Posts on this page:
- Reading multiple signatures from signed file with PowerShell
- Manage pending certificate requests in ADCS with PowerShell
- How to properly delete certificate with private key in PowerShell
- Sign data with ECC (CNG) certificate
- Configure IIS Web Administration to use centralized SSL certificate
Hello S-1-1-0, it’s time for another blog post. Another PowerShell and CryptoAPI blog post.
Identifying the problem
Recently I had a trivial (or non-trivial?) challenge: read multiple signatures from signed files. Usually files have only one signature:
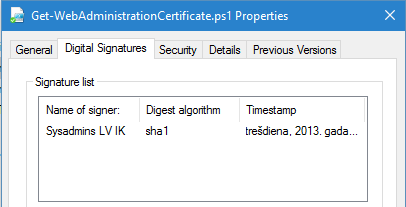
Read more →
I think, I have to publish several articles that would cover common PKI/ADCS administration tasks with PowerShell by using my PowerShell PKI module (of course!). Today I'll cover very simple, but very common task: managing pending certificate requests.
In this post we would propose the following scenario:
- IIS admin requested certificate for internal SharePoint portal
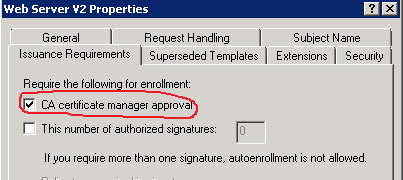
- Certificate template is configured to require CA manager approval to issue the certificate.
- No certificate will be issued until CA manager review and approve the request.
Just to make it clear, CA manager approval is configured in the certificate template, as follows:
you, as CA manager, received notification about incoming certificate request. Your task is to review the certificate request to ensure that it is properly constructed and conforms internal security policies and then make decision: approve or deny certificate request. You can do this by using Certification Authority MMC snap-in, but this would require a lot of clicks and without having a chance to automate this. Another solution that includes PowerShell offers you great automation capabilites.
Read more →
About the problem
PowerShell MVP, Adam Bertram with his recent tweet inspired me to write this blog post. I realized that I see a lot of articles which describe how to delete certificate from certificate store, but never saw article that would describe how to do it properly.
Let’s recall what is wrong here. Years ago I wrote a blog post: The case of accidentally deleted user certificates that describes steps how to restore deleted certificate with private key by having a backup certificate only with public key. I explained why you can use certificate with just public key to restore bindings to private key. The answer was: when you delete certificate by using standard means (certificate store management functions in CryptoAPI), the private key is not deleted! Standard tools includes: Certificates MMC snap-in, X509Store class in .NET, certutil, etc., all they use Certificate and Certificate Store Functions. Our goal now is to fill the gap and provide an ability to remove private key along with certificate when you work in PowerShell.
Read more →
In previous post I talked about weirdness in CNG support in .NET and showed an example how to fill the gaps in .NET. That was just an example. Today I will show how to perform basic cryptographic operations with CNG in PowerShell and other CLR languages (C#, VB.NET). PowerShell is built on top of CLR, so the techniques are almost identical, despite a bit different syntax.
So, today I will show how to sign the data with CNG certificate. The easiest way is to use NCrypt* unmanaged function family exposed by NCRYPT.DLL.
Read more →
Many of you use IIS web servers in corporate network for various purposes, for example, to host internal/external web site, ADCS web services, OCSP, WSUS and this list is very long. It is common to manage them all from a centralized place, for example, from web server administrator’s computer. In other words, IIS servers are not managed directly from console.
The problem
By default IIS do not allow remote administration, you have to enable it by starting (and, likely, setting start type to Automatic) Web Management Service (WMSVC). Ok, you started the service on a web server and attempt to connect to the server from remote IIS management console:
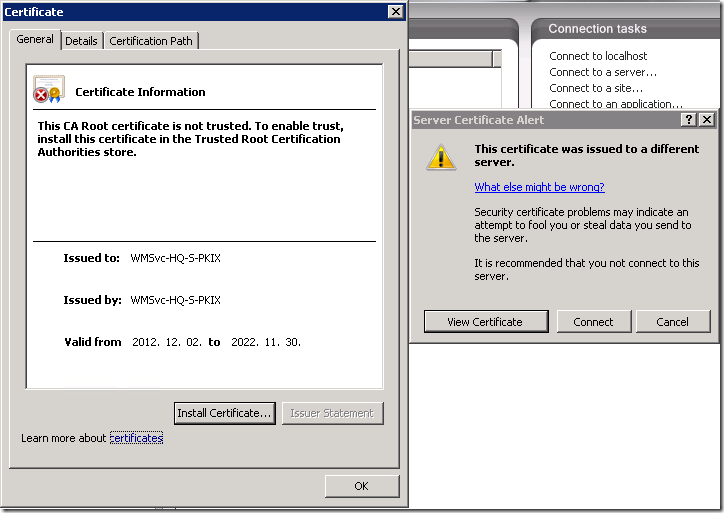
Read more →



