Posts on this page:
- Reading multiple signatures from signed file with PowerShell
- Manage pending certificate requests in ADCS with PowerShell
- How to read ADCS Enrollment Agent/Certificate Manager rights in PowerShell
- How to properly delete certificate with private key in PowerShell
- Test web server SSL/TLS protocol support with PowerShell
Hello S-1-1-0, it’s time for another blog post. Another PowerShell and CryptoAPI blog post.
Identifying the problem
Recently I had a trivial (or non-trivial?) challenge: read multiple signatures from signed files. Usually files have only one signature:
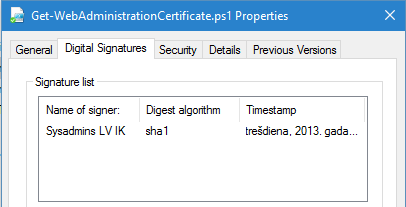
Read more →
I think, I have to publish several articles that would cover common PKI/ADCS administration tasks with PowerShell by using my PowerShell PKI module (of course!). Today I'll cover very simple, but very common task: managing pending certificate requests.
In this post we would propose the following scenario:
- IIS admin requested certificate for internal SharePoint portal
- Certificate template is configured to require CA manager approval to issue the certificate.
- No certificate will be issued until CA manager review and approve the request.
Just to make it clear, CA manager approval is configured in the certificate template, as follows:
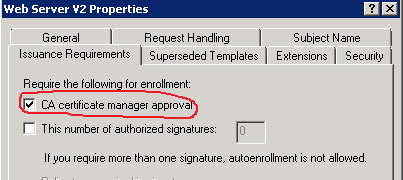
you, as CA manager, received notification about incoming certificate request. Your task is to review the certificate request to ensure that it is properly constructed and conforms internal security policies and then make decision: approve or deny certificate request. You can do this by using Certification Authority MMC snap-in, but this would require a lot of clicks and without having a chance to automate this. Another solution that includes PowerShell offers you great automation capabilites.
Read more →
Recently I was asked about how to read Enrollment Agent Rights and Certificate Manager Restrictions in ADCS. At first, I would like to make a little introduction about the subject.
Enrollment Agents
With Active Directory Certificate Services (ADCS) you can designate one or more enrollment agents to enroll on behalf of other users. One of the most common scenarios is smart card provisioning. Suppose, you purchased smart cards and plan to issue them to employees. You will designate one or more highly trusted persons who will:
- instruct employees about smart card usage policies;
- register smart card serial number/other data in the accounting system (some certificate lifecycle management system);
- prepare smart card for use (print labels and so on);
- install certificate for another employee.
Enrollment Agent Restrictions cover the last point in the list. Restrictions define three major parts:
Read more →
About the problem
PowerShell MVP, Adam Bertram with his recent tweet inspired me to write this blog post. I realized that I see a lot of articles which describe how to delete certificate from certificate store, but never saw article that would describe how to do it properly.
Let’s recall what is wrong here. Years ago I wrote a blog post: The case of accidentally deleted user certificates that describes steps how to restore deleted certificate with private key by having a backup certificate only with public key. I explained why you can use certificate with just public key to restore bindings to private key. The answer was: when you delete certificate by using standard means (certificate store management functions in CryptoAPI), the private key is not deleted! Standard tools includes: Certificates MMC snap-in, X509Store class in .NET, certutil, etc., all they use Certificate and Certificate Store Functions. Our goal now is to fill the gap and provide an ability to remove private key along with certificate when you work in PowerShell.
Read more →
Recently I was tasked to configure SSL/TLS protocols and cipher suites for internal web servers via Group Policy. At first, we collected a list of web server and web client applications to determine the weakest possible SSL/TLS protocols. Once the list was complete, we deployed sample policy in test OU and finally applied them to the rest domain.
Now I was tasked to scan web servers to determine if they match new security policy. In order to minimize my effort in testing, I wrote a simple PowerShell script that accepts a list of web URLs and tests each host with a list of SSL protocols: SSLv2, SSLv3, TLS 1.0, TLS 1.1 and TLS 1.2. Here is a sample code:
Read more →



