| Original URL: | https://blogs.technet.microsoft.com/xdot509/2013/06/18/operating-a-pki-revoking-orphaned-certificates/ |
| Post name: | Operating a PKI: Revoking Orphaned Certificates |
| Original author: | chdelay |
| Posting date: | 2013-06-18T10:04:03+00:00 |
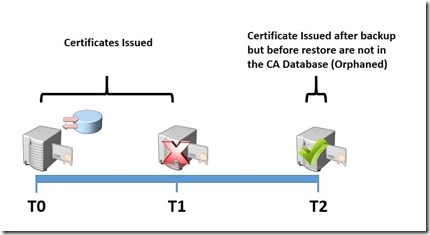
Orphaned certificates are certificates that are issued by a Certification Authority, but after issuing the certificates the Certification Authority has no knowledge of the certificates. This situation most commonly occurs after the restore of a Certification Authority.
is illustrated in the graphic below. In this example the CA is backed up at Time 0. After the backup the CA issues certificates. At Time 1 the CA fails. At Time 2 the CA is recovered from the backup taken at Time 0. The problem here is that after the restore there is no record of certificates issued after the backup, but before the restore. These are known as orphaned certificates. The problem with orphaned certificates is that they are valid, but you have no record of issuing them. And if you have no record of issuing them, you have no way to revoke them if necessary. However, if you have the SMTP module running, you have a list of certificates issued during this time. And although going through a mailbox to determine what certificates you have issued is not the most convenient way to do determine this, at least you have a record. You can also use the information in the email of issued certificates, specifically the Serial Number to revoke these certificates if necessary.
Revoking Orphaned Certificates: A Walkthrough
The steps for revoking the orphaned certificate is to:
- Determine the Serial Number of the orphaned certificate
- Create a certificate with that same Serial Number
- Import that certificate into the CA Database
- Revoke that certificate
- Publish a new CRL
Below is a walkthrough or revoking expired certificates.
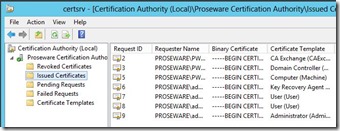
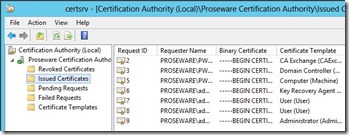
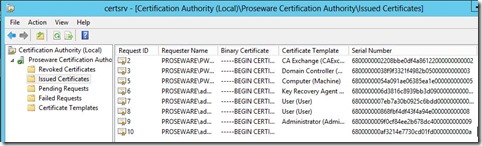
On my Certification Authority I have issued a total of 7 certificates under Issued Certificates.
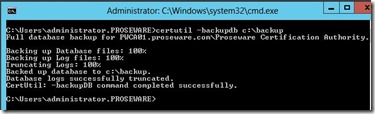
I then backup the CA Database
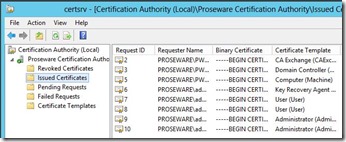
I then requested an a certificate from the CA. I now have a total of 8 certificates listed under Issued Certificates.
After requesting the certificate I restored the CA Database. As you can see in the screenshot, I am missing the certificate that was issued after the backup.
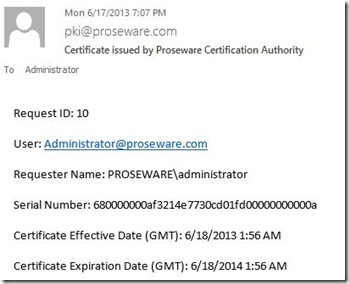
Since, I have the SMTP Exit Module installed on the CA, I know I have a record of the certificate that I issued. So, I check my email to find the serial number of the certificate.
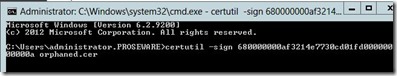
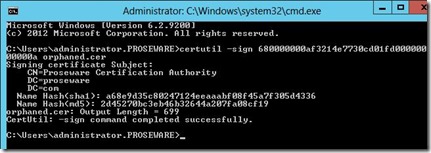
So, next I want to create a certificate with the same serial number. So, I run the following command on the Certification Authority that issued the original certificate:
“certutil –sign <SerialNumber> <CertificateName>” Where <SerialNumber> is the serial number of the original certificate and <CertificateName> is the name I wish to give the certificate.
I then get prompted for the certificate (Private Key) I want to use to sign the certificate with. I choose the CA certificate, and click OK.
After I select the certificate my command completes successfully, as seen below.
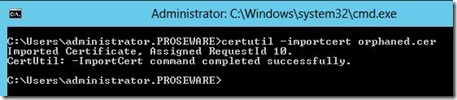
Next, I want to import the certificate into the CA’s Database. To do this I run the following command:
“certutil –importcert <CertName>”, where <CertName> is the name of the certificate I created in the previous steps.
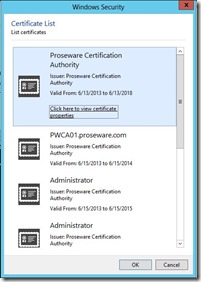
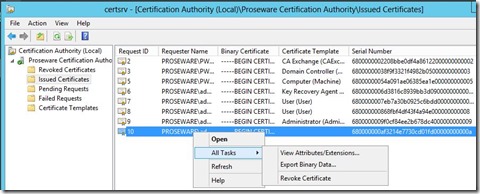
As, we see in the screenshot below I now have an additional certificate in Issued Certificates with the serial number of the orphaned certificate.
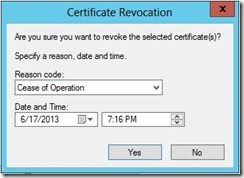
I then right click on that certificate, select All Tasks, then Revoke Certificate
I choose a reason for the revocation, and click OK.
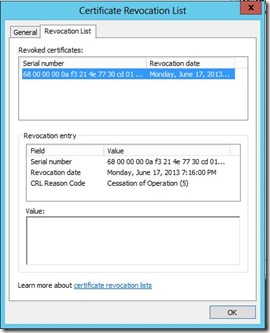
Next I can run “certutil –crl” on the CA to force the publication of a new CRL. And as you see in the screenshot below the “orphaned” certificate is included in the Revocation List.
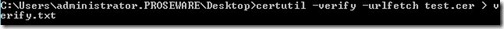
If I want to verify the certificate is showing as revoked to clients I can run “certutil –verify –urlfetch <CertName> > <OutputFileName>” to check validation for the certificate.
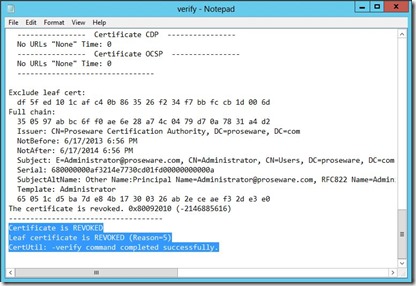
And when I review the output, I see the certificate is showing as revoked.
Summary
In the steps above, I covered how to revoke orphaned certificates. It is important to note that you have to have some way to keep track of issued certificates in order to be able to do this. I have used the SMTP Exit Module to track issued certificates.
-Chris




Comments: