Historical Content Alert
This is a historical content for Windows NT 4.0 product and is presented for informative purposes only. All content in this directory is copyrighted and owned by Microsoft.Data Encryption
In using data encryption, a plaintext message can be scrambled to appear like random gibberish and be difficult to unscramble without a secret key. Here the term message refers to any piece of data designated for encryption. This message can be ASCII text, a database file, or any data designated for secure transmission. Plaintext refers to data that has not been encrypted, while ciphertext refers to data that is encrypted.
After a message has been encrypted, it can be stored on nonsecure media or transmitted on a nonsecure network, and still remain secret. Later, the message can be decrypted into its original form. This process is shown in the following illustration.
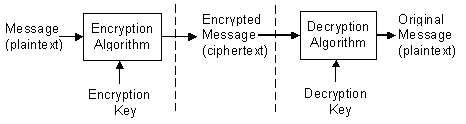
When a message is encrypted, an encryption key is used. This is analogous to a key used to lock a padlock. To decrypt the message, the corresponding decryption key must be used. It is very important to properly restrict access to the decryption key, because anyone who possesses it will be able to decrypt all messages that were encrypted with the matching encryption key.
Symmetric algorithms are the most common type of encryption algorithm. Symmetric algorithms use the same key for both encryption and decryption. In order to communicate using symmetric algorithms, both parties must share a secret key.
Public-key (asymmetric) algorithms use two different keys: a public key and a private key. The private key is kept private to the owner of the key pair, and the public key can be distributed to anyone who requests it (often through a certificate. If one key is used to encrypt a message, then the other key is required to decrypt the message.
Symmetric algorithms are much faster than public-key algorithms and are essential for encryption of large amounts of data. However, because the keys must remain secret, distribution of the keys to large numbers of people is not practical. Public-key algorithms solve this problem and can be used in conjunction with symmetric algorithms to achieve optimal performance when large amounts of data are involved.



