In the previous blog posting (Operating a Windows PKI: Certification Authority Certificate Lifecycle and Renewals) I covered considerations for the CA Certificates lifecycle and when CA certificates should be renewed. In this blog posting, I am going to cover some additional considerations and walkthrough the process of renewing CA Certificates.
CRLNameSuffix
Two important things to remember. If you renew a CA certificate, you are going to have multiple CA certificates, the previous certificate and the renewed certificate. If you renew a CA certificate with a New Key Pair, the CA is going to have to sign multiple CRLs. It will have to sign CRLs with the previous key, assuming that CA certificate is time valid. Also, the CA will need to sign CRLs with the new key pair.
To ensure that the renewal works properties you must have the CRLPublicationURLs registry key configured properly. Specifically, when you configure the CA to publish CRLs or to list an HTTP location in the CDP extension you will want to ensure that the CRLNameSuffix property is defined. For example, below is the post-configuration script for a Root CA:
certutil -setreg CA\CRLPublicationURLs "1:%WINDIR%\system32\CertSrv\CertEnroll\%%3%%8%%9.crl\n2:http://pki.fourthcoffee.com/certenroll/%%3%%8%%9.crl\n10:ldap:///CN=%%7%%8,CN=%%2,CN=CDP,CN=Public Key Services,CN=Services,%%6%%10"
In this line:
1:%WINDIR%\system32\CertSrv\CertEnroll\%%3%%8%%9.crl
And this line:
2:http://pki.fourthcoffee.com/certenroll/%%3%%8%%9.crl
You will notice that there is a %%8 before %%9.crl. After these scripts are run the additional % signs will be stripped. The additional % are required for the script since it is a batch file. So, the resulting variable is %8. The variable %8 stands for CRLNameSuffix. This variable will tell the CA to affix an incremental number to CRL files if they are signed by a new key pair. So, the CRL signed by the CAs first key will be named “FourthCoffee Root Certification Authority.crl”. The CRL signed by the second key will be named “FourthCoffee Root Certification Authority(1).crl, and so on.
Changing the CA Certificates Validity Period
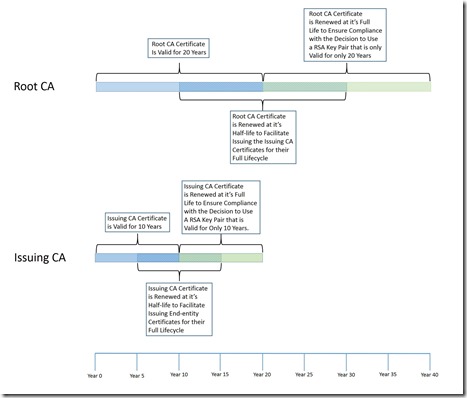
In rare circumstances you may want to change how long CA Certificates are valid for, when renewing the CA certificate. So, let’s use the example of a two tier PKI hierarchy. If you want to modify the validity period for the subordinate/issuing CA, you will have to modify the ValidityPeriodUnits and ValidityPeriod settings on the Root CA. These two registry settings will determine for how long the Root CA issues certificates. Validity PeriodUnits is set to a number and ValidityPeriod is set to a measurement of time. For example, if ValidityPeriodUnits is set to “10”, and ValidityPeriod is set to “Years” the Root CA will issue certificates that are valid for 10 years. Both of these settings are located in the registry at HKLM\System\CurrentControlSet\Services\CertSvc\Configuration\<CAName>\. Optionally, the registry can be configured with the “certutil –setreg” command.
To change the Validity Period for the Root CA you can configure a CAPolicy.inf. To create a CAPolicy.inf file that changes the lifietime of the certificate to 30 years, you would type the following into a text file, and save it with the name CAPolicy.inf in the C:\Windows directory,:
[Version]
Signature= "$Windows NT$"
[Certsrv_Server]
RenewalValidityPeriod=Years
RenewalValidityPeriodUnits=30
Then you would renew the CA certificate.
However, I have not been able to alter the resulting CA certificates lifetime using this method. I have, only tested this with Windows Server 2012. It is my understanding that his has worked in previous versions of the OS but have not been able to verify. Additional information on the CAPolicy.inf file is available here: http://blogs.technet.com/b/askds/archive/2009/10/15/windows-server-2008-r2-capolicy-inf-syntax.aspx
Changing the CA Certificates Key Size
The following steps can be taken to change the Key Size for a renewed CA certificate. First, it should be noted that if you are changing the key size, you are changing the key. Therefore, to increase the Key Size you will need to renew the CA certificate with a new key pair.
The first step is to create a CAPolicy.inf file on the CA for which you wish to increase the Key Size. The format of the file, is as follows:
[Version]
Signature= "$Windows NT$"
[Certsrv_Server]
RenewalKeyLength=4096
You can change the RenewalKeyLength to the size of the key desired.
Next, you will renew the CA certificate with a new key pair. Instructions for CA Certificate renewal, will be covered later in the article.
Changing the CA Certificates Hashing Algorithm
I have had one situation where a customer wanted to change the Hash Algorithm for a CA Certificate. The customer had installed an Issuing CA. The Issuing CA’s certificate used SHA-256 as the hash algorithm. The customer wanted to change the hash algorithm to the less secure, but more compatible SHA1. Assuming, a two-tier hierarchy, you can change the Hash Algorithm in the CA certificate on either the Root or Issuing CA by modifying the following registry key HKLM\System\CurrentControlSet\Services\CertSvc\Configuration\<CAName>\CSP\HashAlgorithm on the Root CA and then renewing either the Issuing or Root CA, depending on which one for which you are changing the Hash Algorithm.
The customer I was working with had the Hashing Algorithm on the Issuing CA set to SHA-256. So, we changed the HashAlgorithm registry key on the Root CA from “SHA256” to “SHA1”.
Renewing a Root CA Certificate
The video below covers the steps required to renew a Root CA Certificate.
Renewing a Root CA Certificate
Renewing an Issuing CA Certificate
The video below covers the steps required to renew a Root CA Certificate
Renewing a Issuing CA Certificate
Conclusion
You should now have the information and steps you need to understand CA Certificates Lifecycle and how to renew CA Certificates.