| Original URL: | https://blogs.technet.microsoft.com/xdot509/2011/07/06/autoenrollment-for-offline-certificate-templates/ |
| Post name: | Autoenrollment for Offline Certificate Templates |
| Original author: | chdelay |
| Posting date: | 2011-07-06T08:06:00+00:00 |
One headache for System Administrators has been renewing certificates generated from Offline Templates. Relief from this arduous task is available in Windows Server 2008 R2.
Certificate Templates that are configured so that the requestor must provide the identity in the request are called "Offline" Certificate Templates. And one of the disadvantages to “Offline” Certificate Templates is that they could not be used with Autoenrollment.
If you take a look at the subject tab of a Version 2 or Version 3 Certificate Template you will notice two settings. The first setting is Supply in the request. The second setting isBuild from this Active Directory information. To enable auto enrollment this second setting must be configured on the Certificate Template. And it makes sense. If you are going to be automatically provisioning certificates you would need to pull the identity information from somewhere, in order to determine what the Subject or Subject Alternative Name (SAN) for a certificate would be. And that is exactly what the Certification Authority does for auto enrolled certificates.
However, in some instances it is necessary for an Administrator to provide this information. For example you have a Web Server whose identity is web01.contoso.com. The web server hosts web portal for a company called contosoweb.contoso.com. Since there is no automated way for the CA to determine that the web servers identity is Contosoweb as well as Web01, that information must be supplied in the request by the Administrator.
Autoenrollment is a feature that performs many actions for a client. One of the two key features in terms of enrollment is the ability to automatically provision certificates to clients. The second is the ability to automatically renew certificates without user or administrator intervention.
Prior to Windows Server 2008 R2, neither of these two features could be utilized with certificates generated from Offline Certificate Templates. This meant that not only did Administrators need to manually request a certificate, but they needed to manually renew them as well. This meant that if Administrators did not remember to renew the certificate before it expired, it would of course expire, causing certificate validation to fail. In the case of a web server protected by SSL, the client would not be able to validate the certificate, resulting in the failure to access the website via SSL.
However, beginning with Windows Server 2008 R2, it is now possible to automatically renew certificates have been generated from “Offline” Certificate Templates. Another way to describe this is that certificates with user defined Subjects or Subject Alternative Names (SAN) can be renewed via Autoenrollment. This does of course mean that the first certificate must be manually enrolled for, and subsequent renewals can be completed by Autoenrollment.
So what are the requirements in order to get this to work? First the issuing CA must be Windows Server 2008 R2. Second, the client that will be performing Autoenrollment must be Windows 7 or Windows 2008 R2.
The steps to configure Autoenrollment for Offline Certificate Templates are the following:
- Configuring Autoenrollment Group Policy *If you do not already have the Autoenrollment GPO configured in your environment
- Configure Certificate Templates
- Manually Requesting a Certificate
Configuring Autoenrollment Group Policy
We are going to use Autoenrollment to do the automatic renewals of certificates, so we must first enable auto enrollment.
Autoenrollment in almost all instances be configured at the domain level so that it applies to all Computers in that domain.
1. First you will need to open GPMC.MSC
2. Navigate to an existing domain wide Group Policy or Create a new one
3. Now open that Group Policy for editing
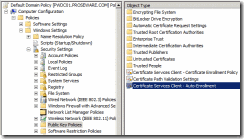
4. Navigate to \Computer Configuration\Windows Settings\Security Settings\Public Key Policies\ and open the setting called Certificate Services Client – Auto-Enrollment as illustrated in Figure 1.
Figure 1
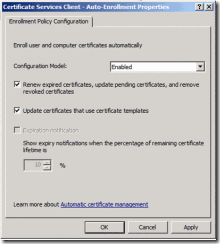
5. Once you have the setting open, ensure that is configured to be Enabled
6. Also, ensure that both Renew expired certificates, update pending certificates, and remove revoked certificates and Update certificates that use certificate templates, are enabled (checked).
7. Click OK when finished.
Figure 2
Configure Certificate Templates
In this example we will be creating a Certificate Templates, whose purpose is Server Authentication. In order to create the Certificate Template, we will duplicate an existing Certificate Template. Then we will modify the Subject Name properties of the Certificate Template. Finally, we will adjust the security permissions on the Certificate Template.
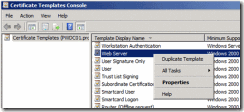
1. Open the Certificate Templates MMC (certtmpl.msc)
2. Right-click on the Web Server template
3. And select Duplicate Template from the context menu
Figure 3
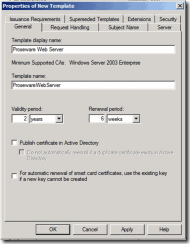
4. Give the template a name. In my example (Figure 4), I used the name Proseware Web Server.
Figure 4
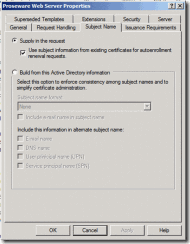
5. Next select the Subject Name tab
6. Verify that Supply in the request is selected
7. Also, verify that Use subject information from existing certificates for autoenrollment renewal requests is selected
Figure 5
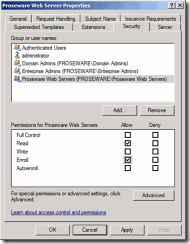
8. Next, go to the Security tab
9. Add any security principals that you would like to be able to enroll for a certificate, based off this template
10. Give those security principals Read and Enroll permissions, so that they can enroll for certificates *To ease management, those machines for which you wish to enable enrollment should be added to a security group. You can then provision permissions to that Security Group on the Certificate Template.
Figure 6
Manually Requesting a Certificate
The first request for the certificate must be done manually, since we are supplying the subject in the request. Since Autoenrollment is enabled, and the certificate template was configured properly, subsequent renewals will be done through Autoenrollment. In this example, I will be requesting a certificate through the Certificates MMC.
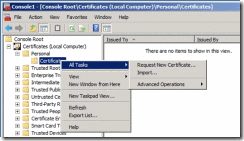
1. Open the Certificates MMC, targeted to the local machine
2. Right Click on either the Personal node, or the Personal\Certificates node
3. Select All Tasks, then Request New Certificate…, from the context menu
Figure 7
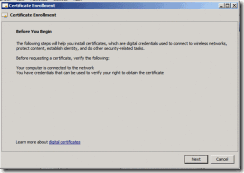
4. This will open the Certificate Enrollment wizard, click Next
Figure 8
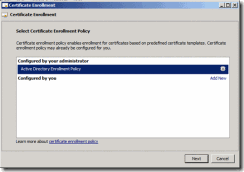
5. On the Select Certificate Enrollment Policy of the wizard, click Next
Figure 9
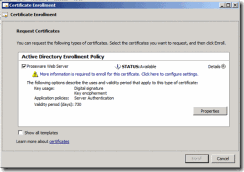
6. Select (checkbox) the desired “Offline” Certificate Template, then click the Details button. In my example this is Proseware Web Server Certificate Template that I created earlier.
7. Then click the Properties button
Figure 10
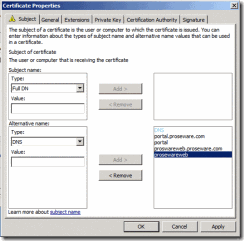
8. On the Subject tab you can fill out the desired Subject and/or Subject Alternative Names. In my example, I chose DNS name as the type, and entered the desired names.
Figure 11
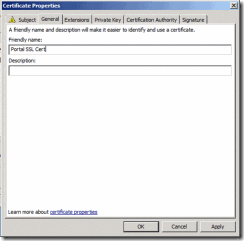
9. Fill out any additional information you would like to include in the request. In my example, I added a friendly name so that I can easily locate the certificate in the Certificates MMC.
10. When finished click OK
Figure 12
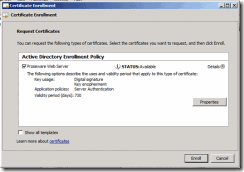
11. On the Request Certificates page of the wizard, click Enroll
Figure 13
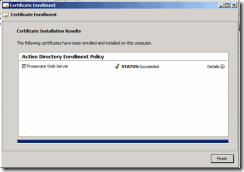
12. When the enrollment completes, click Finish
Figure 14
Conclusion
This completes the entire process for enabling Autoenrollment for certificate renewals of certificates based on “Offline” Certificate Templates. In this article, I configured the Autoenrollment GPO, configured the Certificate Template, and manually requested a certificate based on that template. Autoenrollment will now automatically renew the certificate that I manually enrolled for.




Comments: