Posts on this page:
- OCSP Client Tool — advanced stuff
- OCSP Client Tool
- Windows Server 2012 RC, Active Directory Certificate Services features
- You cannot submit a certificate request generated by Exchange Management Console (EMC) or Exchange Management Shell (EMS) to Microsoft Certificate Ser
- Digging into digital signatures (part 1)
Hello S-1-1-0 again, I'm back!
In the first part we discovered basic OCSP requests and responses. Today's stories:
- Nonce
- Service Locator
Nonce
By default, Online Responder may pre-cache OCSP response for particular certificate, especially if the certificate is used very frequently (for example, SSL certificate at login.live.com) until it (response) is expired. This reduces server load, because there is no need to sign the same response for each incoming request. And this behavior is recommended by RFC5019. Here is an example for StartSSL/StartCom SSL certificate:
Read more →
Hello folks, PowerShell Crypto Guy is again on the board! Today I want to talk about a useful OCSP Client Tool which is available in my PowerShell PKI module.
A long time ago in a galaxy far, far away....
A time ago I started Online Responder deployment and was faced the problem that there are no good tools to test it's configuration and how it works. PKIView.msc and certutil.exe just can tell whether the OCSP is functional or not. No details about request and/or response details. After a little research I found pretty useful and nice tool called Ascertia OCSP Client Tool. Actually this is a great tool with a lot of powerful features, including raw ASN.1 traces and so on. I thought that it is worth to buy the tool and contacted their sellers. Holy ****, the price killed me. They asked about 1,800 (1.8k) euros for a single license! Even though the tool is very cool, I wasn't ready to spend such money for it. But, if you manage Lorne Greene or Johnny Cash, then Ascertia's product may be for you.
Read more →
A little note about features in Windows Server 2012 AD CS. Only three major improvements are available:
- All Windows Server 2012 SKUs supports all AD CS features.
From version to version, Microsoft introduces new features in AD CS, however not all are available in all SKUs. For example, in Windows Server 2008 an Online Responder service was added, but was available on Enterprise and Datacenter SKUs. The same thing as with Cross-forest certificate enrollment in Windows Server 2008 R2. Only Enterprise and Datacenter SKUs supported these features. From now, Windows Server 2012 Standard Edition will support *all* features in AD CS. This means that the following roles are available to any who has Windows Server 2012:
Read more →
SYMPTOMS
Consider the following scenario. You create certificate certificate by using either Exchange Management Console (EMC) or Exchange Management Shell (EMS) and save it to a file. When you attempt to submit certificate request to a Windows-based Certification Authority (CA) (also known as Microsoft Certificate Services), you may receive error message. If CA server runs on Windows Server 2003 (R2) or Windows Server 2008, you receive the following message:
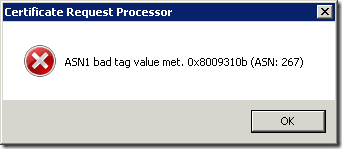
Read more →
Hi folks!
A time ago I wrote a high-level description about the signatures in Digital signatures blog post. And today I want to demonstrate how this works in a real world.
In a real world there are too many signature types, including RSA signatures (plain), Authenticode, XML, Document-specific (MS Word, Adobe PDF, etc.). The simplest signature type is plain RSA signatures. This type of signatures is widely used in PKI (certificates, CRLs, signed BLOBs and so on). In ASN.1 modules (as well as in unmanaged structures), signed BLOB is written like this:
Read more →



