Hey Everyone, I am back with part 2 of this 3 part series on TPM protected certificates. The topics covered in this are related to Virtual Smart Cards, their benefits, and lastly their limitations. I will also cover how to create a Virtual Smart Cards. Management of certificates contained on the virtual smart card are similar to those of a traditional smart card are not covered in this article.
Virtual Smart Cards function very similarly to conventional Smart Cards. The difference is the private key is protected by the TPM and not the smart card media. The Virtual smart card emulates a smart card and reader so the device presents itself to operating system and applications as a traditional smart card. As for the storage of the private key, this is handled similarly to that of a key protected by the Microsoft Platform Crypto Provider. The private key is encrypted and stored on the file system.
Virtual Smart Cards offer the following similarities with traditional Smart Cards.
Non-Exportability: Since the private key is encrypted by the TPM is cannot be used on any other device.
Anti-Hammering: The TPM will lockout if a pin is entered incorrectly too many times. This behavior is manufacturer specific.
Key Isolation: Private keys protected by the TPM are never exposed to the operating system or malware. All private key operations are handled within the TPM.
For more information see the following related article:
TPM Fundamentals - http://technet.microsoft.com/en-us/library/jj889441.aspx
Lab Configuration
Assumptions
This article assumes the individual has a basic understanding of Microsoft PKI and its components.
Prerequisites
•A domain controller running Windows Server 2003 or later*
•An enterprise certificate authority running Windows Server 2012 R2
•A desktop or laptop with a configured TPM, running Windows 8.1
*In order to process Smart Card logons. Domain Controllers must obtain a certificate based on the Domain Controller Authentication certificate template.
Virtual Smart Card Creation
In this section we will create a virtual smart card on the Windows 8.1 laptop or laptop. Creating a virtual smartcard is not a difficult task however there are a few ways of doing it. The easiest method is using the command line utility TPMVSCMGR.EXE.
To create a virtual smartcard from the command line use the following command. Note: You must have admin rights on the host and the command line must be (run as admin).
Tpmvscmgr.exe create /name “TestVirtualSC” /pin prompt /adminkey default /generate
You should be prompted to enter a pin, enter a pin of your choosing then re-enter it to confirm.
Before we go further let’s take note of what this will actually do.
Create: This is pretty self-explanatory. We are creating a virtual smartcard here.
/name: This is the name that will be given to the device you will see in Device Manager (see below)
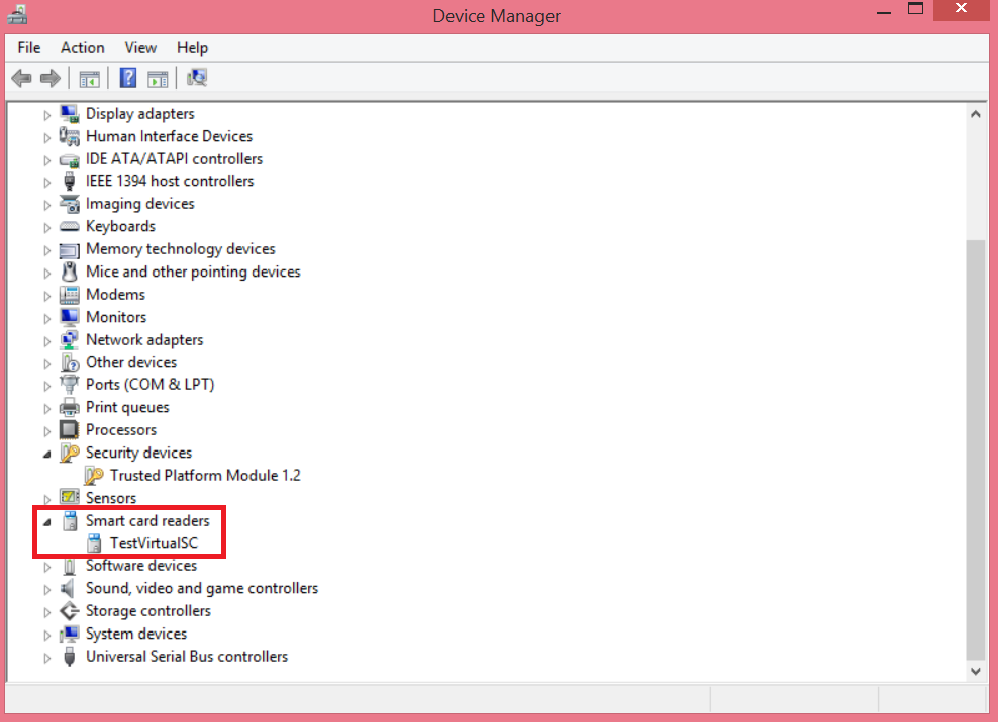
/pin: This is the pin that unlocks the virtual smart card. Similar to physical smartcard but protected by the TPM anti-hammering feature.
/adminkey: the admin key that you are assigning to the virtual smart card. Admin keys are used for management purposes.
After the virtual smartcard creation it can be treated just like a traditional smart card by using the “Microsoft Base Smart Card Crypto Provider” or “Microsoft Smart Card Key Storage Provider”.
Smart Card Logon Certificate Template
In this section we will create the certificate template to be used for smartcard logon. This template will be configured to leverage the “Microsoft Smart Card Key Storage Provider”. So unless a physical or Virtual Smart Card is present the user will not be able to enroll for this type of certificate. Before we get started I want to note a few things.
-
Creating this template will require Enterprise Admin rights unless you have delegated access to the templates by using one of the steps defined in this article: http://technet.microsoft.com/en-us/library/cc725621(v=WS.10).aspx
-
The template settings defined here should not be used in a production environment. Obtaining a certificate that can be used for smart card logon should not be easy. Processes should be put into place to ensure these types of certificates are procured in a secure manner (Issuance Policies), especially if they are to be used for non-repudiation. See the last section in this document “Further Considerations” for more info.
Now that this stuff is out of the way…
From the Enterprise Certificate Authority.
-
Open the Certificate Templates Console - certtmpl.msc,
-
Duplicate the Smartcard Logon certificate templates
-
On the Compatibility tab set the Certificate Authority to Windows Server 2012 and Certificate recipient to Windows 8.1/Windows Server 2012 R2
*Note: Windows 8.1 and Windows Server 2012 R2 are only required for key attestation. We will reuse this template in part 3 for this purpose. If your CA and client are Windows 8 and Windows Server 2012 you can still complete this exercise. If this is the case simply choose Windows 8/Windows Server 2012 in the compatibility settings.
- Click on the General Tab and give the template a name.
-
Click on the Cryptography tab
-
Click Apply and OK.
-
Open the Certificate Authority MMC – certsrv.msc
-
Right click on the Certificate Templates container and select new, certificate template to issue.
-
Click on the certificate template you created and click OK.
Enrolling for a Smart Card Logon Certificate
After your Virtual Smart Card and Smart Card Logon Template has been created now we are ready to enroll for a certificate.
That’s it. We now have a Virtual Smart Card and a certificate for Smart Card Logon. We are ready to use it to log in.
Logging In/User Experience
Before I get started on the next section. Sorry for the low res pictures ??
Now what we have everything we need to log in. What will your users see? Users will see the familiar interface but there will be a new link below: Sign-in options
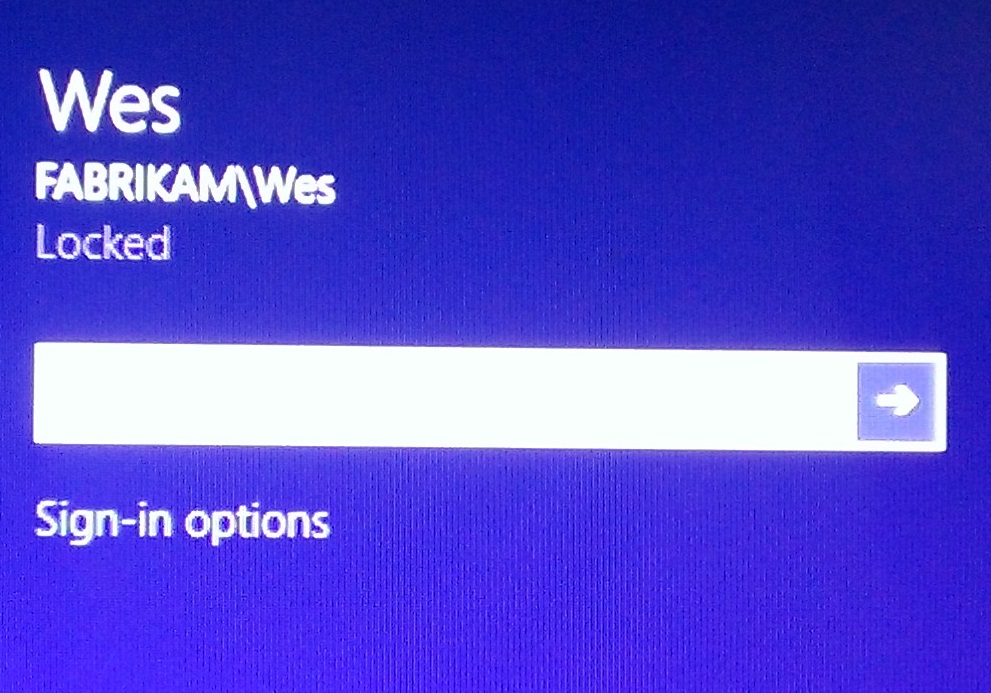
Clicking on Sign-in options reveals the following.
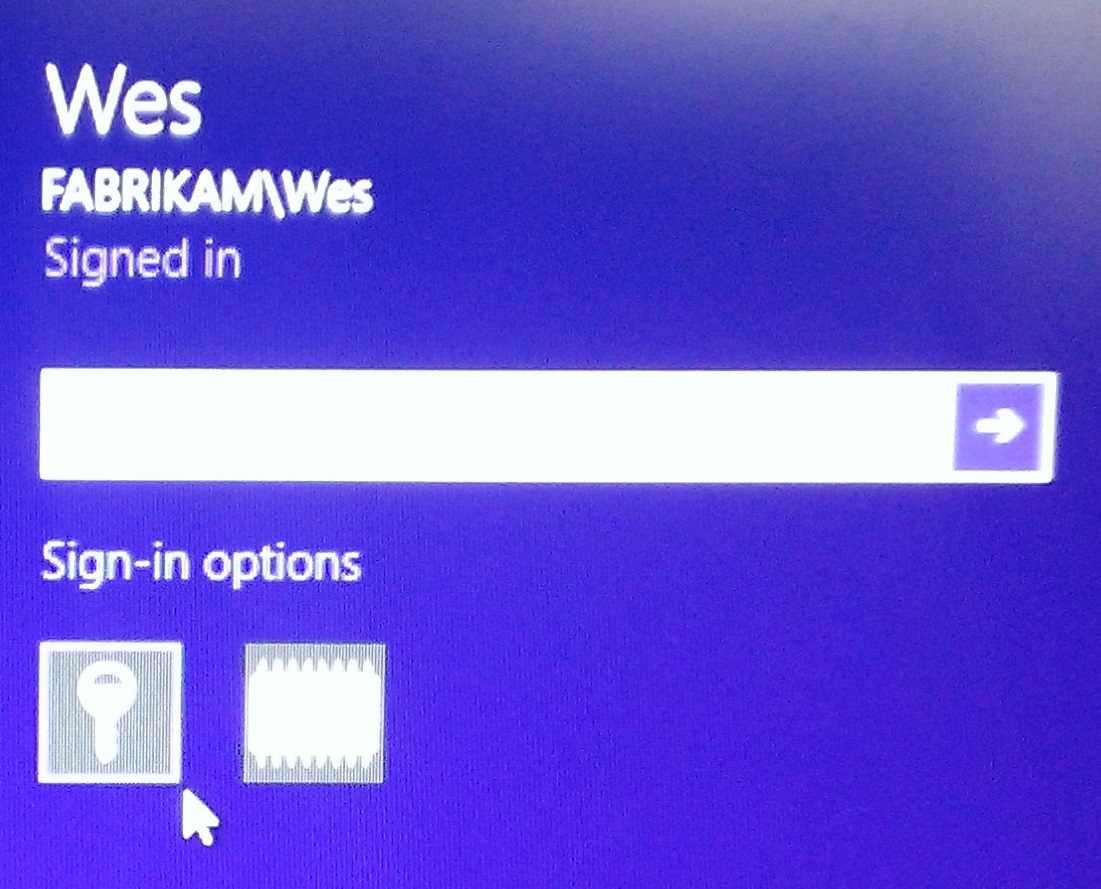
The first is the icon that looks like a key, this is the username/password option. Do I need to explain this any further? I hope not.
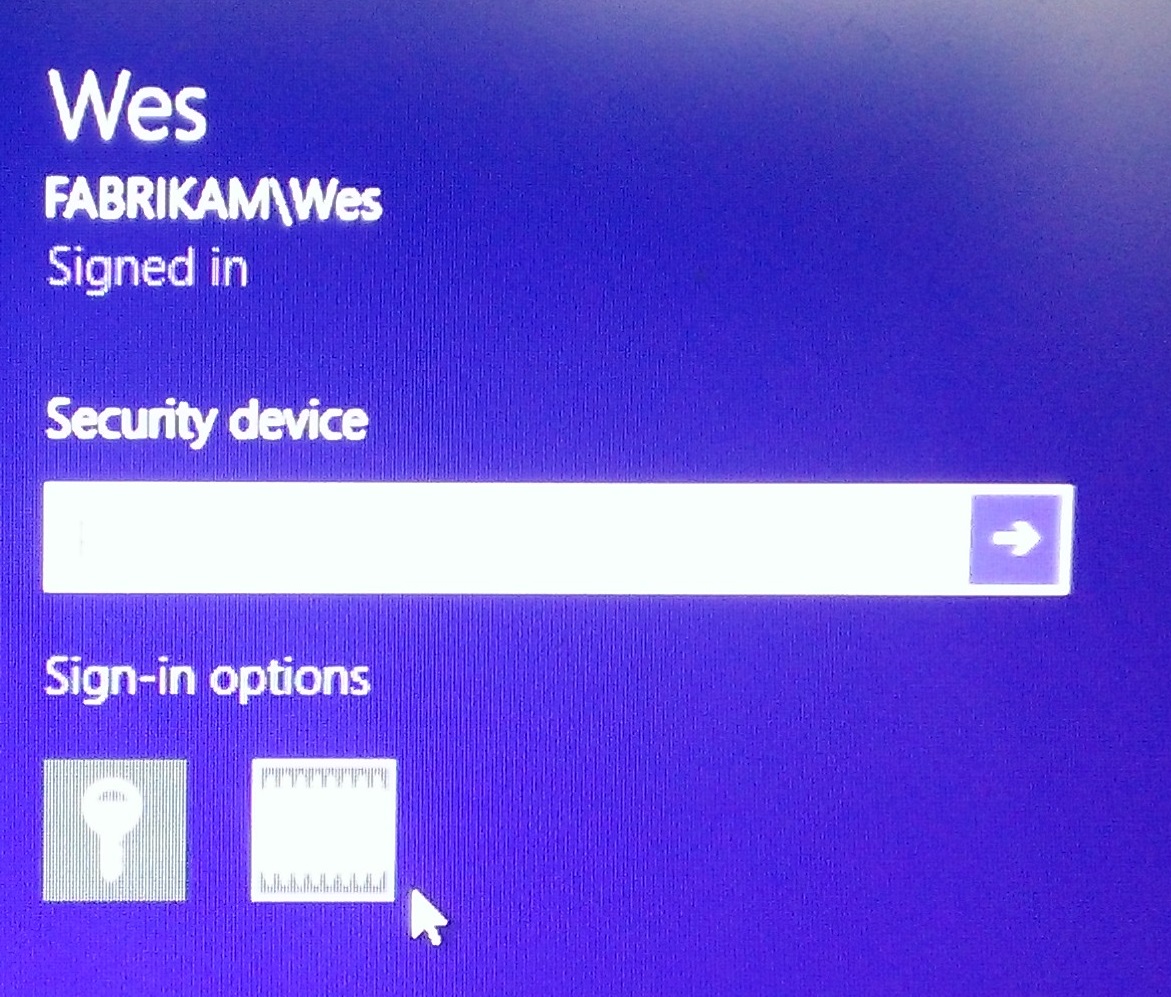
This is the one we are interested in. The icon that looks like an IC or chip. Clicking on this changes the box above to state “Security Device” and the place you would typically put your password says PIN now. Hmmm…… where did I see that PIN before, oh yeah when we created the Virtual Smart Card. I hope you remember what you set it to. Enter the PIN you used when you created the Virtual Smart Card. Viola! Smart Card Logon.
Changing Virtual Smart Card PIN
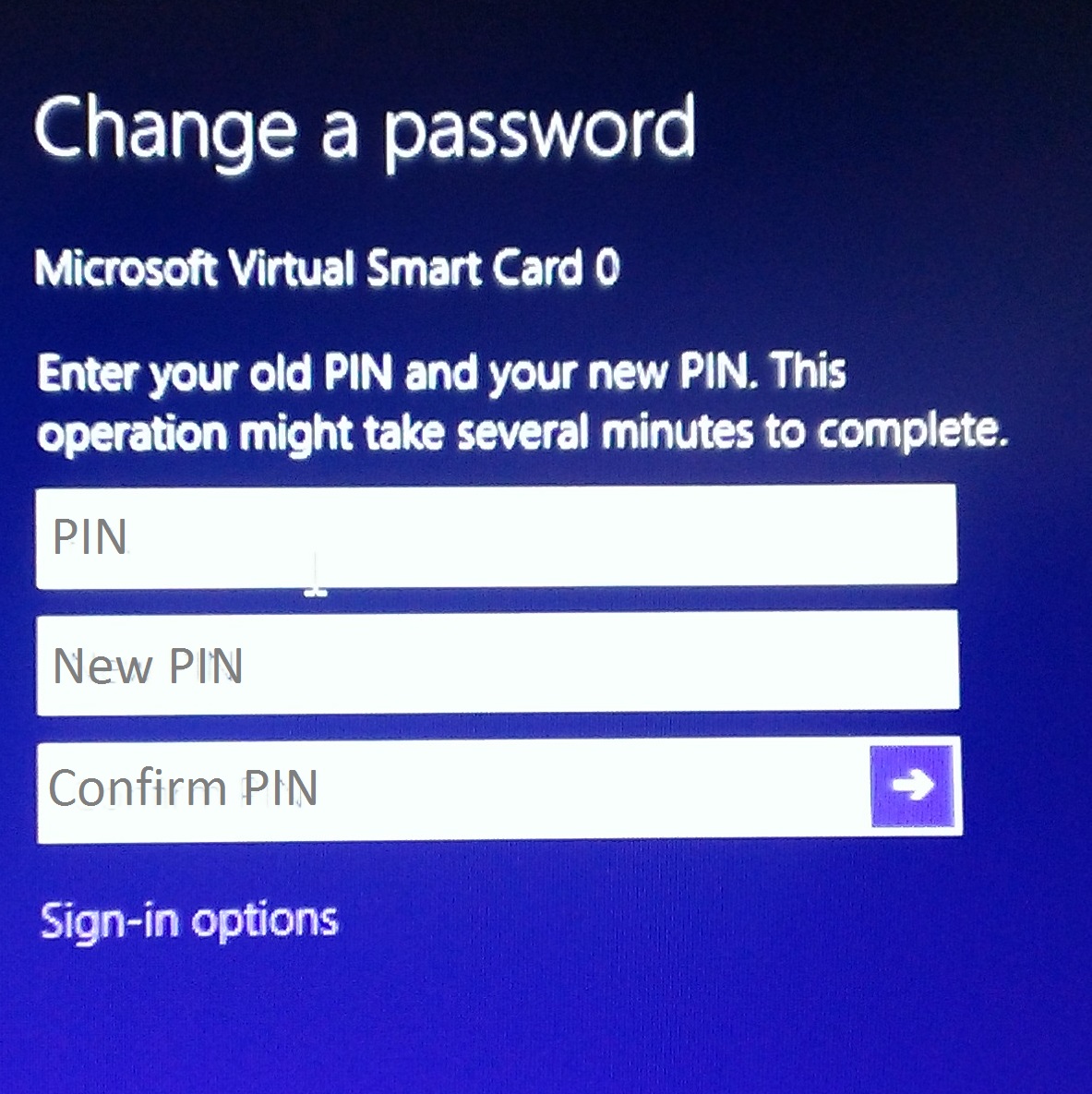
In this last section I will show you how to change a PIN for a Virtual Smart Card.
While logged in using the Virtual Smart Card press Ctrl+Alt+Del and select the option to “Change a password”. Enter the old PIN, the new PIN then confirm. That’s it.
Further Considerations
Issuance Policy/Enrollment Requirements
It is important to give consideration as to why you are implementing Virtual Smart Cards. Most organizations choose to issue Smart Cards or Virtual Smart Cards to strengthen security. Smart card logon achieves this by requiring the user to have their physical smart card and the associated PIN in order to logon. Virtual Smart Cards are very similar. The user must have the TPM enabled device, and know the PIN.
Additional considerations should be given for enrollment for a virtual smart card. Much as that of traditional Smart Cards a username and password should not be the only factor to obtain one. Your organization may determine that someone needs to enroll in person and/or provide positive ID, fill out forms or other requirements.
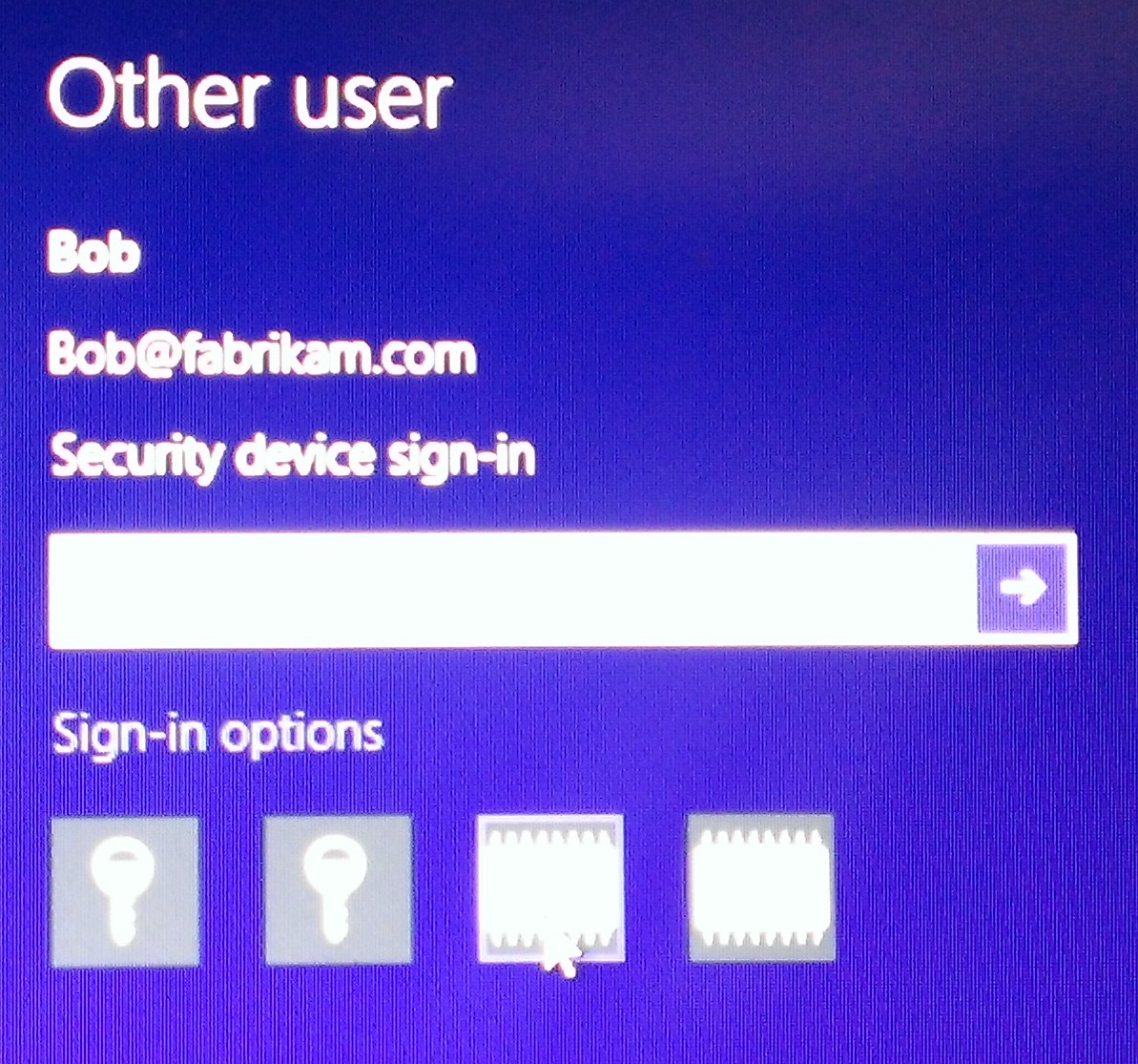
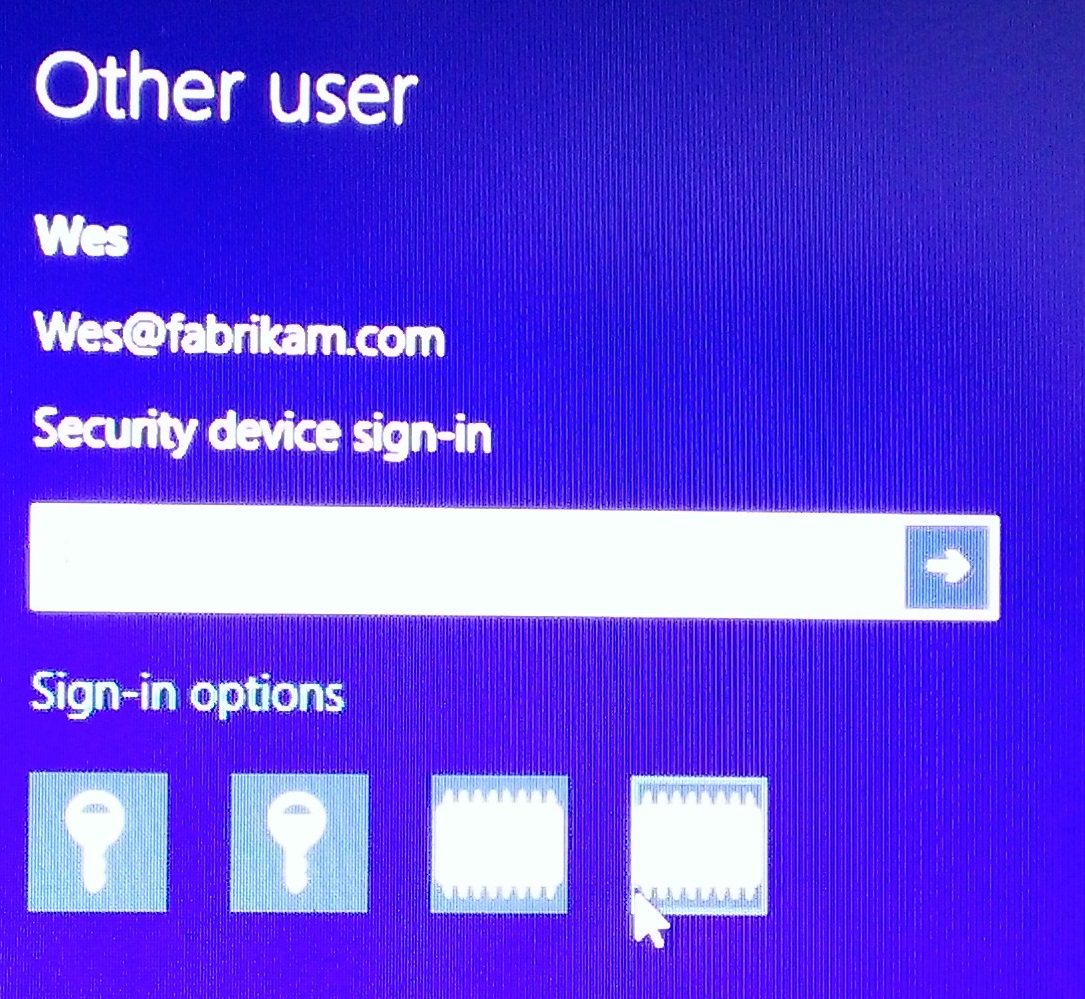
Shared Devices/Computers
It is possible to have more than one Virtual Smart Card on a device. If you do have a requirement to have more than one the interface presents similar to what you see here:
User 1: Bob
User 2: Wes
I hope you all enjoyed this post on Virtual Smart Cards and I hope it assists you in your evaluation of this security related feature. Again, this is part 2 of a 3 part series regarding protecting certificate private keys using Trusted Platform Modules. I’ll be back really soon with part 3, Key Attestation in Windows Server 2012 R2 and Windows 8.1.
Technical Resources:
Understanding and Evaluating Virtual Smart Cards - http://technet.microsoft.com/en-us/library/dn578507.aspx
TPM Platform Crypto-Provider Toolkit - http://research.microsoft.com/en-us/downloads/74c45746-24ad-4cb7-ba4b-0c6df2f92d5d/default.aspx