Posts on this page:
- Digging into digital signatures (part 1)
- Exploring enhanced features in X509CRL2 class
- PS PKI v1.5 is released!
- How to programmatically extract CDP, AIA and OCSP URLs from a digital certificate
- Retrieve timestamp attribute from digital signature
Hi folks!
A time ago I wrote a high-level description about the signatures in Digital signatures blog post. And today I want to demonstrate how this works in a real world.
In a real world there are too many signature types, including RSA signatures (plain), Authenticode, XML, Document-specific (MS Word, Adobe PDF, etc.). The simplest signature type is plain RSA signatures. This type of signatures is widely used in PKI (certificates, CRLs, signed BLOBs and so on). In ASN.1 modules (as well as in unmanaged structures), signed BLOB is written like this:
Read more →
Hello S-1-1-0!
Today I'll describe some interesting features implemented in X509CRL2 class. This class is available within my PowerShell PKI module only (is not a part of .NET Framework).
Verify CRL signature
A time ago a came into an issue with CRL copy to remote web server.
My internal CA publish CRLs to a local drive and custom script copies it to all required distribution points (internal and external web servers). And one day certificate validation failed due to Revocation Offline error. I've checked that CRL is correctly formed, is time valid and so on. But certificate chaining engine still reported mentioned error. Detailed investigation showed that unexpected network-level error occurred during file copy over internet and CRL signature become invalid. Since CRL object contains only signature value without signer certificate, normally it is impossible to verify whether the CRL signature is valid. In order to verify signature, you must obtain signer certificate (issuing CA certificate) and use custom steps to verify the signature.
Read more →
I'm glad to announce that another build of my PowerShell PKI module is released! This release introduces new vision of the module evolution. Since now, it is not only a set of PowerShell commands, but the set of .NET APIs that can be used to extend existing commands. Let's go with details.
Breaking changes
Due to the fact that Windows PKI team decided to name their own module in Windows Server 8 exactly as my module, I was forced to rename it. This is very disappointing thing. Now the module is named PSPKI. On the other side, PKI was too generic name and new name exposes usage area (PowerShell or simply PS).
Installation experience
Previously I've used a private signing certificate (issued by one of my internal CAs) to sign module files. Now I switched it to a certificate issued by common trusted CA (DigiCert).
Read more →
Hi folks! Today I want to demonstrate some useful stuff with CryptoAPI and PowerShell to extract CDP, AIA and OCSP URLs from a digital certificate.
The start point for us is CryptGetObjectUrl function:
BOOL WINAPI CryptGetObjectUrl( __in LPCSTR pszUrlOid, __in LPVOID pvPara, __in DWORD dwFlags, __out PCRYPT_URL_ARRAY pUrlArray, __inout DWORD *pcbUrlArray, __out PCRYPT_URL_INFO pUrlInfo, __inout DWORD *pcbUrlInfo, __reserved LPVOID pvReserved );
as a pszUrlOid argument we will use the following constants: URL_OID_CERTIFICATE_ISSUER (from AIA extension) and URL_OID_CERTIFICATE_OCSP_AND_CRL_DIST_POINT. Constant values (as per Wincrypt.h) are:
Read more →
One friend of mine asked about how to get signature creation time in PowerShell. When we sign a file, optionally (but recommended) we can timestamp the signature, thus approving that the file was signed at the certain moment and wasn't re-signed later. Some useful details about signatures and timestamps you can read in my previous article: Digital signatures.
Here is what we see in the UI:
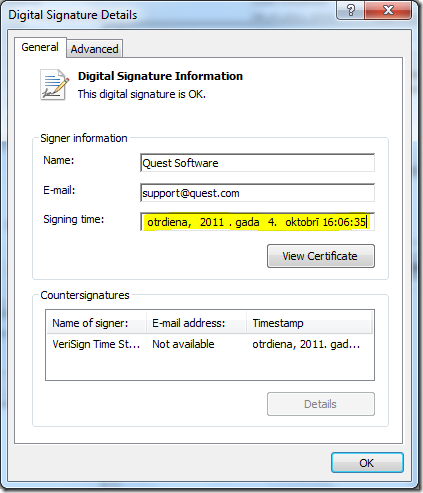
We see the following fields:
Read more →



