Posts on this page:
- PowerShell Cmdlet Help Editor 1.0
- Bulk file signing with PowerShell and user interface
- Updated Test-WebServerSSL function (C#)
- How to convert PKCS#12/PFX to PEM format
- PowerShell File Checksum Integrity Verifier (PsFCIV) 2.0
Update 18.11.2013: pointed URL to a CodePlex project page.
Phinally!!!
Abstract
As you already know, last time I worked on my next PowerShell PKI module and encountered in an issue with Microsoft’s Cmdlet Help Editor. When I tried to open my module (and any other built-in module) I got very nice message:
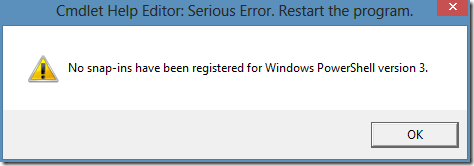
Ok, I tried to download sources (thanks, they are available for download) and was stuck with WPF. I heard that WPF is a modern replacement for WinForms, and that was the only what I knew about WPF. I was able to fix mentioned message issue, but failed with application layout. The form has fixed size and no scroll bars. So I couldn’t access textboxes and commands which are outside of my screen (even if I worked on a 1680*1050 display). And I decided to create my own Help Editor with with “blackjack and hookers”.
Read more →
Hello S-1-1-0! Today I would like to present a PowerShell script that allows you to add multiple files to a form and sign them using Authenticode signature.
As you already know, I’m using Software Restriction Policies and Applocker to prevent users (including myself) from running unauthorized applications and scripts. I’m using various options to allow certain applications and scripts in group policy. In certain cases I’m using hash rules, but mostly (as possible) I’m using digital signatures and publisher/certificate rules.
Since I’m writing a lot of PowerShell scripts I have to sign them in user-friendly way. Yes, there is Set-AuthenticodeSignature cmdlet, but I dislike to specify file path and signing certificate each time I want to sign something. Previously I used a nice function that adds a context menu to Windows Explorer and signs file: Подписывание скриптов PowerShell – практическая реализация (часть 2). However this script adds context menu only for PS1 files, while there are a lot of other file types that supports digital signatures. To address this question I wrote a little WinForms PowerShell script that allows me to perform file signing very easy. At first I start with screenshots.
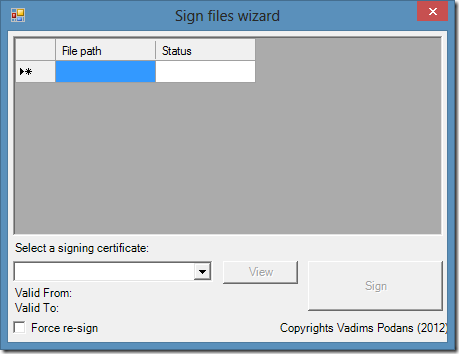
Read more →
Hi again! Recently I faced an issue with my Test-WebServerSSL function which is also available in my Powershell PKI module.
Issue
In certain cases, the function returns certificate chain errors, while Internet Explorer (as well as other web browsers) works normally and do not report anything wrong. For example, you can open https://www.nic.lv/ web site without any issues in your web browser. When you run Test-WebServerSSL function against this web site, you get the following:
Read more →
Hello folks! If you are longing for CryptoAPI stuff here, then you are on the right page. Here you will see another bunch of CryptoAPI, PowerShell and p/invoke hardcore.
Today’s subject is to convert PFX file to PEM format. A time ago I wrote a function that does opposite — converts PEM to PFX: How to convert PEM file to a CryptoAPI compatible format. Read this post to get information about CryptoAPI structures and ASN modules for PKCS#1 and PKCS#8 structures.
The script below performs the following tasks:
- Reads certificate or certificate file. If the file is not valid PFX or certificate hasn’t associated private key, an exception will be thrown.
- Acquires private key (via unmanaged function calls) and attempts to export raw private key from CSP. If the private key is not marked as exportable or it is stored on smart card, an error will be thrown.
- Inspects CryptoAPI private key blob as described here: RSA/Schannel Key BLOBs, removes header, reads raw private key and splits it to components (modulus, primes, exponents, coefficient). Each component is stored in separate variable.
- Generates required ASN structures according to output type by using basic ASN encoder.
- composes certificate and private key and saves them to file.
Read more →
3 years ago a friend of mine asked me about how to enhance FCIV.exe utility functionality with PowerShell. Microsoft is not developing this tool anymore and you have to write your own tools or wrappers for fciv.exe to get required functionality.
I decided to write completely new tool from scratch by using only native PowerShell code. First version of PsFCIV was released about 3 years ago only for Russian-language audience. However there are many requests from English-language visitors. For example, users request new hashing algorithm support (SHA2 family) and other checking options, like file size and last modification timestamp checking. I made a lot of performance and reliability improvements, so new version works much faster than PsFCIV 1.0. Also I added support for SHA2 hashing algorithms. As the result, I was able to release a new updated PsFCIV 2.0 tool on TechNet Gallery:
Read more →



