Windows Vista and Windows Server 2008 have a convenient user interface to create custom certificate requests. This is especially helpful since computer certificate enrollment through the web enrollment pages was discontinued from Windows Server 2008 and on.
If you want to create a custom certificate request, perform the following steps:
1. Start the Certificates MMC snap-in and expand the Personal – Certificates container in the left pane.
2. Right click the Certificates container and chose Create custom request from the context menu.
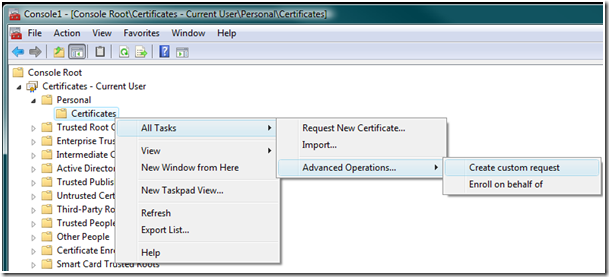
3. Click Next to accept the welcome page of the wizard.
4. If you have Enterprise CA connectivity in your Active Directory forest, you can chose from a list of available certificate templates and create the request based on a specific certificate template. If you want to be independent of any certificate template, select (No template) CNG key if the application can handle CNG keys. Else select the (No Template) Legacy Key instead. For more information on Cryptography Next Generation (CNG), see the documentation on MSDN. Click Next to continue.
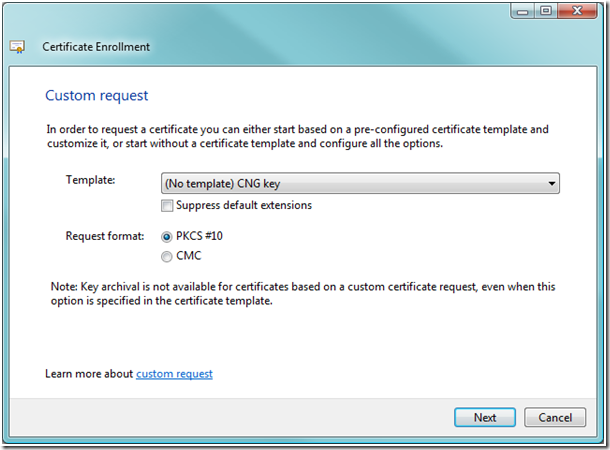
5. To customize your certificate request click the little arrow next to the word Details in the Certificate Enrollment page.
6. Click the Properties button.
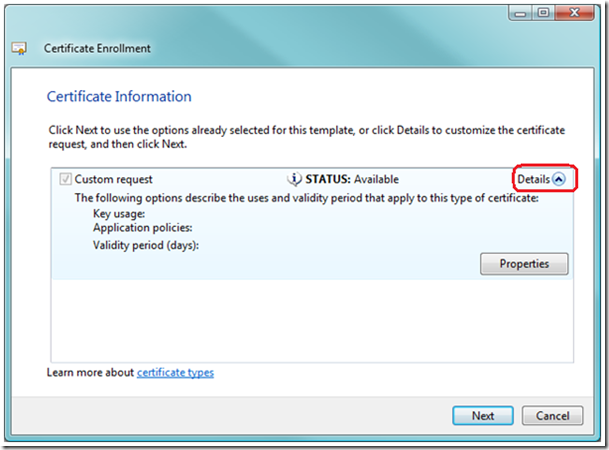
7. Use the dialog tabs to define the certificate properties.
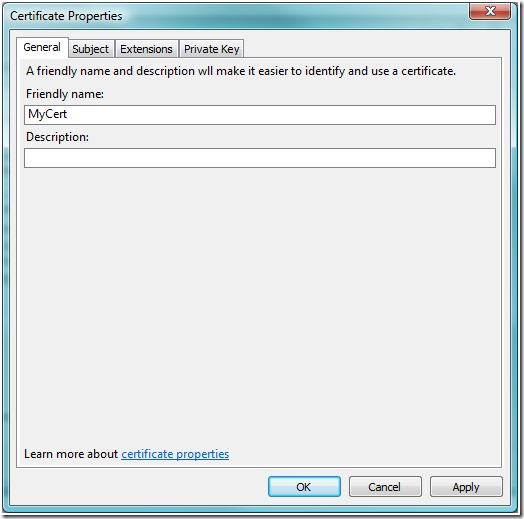
8. After defining all certificate attributes, click OK.
9. Finally, specify a filename to save the offline certificate request and click Finish.
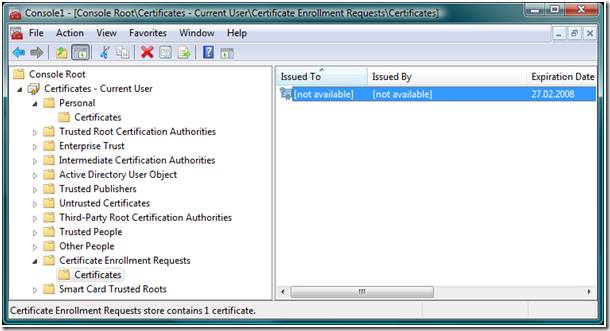
10. The pending certificate request appears in the Certificate Enrollment Requests container in the Certificates MMC snap-in until the offline request was accepted.
11. To verify the certificate request, double-click the pending request in the MMC snap-in. Alternatively use certutil [mycert.req] at a command-line where [mycert.req] is equal to the file that you saved in step 9.
12. To enroll for the certificate request, submit the request with certreq –submit. If no certificate template was selected in the wizard, it is required to specify one as command-line parameter. Also don’t forget the –config parameter to specify the name of the certification authority where you are enrolling from. The certreq command might look like the following example if the CA is accessible via DCOM:
certreq –config "myCAserver\myCAname" –submit –attrib "CertificateTemplate:User" mycert.req
If certreq is executed on a computer running Windows 7 or Windows Server 2008 R2, the following command leverages the new web enrollment protocol on a Windows Server 2008 R2 CA where DCOM access to the CA is not mandatory. The URL provided with the config command is configured at the CA and can be found out with the certutil -dump command:
certreq –config https://www.contoso.com/My-CES/service.svc/CEP –submit –attrib "CertificateTemplate:User" mycert.req
If the CA is only accessible via the web enrollment pages, you have to open the mycert.req file with Notepad and copy/paste it into the web enrollment pages.
13. To install the certificate once it was enrolled, accept the certificate. This will also remove the pending certificate request from the Certificate Enrollment Requests container. Use certreq -accept [certificatename.cer] to accept the certificate request.









