Posts on this page:
- PS PKI v1.8 is released!
- Windows Server 2012 RC, Active Directory Certificate Services features
- How to retrieve certificate purposes property with CryptoAPI and PowerShell
- You cannot submit a certificate request generated by Exchange Management Console (EMC) or Exchange Management Shell (EMS) to Microsoft Certificate Ser
- How to register custom Object Identifier
Hi S-1-1-0! Today I've released a new version of my PowerShell PKI module.
New commands
Unlike previous versions, this version do not introduce any new commands.
Existing code changes
Instead, I take a time to make the module more consistent. As a part of this work I revisited all help topics. Now all help content is more accurate and consistent. Also I've added additional examples (where I considered this as important) and clarified existing parts.
After discussions with Windows PKI team, I was forced to change the things in Add-ExtensionList and Remove-ExtensionList. CAExtension and UserExtension parameters were renamed to EnabledExtension and OfflineExtension respectively. Parameter descriptions can be found in built-in and online help topics. ExtensionList object properties are renamed accordingly to make them consistent with parameters.
Read more →
A little note about features in Windows Server 2012 AD CS. Only three major improvements are available:
- All Windows Server 2012 SKUs supports all AD CS features.
From version to version, Microsoft introduces new features in AD CS, however not all are available in all SKUs. For example, in Windows Server 2008 an Online Responder service was added, but was available on Enterprise and Datacenter SKUs. The same thing as with Cross-forest certificate enrollment in Windows Server 2008 R2. Only Enterprise and Datacenter SKUs supported these features. From now, Windows Server 2012 Standard Edition will support *all* features in AD CS. This means that the following roles are available to any who has Windows Server 2012:
Read more →
Hello crypto world! One my colleague asked me about how to get certificate purposes property. Here is a little intro.
Certificate purposes are (mainly) limited by Enhanced Key Usages extension:
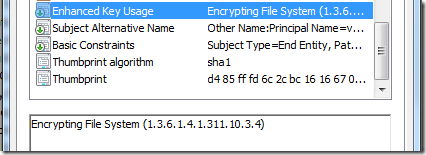
That is true. In certain cases it is reasonable to limit certificate purposes to a subset of purposes that are allowed in EKU extension. For example, in many and many CAs are allowed for any purpose (All Application Policies) and you can limit it's purposes to a limited set:
Read more →
SYMPTOMS
Consider the following scenario. You create certificate certificate by using either Exchange Management Console (EMC) or Exchange Management Shell (EMS) and save it to a file. When you attempt to submit certificate request to a Windows-based Certification Authority (CA) (also known as Microsoft Certificate Services), you may receive error message. If CA server runs on Windows Server 2003 (R2) or Windows Server 2008, you receive the following message:
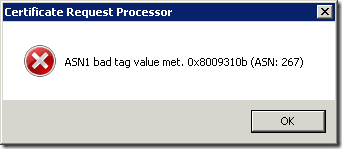
Read more →
Today I will discuss about how to register custom object identifier on a local computer. Why you need this? .NET Oid class which can resolve many common object identifiers to their friendly names and vice versa. However, not all OIDs are registered there. For example, RDS (Remote Desktop Services, former Terminal Services) team introduces special OID for RDP-SSL enhanced key usage with OID=1.3.6.1.4.1.311.54.1.2:
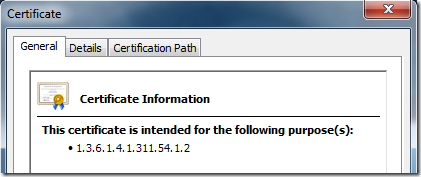
If you have Active Directory domain and at least one Enterprise CA, you can define this OID in Active Directory (by editing certificate template). But what if you don't have Active Directory or internal Enterprise CA? Then PowerShell and CryptoAPI is the answer here!
Read more →



