3 18 e8 3f d8 a1 c0 a3 b7 e8 f2 89 29 6e b7 e0
0070 93 a5 9b aa ff 87 22 b1 91 78 2f 4e 14 ac e3 3b
0080 4d 10 16 bb ee d4 3b 78 58 56 9c 9e cc 24 68 bc
0090 ca d4 4f 35 d2 00 e7 0d 74 5d 41 b3 c1 39 15 ce
00a0 2e 6d 49 0c a0 cc 38 f1 94 e0 49 96 a2 e4 ed 4d
00b0 f6 33 72 67 75 86 76 55 83 04 a8 ea d7 c0 9e b6
00c0 b5 ca cf 8f 6e 49 26 7c 4e 1e b3 6b be 99 07 65
00d0 6f ea ea 33 61 5a 9b ca d2 0c f5 1a 8c a7 c8 25
00e0 c2 07 94 a1 83 16 fa e1 9d de e4 3f 55 29 a1 e0
00f0 66 80 e4 61 4d 1e ef f3 96 eb d1 24 8d cd 01 97
CertUtil: -dump command completed successfully.
PS C:\CRL>
Getting ASN.1 dump
Entire X.509 infrastructure relies on an Abstract Syntax Notation One (ASN.1) specification and Distinguished Encoding Rules (DER) to represent cryptography objects in streams. Certutil allows you to decode cryptographic objects in ASN.1 structures by using -asn parameter:
PS C:\Certs> certutil -asn www.cer
0000: 30 82 06 91 ; SEQUENCE (691 Bytes)
0004: 30 82 05 79 ; SEQUENCE (579 Bytes)
0008: | a0 03 ; OPTIONAL[0] (3 Bytes)
000a: | | 02 01 ; INTEGER (1 Bytes)
000c: | | 02
000d: | 02 10 ; INTEGER (10 Bytes)
000f: | | 09 77 72 da 4a 53 ea db e8 6f e0 1a 4f 97 f9 0a
001f: | 30 0d ; SEQUENCE (d Bytes)
0021: | | 06 09 ; OBJECT_ID (9 Bytes)
0023: | | | 2a 86 48 86 f7 0d 01 01 0b
| | | ; 1.2.840.113549.1.1.11 sha256RSA
002c: | | 05 00 ; NULL (0 Bytes)
002e: | 30 4d ; SEQUENCE (4d Bytes)
0030: | | 31 0b ; SET (b Bytes)
0032: | | | 30 09 ; SEQUENCE (9 Bytes)
0034: | | | 06 03 ; OBJECT_ID (3 Bytes)
0036: | | | | 55 04 06
| | | | ; 2.5.4.6 Country/Region (C)
0039: | | | 13 02 ; PRINTABLE_STRING (2 Bytes)
003b: | | | 55 53 ; US
| | | ; "US"
003d: | | 31 15 ; SET (15 Bytes)
003f: | | | 30 13 ; SEQUENCE (13 Bytes)
0041: | | | 06 03 ; OBJECT_ID (3 Bytes)
0043: | | | | 55 04 0a
| | | | ; 2.5.4.10 Organization (O)
0046: | | | 13 0c ; PRINTABLE_STRING (c Bytes)
0048: | | | 44 69 67 69 43 65 72 74 20 49 6e 63 ; DigiCert Inc
| | | ; "DigiCert Inc"
0054: | | 31 27 ; SET (27 Bytes)
0056: | | 30 25 ; SEQUENCE (25 Bytes)
0058: | | 06 03 ; OBJECT_ID (3 Bytes)
005a: | | | 55 04 03
| | | ; 2.5.4.3 Common Name (CN)
005d: | | 13 1e ; PRINTABLE_STRING (1e Bytes)
005f: | | 44 69 67 69 43 65 72 74 20 53 48 41 32 20 53 65 ; DigiCert SHA2 Se
006f: | | 63 75 72 65 20 53 65 72 76 65 72 20 43 41 ; cure Server CA
| | ; "DigiCert SHA2 Secure Server CA"
007d: | 30 1e ; SEQUENCE (1e Bytes)
007f: | | 17 0d ; UTC_TIME (d Bytes)
0081: | | | 31 38 31 32 31 34 30 30 30 30 30 30 5a ; 181214000000Z
| | | ; 12/14/2018 2:00 AM
008e: | | 17 0d ; UTC_TIME (d Bytes)
0090: | | 32 30 30 33 33 31 31 32 30 30 30 30 5a ; 200331120000Z
| | ; 3/31/2020 2:00 PM
009d: | 30 51 ; SEQUENCE (51 Bytes)
009f: | | 31 0b ; SET (b Bytes)
00a1: | | | 30 09 ; SEQUENCE (9 Bytes)
00a3: | | | 06 03 ; OBJECT_ID (3 Bytes)
00a5: | | | | 55 04 06
| | | | ; 2.5.4.6 Country/Region (C)
00a8: | | | 13 02 ; PRINTABLE_STRING (2 Bytes)
00aa: | | | 4c 56 ; LV
| | | ; "LV"
00ac: | | 31 0d ; SET (d Bytes)
00ae: | | | 30 0b ; SEQUENCE (b Bytes)
00b0: | | | 06 03 ; OBJECT_ID (3 Bytes)
00b2: | | | | 55 04 07
| | | | ; 2.5.4.7 Locality (L)
00b5: | | | 13 04 ; PRINTABLE_STRING (4 Bytes)
00b7: | | | 52 69 67 61 ; Riga
| | | ; "Riga"
00bb: | | 31 18 ; SET (18 Bytes)
00bd: | | | 30 16 ; SEQUENCE (16 Bytes)
00bf: | | | 06 03 ; OBJECT_ID (3 Bytes)
00c1: | | | | 55 04 0a
| | | | ; 2.5.4.10 Organization (O)
00c4: | | | 13 0f ; PRINTABLE_STRING (f Bytes)
00c6: | | | 53 79 73 61 64 6d 69 6e 73 20 4c 56 20 49 4b ; Sysadmins LV IK
| | | ; "Sysadmins LV IK"
00d5: | | 31 19 ; SET (19 Bytes)
00d7: | | 30 17 ; SEQUENCE (17 Bytes)
00d9: | | 06 03 ; OBJECT_ID (3 Bytes)
00db: | | | 55 04 03
| | | ; 2.5.4.3 Common Name (CN)
00de: | | 13 10 ; PRINTABLE_STRING (10 Bytes)
00e0: | | 77 77 77 2e 73 79 73 61 64 6d 69 6e 73 2e 6c 76 ; www.sysadmins.lv
| | ; "www.sysadmins.lv"
00f0: | 30 82 01 22 ; SEQUENCE (122 Bytes)
00f4: | | 30 0d ; SEQUENCE (d Bytes)
00f6: | | | 06 09 ; OBJECT_ID (9 Bytes)
00f8: | | | | 2a 86 48 86 f7 0d 01 01 01
| | | | ; 1.2.840.113549.1.1.1 RSA (RSA_SIGN)
0101: | | | 05 00 ; NULL (0 Bytes)
0103: | | 03 82 01 0f ; BIT_STRING (10f Bytes)
0107: | | 00
0108: | | 30 82 01 0a ; SEQUENCE (10a Bytes)
010c: | | 02 82 01 01 ; INTEGER (101 Bytes)
0110: | | | 00
0111: | | | af ce 7c d9 ec e6 7d 01 33 a5 b7 0a 78 62 17 fd
0121: | | | d5 b2 08 92 e5 27 35 19 7b 6b 97 5e 9d c8 7e 08
0131: | | | 23 2f 06 09 69 5a ec aa bb a1 01 39 d9 bd 07 5b
0141: | | | b8 de e4 05 5d e0 55 00 74 d3 2d c8 99 64 b3 43
0151: | | | b5 1d 99 02 5b d1 b4 d7 24 7e 2c 81 e8 0c 8d f1
0161: | | | a6 aa 3e ac 3d ef 7f 9b e8 f1 d6 f4 0f 9e 24 21
0171: | | | 33 e9 d6 9a 29 93 87 69 fe 8c c5 7a 70 e6 15 67
0181: | | | 9a 86 a2 e2 c7 d3 0c 7e 90 ef 12 a6 95 5d 57 a1
0191: | | | 56 21 8b 00 e3 87 0f 9c 58 27 c4 6c 2f 23 0c 79
01a1: | | | d6 03 10 3f c9 f2 80 7b 7d 49 71 4a 76 4d 6f a0
01b1: | | | ce 6a 45 d0 81 8a 66 31 d7 5d 3a f4 93 48 3e 6d
01c1: | | | b9 f4 52 33 cd c4 ba ea f4 95 b9 51 0f 9c cc 91
01d1: | | | 9e f4 ea 59 b6 dd 1c 30 77 e4 21 59 e0 98 9d c5
01e1: | | | c0 37 44 72 96 3a ee 16 cd 0b 2e d1 ea ad 18 4c
01f1: | | | 48 fd d4 bb 61 0e d9 9f e0 8d 90 e6 54 65 a5 1a
0201: | | | 9d 21 68 e5 7b 0d db 32 1b 63 ec 1d bd 3d 2c 63
0211: | | 02 03 ; INTEGER (3 Bytes)
0213: | | 01 00 01
0216: | a3 82 03 67 ; OPTIONAL[3] (367 Bytes)
021a: | 30 82 03 63 ; SEQUENCE (363 Bytes)
021e: | 30 1f ; SEQUENCE (1f Bytes)
0220: | | 06 03 ; OBJECT_ID (3 Bytes)
0222: | | | 55 1d 23
| | | ; 2.5.29.35 Authority Key Identifier
0225: | | 04 18 ; OCTET_STRING (18 Bytes)
0227: | | 30 16 ; SEQUENCE (16 Bytes)
0229: | | 80 14 ; CONTEXT_SPECIFIC[0] (14 Bytes)
022b: | | 0f 80 61 1c 82 31 61 d5 2f 28 e7 8d 46 38 b4 2c ; ..a..1a./(..F8.,
023b: | | e1 c6 d9 e2 ; ....
023f: | 30 1d ; SEQUENCE (1d Bytes)
0241: | | 06 03 ; OBJECT_ID (3 Bytes)
0243: | | | 55 1d 0e
| | | ; 2.5.29.14 Subject Key Identifier
0246: | | 04 16 ; OCTET_STRING (16 Bytes)
0248: | | 04 14 ; OCTET_STRING (14 Bytes)
024a: | | fc 36 e0 85 08 b2 98 00 c2 19 d6 2a 22 8b 1e 38 ; .6.........*"..8
025a: | | 4e 07 57 14 ; N.W.
025e: | 30 29 ; SEQUENCE (29 Bytes)
0260: | | 06 03 ; OBJECT_ID (3 Bytes)
0262: | | | 55 1d 11
| | | ; 2.5.29.17 Subject Alternative Name
0265: | | 04 22 ; OCTET_STRING (22 Bytes)
0267: | | 30 20 ; SEQUENCE (20 Bytes)
0269: | | 82 10 ; CONTEXT_SPECIFIC[2] (10 Bytes)
026b: | | | 77 77 77 2e 73 79 73 61 64 6d 69 6e 73 2e 6c 76 ; www.sysadmins.lv
027b: | | 82 0c ; CONTEXT_SPECIFIC[2] (c Bytes)
027d: | | 73 79 73 61 64 6d 69 6e 73 2e 6c 76 ; sysadmins.lv
0289: | 30 0e ; SEQUENCE (e Bytes)
028b: | | 06 03 ; OBJECT_ID (3 Bytes)
028d: | | | 55 1d 0f
| | | ; 2.5.29.15 Key Usage
0290: | | 01 01 ; BOOL (1 Bytes)
0292: | | | ff
0293: | | 04 04 ; OCTET_STRING (4 Bytes)
0295: | | 03 02 ; BIT_STRING (2 Bytes)
0297: | | 05
0298: | | a0
0299: | 30 1d ; SEQUENCE (1d Bytes)
029b: | | 06 03 ; OBJECT_ID (3 Bytes)
029d: | | | 55 1d 25
| | | ; 2.5.29.37 Enhanced Key Usage
02a0: | | 04 16 ; OCTET_STRING (16 Bytes)
02a2: | | 30 14 ; SEQUENCE (14 Bytes)
02a4: | | 06 08 ; OBJECT_ID (8 Bytes)
02a6: | | | 2b 06 01 05 05 07 03 01
| | | ; 1.3.6.1.5.5.7.3.1 Server Authentication
02ae: | | 06 08 ; OBJECT_ID (8 Bytes)
02b0: | | 2b 06 01 05 05 07 03 02
| | ; 1.3.6.1.5.5.7.3.2 Client Authentication
02b8: | 30 6b ; SEQUENCE (6b Bytes)
02ba: | | 06 03 ; OBJECT_ID (3 Bytes)
02bc: | | | 55 1d 1f
| | | ; 2.5.29.31 CRL Distribution Points
02bf: | | 04 64 ; OCTET_STRING (64 Bytes)
02c1: | | 30 62 ; SEQUENCE (62 Bytes)
02c3: | | 30 2f ; SEQUENCE (2f Bytes)
02c5: | | | a0 2d ; OPTIONAL[0] (2d Bytes)
02c7: | | | a0 2b ; OPTIONAL[0] (2b Bytes)
02c9: | | | 86 29 ; CONTEXT_SPECIFIC[6] (29 Bytes)
02cb: | | | 68 74 74 70 3a 2f 2f 63 72 6c 33 2e 64 69 67 69 ; http://crl3.digi
02db: | | | 63 65 72 74 2e 63 6f 6d 2f 73 73 63 61 2d 73 68 ; cert.com/ssca-sh
02eb: | | | 61 32 2d 67 36 2e 63 72 6c ; a2-g6.crl
02f4: | | 30 2f ; SEQUENCE (2f Bytes)
02f6: | | a0 2d ; OPTIONAL[0] (2d Bytes)
02f8: | | a0 2b ; OPTIONAL[0] (2b Bytes)
02fa: | | 86 29 ; CONTEXT_SPECIFIC[6] (29 Bytes)
02fc: | | 68 74 74 70 3a 2f 2f 63 72 6c 34 2e 64 69 67 69 ; http://crl4.digi
030c: | | 63 65 72 74 2e 63 6f 6d 2f 73 73 63 61 2d 73 68 ; cert.com/ssca-sh
031c: | | 61 32 2d 67 36 2e 63 72 6c ; a2-g6.crl
0325: | 30 4c ; SEQUENCE (4c Bytes)
0327: | | 06 03 ; OBJECT_ID (3 Bytes)
0329: | | | 55 1d 20
| | | ; 2.5.29.32 Certificate Policies
032c: | | 04 45 ; OCTET_STRING (45 Bytes)
032e: | | 30 43 ; SEQUENCE (43 Bytes)
0330: | | 30 37 ; SEQUENCE (37 Bytes)
0332: | | | 06 09 ; OBJECT_ID (9 Bytes)
0334: | | | | 60 86 48 01 86 fd 6c 01 01
| | | | ; 2.16.840.1.114412.1.1
033d: | | | 30 2a ; SEQUENCE (2a Bytes)
033f: | | | 30 28 ; SEQUENCE (28 Bytes)
0341: | | | 06 08 ; OBJECT_ID (8 Bytes)
0343: | | | | 2b 06 01 05 05 07 02 01
| | | | ; 1.3.6.1.5.5.7.2.1 CPS
034b: | | | 16 1c ; IA5_STRING (1c Bytes)
034d: | | | 68 74 74 70 73 3a 2f 2f 77 77 77 2e 64 69 67 69 ; https://www.digi
035d: | | | 63 65 72 74 2e 63 6f 6d 2f 43 50 53 ; cert.com/CPS
| | | ; "https://www.digicert.com/CPS"
0369: | | 30 08 ; SEQUENCE (8 Bytes)
036b: | | 06 06 ; OBJECT_ID (6 Bytes)
036d: | | 67 81 0c 01 02 02
| | ; 2.23.140.1.2.2
0373: | 30 7c ; SEQUENCE (7c Bytes)
0375: | | 06 08 ; OBJECT_ID (8 Bytes)
0377: | | | 2b 06 01 05 05 07 01 01
| | | ; 1.3.6.1.5.5.7.1.1 Authority Information Access
037f: | | 04 70 ; OCTET_STRING (70 Bytes)
0381: | | 30 6e ; SEQUENCE (6e Bytes)
0383: | | 30 24 ; SEQUENCE (24 Bytes)
0385: | | | 06 08 ; OBJECT_ID (8 Bytes)
0387: | | | | 2b 06 01 05 05 07 30 01
| | | | ; 1.3.6.1.5.5.7.48.1 On-line Certificate Status Protocol
038f: | | | 86 18 ; CONTEXT_SPECIFIC[6] (18 Bytes)
0391: | | | 68 74 74 70 3a 2f 2f 6f 63 73 70 2e 64 69 67 69 ; http://ocsp.digi
03a1: | | | 63 65 72 74 2e 63 6f 6d ; cert.com
03a9: | | 30 46 ; SEQUENCE (46 Bytes)
03ab: | | 06 08 ; OBJECT_ID (8 Bytes)
03ad: | | | 2b 06 01 05 05 07 30 02
| | | ; 1.3.6.1.5.5.7.48.2 Certification Authority Issuer
03b5: | | 86 3a ; CONTEXT_SPECIFIC[6] (3a Bytes)
03b7: | | 68 74 74 70 3a 2f 2f 63 61 63 65 72 74 73 2e 64 ; http://cacerts.d
03c7: | | 69 67 69 63 65 72 74 2e 63 6f 6d 2f 44 69 67 69 ; igicert.com/Digi
03d7: | | 43 65 72 74 53 48 41 32 53 65 63 75 72 65 53 65 ; CertSHA2SecureSe
03e7: | | 72 76 65 72 43 41 2e 63 72 74 ; rverCA.crt
03f1: | 30 0c ; SEQUENCE (c Bytes)
03f3: | | 06 03 ; OBJECT_ID (3 Bytes)
03f5: | | | 55 1d 13
| | | ; 2.5.29.19 Basic Constraints
03f8: | | 01 01 ; BOOL (1 Bytes)
03fa: | | | ff
03fb: | | 04 02 ; OCTET_STRING (2 Bytes)
03fd: | | 30 00 ; SEQUENCE (0 Bytes)
03ff: | 30 82 01 7e ; SEQUENCE (17e Bytes)
0403: | 06 0a ; OBJECT_ID (a Bytes)
0405: | | 2b 06 01 04 01 d6 79 02 04 02
| | ; 1.3.6.1.4.1.11129.2.4.2 SCT List
040f: | 04 82 01 6e ; OCTET_STRING (16e Bytes)
0413: | 04 82 01 6a ; OCTET_STRING (16a Bytes)
0417: | 01 68 00 76 00 ee 4b bd b7 75 ce 60 ba e1 42 69 ; .h.v..K..u.`..Bi
0427: | 1f ab e1 9e 66 a3 0f 7e 5f b0 72 d8 83 00 c4 7b ; ....f..~_.r....{
0437: | 89 7a a8 fd cb 00 00 01 67 ae 34 d3 22 00 00 04 ; .z......g.4."...
0447: | 03 00 47 30 45 02 20 53 4d 4a 89 8f 06 30 2c f8 ; ..G0E. SMJ...0,.
0457: | 31 97 25 20 bc e9 b7 68 1e fe 51 a1 85 69 69 19 ; 1.% ...h..Q..ii.
0467: | 06 02 db 6c e5 aa 0d 02 21 00 bf f6 3d 6f df 67 ; ...l....!...=o.g
0477: | d8 89 ad 80 1c 2e a8 fa f7 b4 00 78 5a 46 68 11 ; ...........xZFh.
0487: | 8b 1f be 49 6c 51 98 60 f1 d2 00 76 00 87 75 bf ; ...IlQ.`...v..u.
0497: | e7 59 7c f8 8c 43 99 5f bd f3 6e ff 56 8d 47 56 ; .Y|..C._..n.V.GV
04a7: | 36 ff 4a b5 60 c1 b4 ea ff 5e a0 83 0f 00 00 01 ; 6.J.`....^......
04b7: | 67 ae 34 d3 f4 00 00 04 03 00 47 30 45 02 21 00 ; g.4.......G0E.!.
04c7: | f8 3f 5f a4 5f df c3 ce f2 09 f8 b3 53 34 89 a6 ; .?_._.......S4..
04d7: | 40 f8 15 1d 08 fb 04 c2 3b 13 bb 6f d7 b8 25 9f ; @.......;..o..%.
04e7: | 02 20 48 8c c3 15 4c 7b a8 c4 83 ac c9 66 f9 c6 ; . H...L{.....f..
04f7: | e2 5e 7f b0 bb 34 3d 77 e3 9c a0 01 ca 5a 92 a4 ; .^...4=w.....Z..
0507: | 6f c8 00 76 00 6f 53 76 ac 31 f0 31 19 d8 99 00 ; o..v.oSv.1.1....
0517: | a4 51 15 ff 77 15 1c 11 d9 02 c1 00 29 06 8d b2 ; .Q..w.......)...
0527: | 08 9a 37 d9 13 00 00 01 67 ae 34 d4 7a 00 00 04 ; ..7.....g.4.z...
0537: | 03 00 47 30 45 02 20 5f 7b e4 76 ba 17 b0 f3 78 ; ..G0E. _{.v....x
0547: | af 72 b3 a4 ec 88 08 09 b8 a6 3d 85 51 e9 57 81 ; .r........=.Q.W.
0557: | 9c 98 96 77 45 f2 05 02 21 00 90 c7 0c 0d db 96 ; ...wE...!.......
0567: | c2 81 37 d8 f2 19 12 b4 14 df c8 40 16 a5 20 87 ; ..7........@.. .
0577: | 59 3d e3 ec 94 4d 57 be ab 90 ; Y=...MW...
0581: 30 0d ; SEQUENCE (d Bytes)
0583: | 06 09 ; OBJECT_ID (9 Bytes)
0585: | | 2a 86 48 86 f7 0d 01 01 0b
| | ; 1.2.840.113549.1.1.11 sha256RSA
058e: | 05 00 ; NULL (0 Bytes)
0590: 03 82 01 01 ; BIT_STRING (101 Bytes)
0594: 00
0595: a8 34 22 aa 85 81 bf 33 f7 d0 28 99 4d 2a 68 a8
05a5: 68 59 c3 52 14 af 2a 92 95 53 12 a2 ef 98 a4 49
05b5: 80 36 69 fe 7f c9 a6 e4 c1 fc 34 73 83 db d7 f8
05c5: 18 cd a1 ba 88 d9 bf 38 6f 4c da 6c 79 57 44 5c
05d5: 9b 70 c8 75 78 2e c3 9d 62 e4 a0 98 9a c0 d1 19
05e5: 3e 2f e6 42 b8 2a 21 36 8d 24 84 d7 f5 ec 25 5d
05f5: e9 6e 7a 01 fe 40 27 6f b6 00 a8 a8 42 35 69 22
0605: 37 dd e0 3d 14 d6 fd 39 0f 6d d5 11 93 55 f7 21
0615: c5 52 df 31 af 82 f8 20 b1 04 11 b0 04 44 06 3d
0625: 9b 31 19 a9 03 ac 67 42 36 33 ac 19 d7 54 d2 4c
0635: 92 1d 57 77 ef 93 32 09 8f cd 10 bf 20 e3 f5 a9
0645: d5 86 73 41 df e7 88 aa df c5 8e 69 60 b3 57 b7
0655: a2 47 6c f1 6f 30 ac 12 d5 2f 45 c9 39 b6 9d 50
0665: 67 81 31 dc 28 52 d1 15 b0 1b c3 9e 81 bb da 36
0675: 3f 26 5d 38 5c 2c 78 28 1a 27 28 d7 0b 61 ca 25
0685: 91 6d fc c7 95 23 4a 4b ec 83 b6 e7 62 9c 7b f7
CertUtil: -asn command completed successfully.
PS C:\Certs>
ASN decoder is very generic, it doesn't care about object type embedded in the file, it just decodes raw ASN.1 stream. That is, certutil –dump may not support some rarely used cryptographic objects, but ASN.1 decoder does support any if it is encoded by using ASN.1 encoding. There is neat thing: certutil can transform this dump back to a original binary stream. I’ll show this in next posts.
Parsing certificates from Windows Certificate Store
All techniques shown above used a file system to get input objects. Certutil can decode cryptographic objects (certificates, CRLs and CTLs) from Windows Certificate Store without having to export them to a file. Use -store parameter to access local machine store. In order to access current user store, add -user modifier:
PS C:\> certutil -user -store my "0498564a3f96c5f38b1aa10971e7549d" my "Personal" ================ Certificate 5 ================ Serial Number: 0498564a3f96c5f38b1aa10971e7549d Issuer: CN=DigiCert SHA2 Assured ID CA, OU=www.digicert.com, O=DigiCert Inc, C=US NotBefore: 05.12.2017 02:00 NotAfter: 05.12.2020 14:00 Subject: E=vpodans@sysadmins.lv, CN=Vadims Podans, O=Sysadmins LV IK, L=Riga, C=LV Non-root Certificate Cert Hash(sha1): 8b6f616b5f5629c099ae6563047f981eaf0eb740 Key Container = te-67e0cee2-efce-41bf-bcef-9203a2f5d17a Provider = Athena ASECard Crypto CSP Private key is NOT exportable Encryption test passed CertUtil: -store command completed successfully. PS C:\>
Certutil shows only basic data about the certificate and private key (when private key is presented). We can add -v (which stands for "verbose") modifier to get verbose output:
PS C:\> certutil -v -user -store my "0498564a3f96c5f38b1aa10971e7549d"
my "Personal"
================ Certificate 5 ================
X509 Certificate:
Version: 3
Serial Number: 0498564a3f96c5f38b1aa10971e7549d
Signature Algorithm:
Algorithm ObjectId: 1.2.840.113549.1.1.11 sha256RSA
Algorithm Parameters:
05 00
Issuer:
CN=DigiCert SHA2 Assured ID CA
OU=www.digicert.com
O=DigiCert Inc
C=US
Name Hash(sha1): 163b8b916b3fe4bfcec6ee0825693f90f99f8ba7
Name Hash(md5): 699f82249e09ba13e0bf1043c1e40797
NotBefore: 05.12.2017 02:00
NotAfter: 05.12.2020 14:00
Subject:
E=vpodans@sysadmins.lv
CN=Vadims Podans
O=Sysadmins LV IK
L=Riga
C=LV
Name Hash(sha1): 6b871eae518bf406250c91e7dec53bc69afa75b5
Name Hash(md5): 130230aa1eca977057afd277d8b5ed3f
Public Key Algorithm:
Algorithm ObjectId: 1.2.840.113549.1.1.1 RSA
Algorithm Parameters:
05 00
Public Key Length: 2048 bits
Public Key: UnusedBits = 0
0000 30 82 01 0a 02 82 01 01 00 bc 4f 44 bb 8d cd 26
0010 7a 97 34 8a aa a0 a7 d8 b1 d7 d8 c2 7d b3 57 f0
0020 71 a4 72 ea e2 b8 eb db 07 82 c2 a7 16 7a a1 c0
0030 f2 1c c3 22 16 bf 09 a4 a0 a3 2a 95 c4 a1 ab 40
0040 5c 40 c2 ed 83 f1 b7 c0 4f 6d 82 57 0e 77 2d 87
0050 5c 82 64 79 b6 44 c5 65 41 d6 ca 10 24 b8 68 82
0060 8b 7f f0 20 27 35 29 ec 50 fe 46 69 f4 83 d5 cc
0070 ed c0 81 00 f3 7e 15 cc b0 23 83 f6 52 a3 25 94
0080 f7 59 5f ed 59 e5 70 68 3d e9 3b 90 eb 60 fe 89
0090 f7 b2 9c c8 24 75 fb 55 f6 cd 12 a7 5c f8 4d 58
00a0 44 5f 60 0b cb 91 f8 33 a3 b2 b8 ff 23 f6 f3 30
00b0 8e 7c 20 90 6f ab 54 e3 44 4b 8c 9f cb be f4 ca
00c0 19 69 9d 08 9e 01 8d b2 f3 88 09 56 81 30 6b 32
00d0 a7 1e 15 d1 34 3f 16 de 25 86 68 30 97 ec 88 e8
00e0 84 36 f5 a0 e8 ac 2e 8e 64 d9 96 57 95 41 64 13
00f0 1c 43 5b 3f f6 ef 96 1e d6 4e ec a9 89 69 fc fc
0100 b7 0a 7f 2b 54 07 39 30 df 02 03 01 00 01
Certificate Extensions: 9
2.5.29.35: Flags = 0, Length = 18
Authority Key Identifier
KeyID=e7 02 23 80 00 4f d8 d7 bc 94 0b d9 3f 74 39 49 32 3c 8a 79
2.5.29.14: Flags = 0, Length = 16
Subject Key Identifier
9f a0 8a e0 fd 0c 65 8c e7 ce 7f dc 2c 32 84 42 e0 0a a9 df
2.5.29.19: Flags = 1(Critical), Length = 2
Basic Constraints
Subject Type=End Entity
Path Length Constraint=None
2.5.29.17: Flags = 0, Length = 18
Subject Alternative Name
RFC822 Name=vpodans@sysadmins.lv
2.5.29.15: Flags = 1(Critical), Length = 4
Key Usage
Digital Signature, Key Encipherment (a0)
2.5.29.37: Flags = 0, Length = 16
Enhanced Key Usage
Client Authentication (1.3.6.1.5.5.7.3.2)
Secure Email (1.3.6.1.5.5.7.3.4)
2.5.29.32: Flags = 0, Length = 3c
Certificate Policies
[1]Certificate Policy:
Policy Identifier=2.16.840.1.114412.4.1.2
[1,1]Policy Qualifier Info:
Policy Qualifier Id=CPS
Qualifier:
https://www.digicert.com/CPS
2.5.29.31: Flags = 0, Length = 80
CRL Distribution Points
[1]CRL Distribution Point
Distribution Point Name:
Full Name:
URL=http://crl3.digicert.com/DigiCertSHA2AssuredIDCA-g2.crl
[2]CRL Distribution Point
Distribution Point Name:
Full Name:
URL=http://crl4.digicert.com/DigiCertSHA2AssuredIDCA-g2.crl
1.3.6.1.5.5.7.1.1: Flags = 0, Length = 6d
Authority Information Access
[1]Authority Info Access
Access Method=On-line Certificate Status Protocol (1.3.6.1.5.5.7.48.1)
Alternative Name:
URL=http://ocsp.digicert.com
[2]Authority Info Access
Access Method=Certification Authority Issuer (1.3.6.1.5.5.7.48.2)
Alternative Name:
URL=http://cacerts.digicert.com/DigiCertSHA2AssuredIDCA.crt
Signature Algorithm:
Algorithm ObjectId: 1.2.840.113549.1.1.11 sha256RSA
Algorithm Parameters:
05 00
Signature: UnusedBits=0
0000 63 e6 69 f6 1c 10 31 13 28 11 4e 14 19 6b a8 00
0010 44 bd 9e 39 2e 4a 6b 64 96 f2 c0 a7 57 56 58 3e
0020 02 f8 7b 44 cf e3 0e ab 81 02 4d 3c 4f 68 7b 49
0030 f3 bf 98 1c 99 93 0e 56 ea c2 9d b4 c8 c6 67 0a
0040 3e a8 96 4d 0f 70 30 9d 58 3d bd 6b 4e e7 3f d2
0050 cd 9f dc 0a 28 b6 ad 5f 2e 52 c5 f1 93 51 f8 bc
0060 18 5e 6f 97 86 a5 c1 47 c2 be 2f fa a1 a6 f9 6c
0070 d1 de 39 4a 06 13 a0 36 9d 3d 17 4f 21 55 5b dc
0080 09 b0 12 76 71 84 f6 5e 0e d3 f2 25 c4 9c 2a ea
0090 50 18 80 af bc 57 61 3f 12 49 5d 82 2e 02 59 15
00a0 bd 22 8b 6f 8b 2d df 5b 78 80 d8 9c 93 91 af 67
00b0 2e 45 03 9d cc e7 64 34 23 8e 0f ff 9c e8 96 65
00c0 e6 1b 40 af b0 6b 22 90 96 df 62 e0 1f 5e f9 e1
00d0 1d 06 d4 7e d2 93 ea 15 73 a1 e7 f9 a4 25 b2 df
00e0 c2 6b 38 86 f5 7a 49 b0 76 d7 c4 e7 48 95 2d 93
00f0 d4 e9 69 c6 b1 be f5 ed c8 7c 9e f5 e9 4f 06 04
Non-root Certificate
Key Id Hash(rfc-sha1): 9fa08ae0fd0c658ce7ce7fdc2c328442e00aa9df
Key Id Hash(sha1): c144b8c08863dbf0894a024183e038ac63063e9e
Key Id Hash(md5): 8a51a0672e5d8f8b34a4e82964c3c032
Key Id Hash(sha256): dbcedcfb43684c49f715462e07c207733dc0a6afcd7de7fb0858822e55becc73
Cert Hash(md5): 5bcdf4bf4ebf5b364c543e667aec438f
Cert Hash(sha1): 8b6f616b5f5629c099ae6563047f981eaf0eb740
Cert Hash(sha256): 46c3a59ec923516dac7522ffa944f69836c6acd9d273bd475619f1a0701e42d7
Signature Hash: 5d1dd5831ed2eea1419b7c12e5ccf319075f40c7984eab78a95e180a79615a46
CERT_SMART_CARD_READER_PROP_ID(101):
Microsoft\SmartCard\Reader\Images\E55FA0F4F9280FF39B7D2865DE7F99C6F2C86126C3F5506DF391167EBEB233E1.bmp
CERT_SCARD_PIN_ID_PROP_ID(90):
01 00 00 00 ....
CERT_ISSUER_PUBLIC_KEY_MD5_HASH_PROP_ID(24):
a6b914b841db11654e21d74377ebf1a5
CERT_SUBJECT_PUBLIC_KEY_MD5_HASH_PROP_ID(25):
8a51a0672e5d8f8b34a4e82964c3c032
CERT_MD5_HASH_PROP_ID(4):
5bcdf4bf4ebf5b364c543e667aec438f
CERT_SHA1_HASH_PROP_ID(3):
8b6f616b5f5629c099ae6563047f981eaf0eb740
CERT_KEY_IDENTIFIER_PROP_ID(20):
9fa08ae0fd0c658ce7ce7fdc2c328442e00aa9df
CERT_SIGNATURE_HASH_PROP_ID(15) disallowedHash:
5d1dd5831ed2eea1419b7c12e5ccf319075f40c7984eab78a95e180a79615a46
CERT_SUBJECT_PUB_KEY_BIT_LENGTH_PROP_ID(92):
0x00000800 (2048)
CERT_OCSP_CACHE_PREFIX_PROP_ID(75):
AEE5DC149DDF37EE2C67DDA6CC838E13_
CERT_DESCRIPTION_PROP_ID(13):
descr
CERT_SCARD_PIN_INFO_PROP_ID(91):
06 00 00 00 00 00 00 00 00 00 00 00 02 00 00 00 ................
04 00 00 00 06 00 00 00 00 00 00 00 00 00 00 00 ................
00 00 00 00 ....
CERT_KEY_PROV_INFO_PROP_ID(2):
Key Container = te-67e0cee2-efce-41bf-bcef-9203a2f5d17a
Provider = Athena ASECard Crypto CSP
ProviderType = 1
Flags = 0
KeySpec = 1 -- AT_KEYEXCHANGE
CERT_KEY_CLASSIFICATION_PROP_ID(120):
CertKeyType = 2
KeyTypePhysicalSmartCard -- 2
CERT_ACCESS_STATE_PROP_ID(14):
AccessState = 2
CERT_ACCESS_STATE_SYSTEM_STORE_FLAG -- 2
Provider = Athena ASECard Crypto CSP
ProviderType = 1
RSA
PP_KEYSTORAGE = 1
CRYPT_SEC_DESCR -- 1
KP_PERMISSIONS = 1
CRYPT_ENCRYPT -- 1
D:(A;OICIID;GAGR;;;SY)(A;OICIID;GAGR;;;BA)(A;OICIID;GAGR;;;S-1-5-21-516845474-3315778190-3767122921-1000)
Allow Full Control *******\*******
Allow Full Control *******\*******
Allow Full Control *******\*******
Private key is NOT exportable
Encryption test passed
CertUtil: -store command completed successfully.
PS C:\>
In addition to certificate itself, certutil displays all certificate store-attached properties. Properties goes after “signature hash” line. In the store object identifier you pass object’s thumbprint. Microsoft CryptUI dynamically adds Thumbprint field (which is not a part of cryptographic objects):
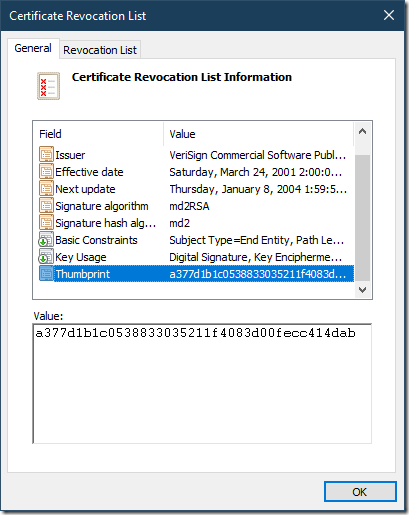
You will supply this value to certutil:
PS C:\> certutil -v -store CA "a377d1b1c0538833035211f4083d00fecc414dab"
CA "Intermediate Certification Authorities"
================ CRL 0 ================
X509 Certificate Revocation List:
Version: 2
Signature Algorithm:
Algorithm ObjectId: 1.2.840.113549.1.1.2 md2RSA
Algorithm Parameters:
05 00
Issuer:
OU=VeriSign Commercial Software Publishers CA
O=VeriSign, Inc.
L=Internet
Name Hash(sha1): 12d2cb85c5e62f9aa7591e2ddaa44c987de5abbc
Name Hash(md5): 177f789e96523e206c796917c848d50f
ThisUpdate: 3/24/2001 2:00 AM
NextUpdate: 1/8/2004 1:59 AM
CRL Entries: 3
Serial Number: 1b5190f73724399c9254cd424637996a
Revocation Date: 1/30/2001 2:01 AM
Serial Number: 750e40ff97f047edf556c7084eb1abfd
Revocation Date: 1/31/2001 2:00 AM
Serial Number: 77e65a4359935d5f7a75801acdadc222
Revocation Date: 8/31/2000 2:00 AM
CRL Extensions: 2
2.5.29.19: Flags = 0, Length = 2
Basic Constraints
Subject Type=End Entity
Path Length Constraint=None
2.5.29.15: Flags = 0, Length = 4
Key Usage
Digital Signature, Key Encipherment (a0)
Signature Algorithm:
Algorithm ObjectId: 1.2.840.113549.1.1.2 md2RSA
Algorithm Parameters:
05 00
Signature: UnusedBits=0
0000 cd 9c 9c 3b 63 51 4d 43 67 08 ea c9 7a ab 07 15
0010 be 97 0c 92 c8 b1 4e 06 a0 52 28 82 94 e3 a3 72
0020 1d 66 18 19 f5 43 80 d7 8f 64 fb 6f 30 b4 22 e4
0030 84 f1 ad 6e 8e 75 0c e6 15 22 cd 5e aa a7 7e 3d
0040 21 06 7f 90 0a f5 bd 08 c4 0d 22 62 91 6a 74 46
0050 ac 6a e7 9d 39 c1 4b 0c cf 8a 89 9b cf 0e 83 1e
0060 21 7e 67 fa 0c c0 ab 65 0e dd 19 59 da f9 bb 64
0070 bf 11 b8 5d 48 54 88 3d 4a 91 6d 16 fc e8 2c 18
CRL Hash(md5): 4f0234ad0ee37e3182d35b0ebfafbc3e
CRL Hash(sha1): a377d1b1c0538833035211f4083d00fecc414dab
CRL Hash(sha256): 35904127bf39e9de2977deb4c102aab200c547fe5ad994ecb7d89eb20b435861
Signature Hash: bf4a2e7c9d74f86c314d605d4184cca6
CERT_SHA1_HASH_PROP_ID(3):
a377d1b1c0538833035211f4083d00fecc414dab
CertUtil: -store command completed successfully.
PS C:\>
We didn’t use -user modifier, because this particular CRL is installed in the local machine store, not current user store (certutil defaults to local machine store).
What does certutil -scroots update do? The output looks different when run in a domain joined machine compared to a non-domain machine.
I'm not clearly sure what exactly it does. It isn't something I ever used.
What is another main cryptographic utilities in Windows? Is it SignTool.exe?
> Is it SignTool.exe?
SignTool is not shipped with Windows, it is part of SDK which you need to download and install.
Thanks so much!!
Can you please tell what is another main cryptographic utilities in Windows? Thanks.
Your blog has been really help.
How would I be able to view the Signature Hash Algorithm property using Certutil?
> How would I be able to view the Signature Hash Algorithm property using Certutil?
Signature and signature hash algorithm are actually the same thing, hash algorithm just doesn't include public key algorithm name.
I use a certutil command to dump certificates issued by a particular template to csv with the following command:
certutil -view -restrict "CertificateTemplate = number" -out RequestID,CommonName,NotBefore,NotAfter csv > C:\FileLocation.csv
I would like to be able add subject alternative names to this output and haven't figured out how to get the Ext fieled added.
This took forever to figure out, but I'm recording it here to at least help the next poor sucker that wants to get this.
# View the extensions for a specific cert
# <RequestID> is the RequestID for the actual cert (can be hex or decimal value)
certutil -config -View -restrict "ExtensionRequestId==<RequestID>" EXT
# View the Subject Alternative Name extension
certutil -config -View -restrict "ExtensionRequestId==<RequestID>,ExtensionName=2.5.29.17" -out "ExtensionName,ExtensionRawValue" EXT
Post your comment:




Comments: