| Original URL: | https://blogs.technet.microsoft.com/pki/2012/07/13/blocking-rsa-keys-less-than-1024-bits-part-2/ |
| Post name: | Blocking RSA Keys less than 1024 bits (part 2) |
| Original author: | Kurt L Hudson MSFT |
| Posting date: | 2012-07-13T14:14:00+00:00 |
OnAugust 14, 2012, Microsoftwillissue a critical non-security update(KB 2661254) for Windows XP, Windows Server 2003, Windows Server 2003 R2, Windows Vista, Windows Server 2008, Windows 7, and Windows Server 2008 R2. The update will block the use of cryptographic keys that are less than 1024 bits. This update was first announced in the blog titled RSA keys under 1024 bits are blocked. This blog post is a reminder that the update is coming and provides a bit more information on how to control the updatewhen deployed.
Note:The modification (opt-out settings) discussed in this article will applythroughout the operating system. You cannot configure these modifications to be applicable to a specific application, custom certificate, or scenario. You can configure thesemodificationsbefore the update is applied and when the update is applied, they will take effect. The update will require a restart.
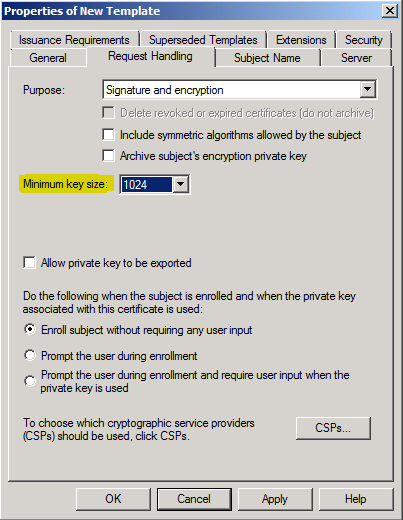
You can modify a registry setting using the certutil command to modifythe size of the keys thatareblocked. For example, if you wanted to allow 512 bit keys, but block all keys less than 512 bits, you could run the following command:
Certutil -setreg chain\minRSAPubKeyBitLength 512
Note: All certutil commands shown in this article require local Administratorprivilegesbecause they are modifiying the registry. You can disregard the message that reads "The CertSvc service may need to be restarted for changes to take effect." That is not required for these commands as they do not affect the certificate service (CertSvc).
If only the root certificate in a chain is 512 bits, but all the rest of the keys below are 1024 bits or higher, you could run the following command to indicate that you will allow a 512 bit root certificate, but want to block all keys less than 1024 bits below the root certificate.
Certutil -setreg chain\EnableWeakSignatureFlags 2
Note: The above command also works with self-signed certificates with RSA keys less than 1024.
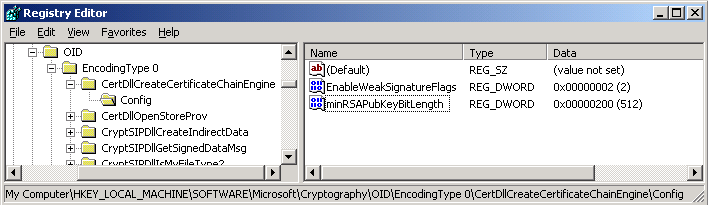
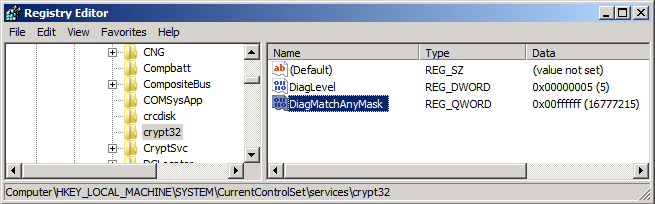
The certutil commands shown in this posting will not work on Windows XP, Windows Server 2003, or Windows Server 2003 R2. You will have to modify the registry directly using regedit.exe or reg command. Registry path: HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Cryptography\OID\EncodingType 0\CertDllCreateCertificateChainEngine\Config. The following table and figure illustrate registry the settings shown in the previous two examples:
| Name | Type | Decimal data |
| EnableWeakSignatureFlags | REG_DWORD | 2 |
| minRSAPubKeyBitLength | REG_DWORD | 512 |
If you have Authenticode signatures that were signed with keys less than 1024 bits prior to January 1, 2010, 12:00:00 AM UTC/GMT, they will not be blocked by default. If necessary, you can use the WeakRsaPubKeyTime setting to allow for the configuration of the date and time for which to consider older signatures valid. If you have reason to set a different date and time for the WeakRsaPubKeyTime, you can use certutil to set a different date and time. For example, if you wanted to set the date to August 29, 2010, you could use the following command:
certutil -setreg chain\WeakRsaPubKeyTime @08/29/2010
If you have a need to set a specific time, such as 6:00 PM UTC/GMT on July 4, 2011, then add the number of days and hours in the format +[dd:hh] to the command. Since 6:00 PM is 18 hours after midnight on July 4, 2011, you would run the following command:
certutil -setreg chain\WeakRsaPubKeyTime @07/04/2011+00:18
To enterWeakRsaPubKeyTimeand date on Windows XP, WindowsServer 2003, or Windows Server 2003 R2, use a REG_BINARY value for WeakRsaPubKeyTime.You canfigure out the hex value using certutil on Windows Vista, Windows Server 2008, ormore recentWindows operating system and then view the value in the registry or export the value to a REG file for viewing. The following table shows REG_BINARYhex value equivalents for WeakRsaPubKeyTime
| Date/Time | Hex value |
| August 29, 2010at midnight UTC\GMT | 00 d8 f0 cb 47 47 cb 01 |
| July4, 2011at 6 PM UTC\GMT | 00 e8 64 dd ae 3a cc 01 |
Additional resources
Security advisory http://technet.microsoft.com/security/advisory/2661254.
KB 2661254: http://support.microsoft.com/kb/2661254
Additional blog posts:
RSA keys under 1024 bits are blocked
https://www.sysadmins.lv/retired-msft-blogs/pki/blocking-rsa-keys-less-than-1024-bits-part-3.aspx